Mutual Aid: Difference between revisions
| (18 intermediate revisions by 4 users not shown) | |||
| Line 1: | Line 1: | ||
{{Ilawsidebar}} | |||
==Overview== | ==Overview== | ||
'''Thursday, 5:00-6:00pm'''<br> | |||
''Lead: Jonathan Zittrain'' | |||
Building upon key themes related to cybersecurity and the role of the private sector in ensuring persistent, secure, and consistently available content on the web, this session will focus on possible responses to the current state of computer and network security. Drawing conceptually from mutual aid treaties among states in the real world, Jonathan Zittrain will outline a defense scheme that would seek to make the current decentralized Web a more robust one. His" mirror as you link" system of assistance reimagines the technological relationships between sites and services on the Web, and envisions a new socially- and technologically-based system of redundancy and security. "Today, if one clicks on a link to an external site and that site is unavailable – perhaps attacked with a classic denial-of-service – there is no alternative to accessing it. Mirror-as-you-link would change that. Participating Web server administrators could make it so that for some or all of the links to external sites that they offer on their pages, the contents of the faraway sites would be saved (“cached”). They would do this only for sites that wish it to be done, and then only for sites that also perform such mirroring themselves. Then, when one site goes down, a Web surfer clicking on a link to get there can return to the referring site and ask for a copy of whatever he or she is missing since the destination site is down." | |||
==Required Readings== | ==Required Readings== | ||
*The Harvard International Law Journal, [http://opiniojuris.org/2011/07/13/hilj-zittrain-responds-to-hollis/ "Jonathan Zittrain responds to Duncan Hollis"], July | *The Harvard International Law Journal, [http://opiniojuris.org/2011/07/13/hilj-zittrain-responds-to-hollis/ "Jonathan Zittrain responds to Duncan Hollis"], July 2011. | ||
*Jonathan Zittrain, [http://www.techpolicy.com/Blog/January-2010/Consider-This--A-Mutual-Aid-Treaty-for-the-Interne.aspx "Consider This: A Mutual Aid Treaty for the Internet"], January | *Jonathan Zittrain, [http://www.techpolicy.com/Blog/January-2010/Consider-This--A-Mutual-Aid-Treaty-for-the-Interne.aspx "Consider This: A Mutual Aid Treaty for the Internet"], January 2010. | ||
*Jonathan Zittrain, [http://ir.lawnet.fordham.edu/flr/vol78/iss6/3 "The Fourth Quadrant"], 78 Fordham L. Rev. 2767, January | *Jonathan Zittrain, [http://ir.lawnet.fordham.edu/flr/vol78/iss6/3 "The Fourth Quadrant"], 78 Fordham L. Rev. 2767, January 2010. | ||
==Recommended Readings== | ==Recommended Readings== | ||
*Jonathan Zittrain, [http://www.brookings.edu/papers/2011/0127_internet_treaty_zittrain.aspx "A Mutual Aid Treaty for the Net"], 8 The Future of the Constitution Series, The Brookings Institution, January 27, 2011. (also available in [http://www.brookings.edu/~/media/Files/rc/papers/2011/0127_internet_treaty_zittrain/0127_internet_treaty_zittrain.pdf PDF]) | |||
==Student Reflections== | |||
This panel delved deeper into the cost and benefit analysis of solutions to previously mentioned cyber security problems. Such problems include dealing with networks that are difficult to control and resolve. Jonathan Zittrain categorized these problems into a quadrant chart dependant on the level of direct people participation in resolving these cyber security problems. | |||
[[Image:JZ_quadrant.png|border|center]] | |||
In discussing the different types of solutions, Zittrain showed how each solution followed the pattern of a generative dilemma presented by the nature of the internet: openness->abuse->lockdown. He asked whether the real problem is not the solution but rather whether we need to change the inherent nature of the Internet to make it more difficult to attack. | |||
First, Self Help, from Quadrant 4 was discussed, in which each computer user must “stay vigilant” for cyber attacks. However, this solution was limited by the average user’s knowledge and understanding of computer problems. In addition, the computer knowledgeable demographic has limited initiative to help those less informed without an external incentive. | |||
Second, Government Involvement, from Quadrant 1 was discussed. Either a national government or world government organization (ITU) would be responsible for defending against cyber attacks through programs such as Einstein 1,2, or 3, currently used for the military and federal government computers. However, this type of solution highlighted issues such as what level of government should be involved and responsible? The American people have a history of being more comfortable with state government involvement in regulating large aspects of their lives. While a centralized firewall would bring security, it gives the central government more control over an individual’s computer. Also, a combination of government and corporate solutions was discussed, in which the government provides the ultimate firewall but keeps ISPs liable for problems arising on their networks. | |||
Next, the Corporate Solution, in Quadrant 2, was discussed in which Corporations limit the ability of their networks to be attacked by limiting access and modification of their products. Apple Iphones and Android phones were compared to highlight corporate control. | |||
Finally, mutual cooperation with an institution of hierarchy, from Quadrant 3, was discussed. These solutions would rely upon cooperation between the users but have an institution of hierarchy to provide some stability or incentive for participation. Examples would be Wikipedia. However, this solution would also be limited because this solution relies upon the existence motivation. | |||
A final problem was discussed being that there could be cybersecurity issues waiting for us in our hardware. This stuff is made all over the world, often in countries that aren’t friendly to the U.S. How do we stop this? | |||
Possible Questions: | |||
#Do we want to fix these problems or are the solutions too costly to freedom and privacy? (Example PKI- advertisers sign and get an electronic signature…) | |||
#Is there an outside solution or must we change the inherent nature of the internet that must be changed? | |||
#Can mutual aid work or is it too limited by its dependant on incentive and motivation? | |||
[[Category: Cross-Sectional Themes]] | [[Category: Cross-Sectional Themes]] | ||
Latest revision as of 17:42, 12 September 2011
Overview
Thursday, 5:00-6:00pm
Lead: Jonathan Zittrain
Building upon key themes related to cybersecurity and the role of the private sector in ensuring persistent, secure, and consistently available content on the web, this session will focus on possible responses to the current state of computer and network security. Drawing conceptually from mutual aid treaties among states in the real world, Jonathan Zittrain will outline a defense scheme that would seek to make the current decentralized Web a more robust one. His" mirror as you link" system of assistance reimagines the technological relationships between sites and services on the Web, and envisions a new socially- and technologically-based system of redundancy and security. "Today, if one clicks on a link to an external site and that site is unavailable – perhaps attacked with a classic denial-of-service – there is no alternative to accessing it. Mirror-as-you-link would change that. Participating Web server administrators could make it so that for some or all of the links to external sites that they offer on their pages, the contents of the faraway sites would be saved (“cached”). They would do this only for sites that wish it to be done, and then only for sites that also perform such mirroring themselves. Then, when one site goes down, a Web surfer clicking on a link to get there can return to the referring site and ask for a copy of whatever he or she is missing since the destination site is down."
Required Readings
- The Harvard International Law Journal, "Jonathan Zittrain responds to Duncan Hollis", July 2011.
- Jonathan Zittrain, "Consider This: A Mutual Aid Treaty for the Internet", January 2010.
- Jonathan Zittrain, "The Fourth Quadrant", 78 Fordham L. Rev. 2767, January 2010.
Recommended Readings
- Jonathan Zittrain, "A Mutual Aid Treaty for the Net", 8 The Future of the Constitution Series, The Brookings Institution, January 27, 2011. (also available in PDF)
Student Reflections
This panel delved deeper into the cost and benefit analysis of solutions to previously mentioned cyber security problems. Such problems include dealing with networks that are difficult to control and resolve. Jonathan Zittrain categorized these problems into a quadrant chart dependant on the level of direct people participation in resolving these cyber security problems.
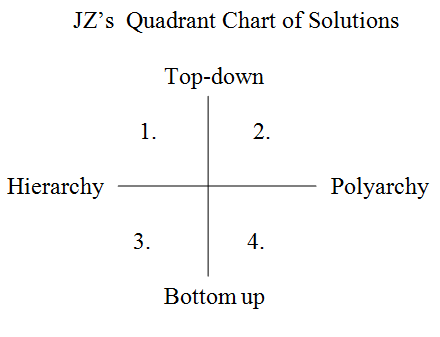
In discussing the different types of solutions, Zittrain showed how each solution followed the pattern of a generative dilemma presented by the nature of the internet: openness->abuse->lockdown. He asked whether the real problem is not the solution but rather whether we need to change the inherent nature of the Internet to make it more difficult to attack.
First, Self Help, from Quadrant 4 was discussed, in which each computer user must “stay vigilant” for cyber attacks. However, this solution was limited by the average user’s knowledge and understanding of computer problems. In addition, the computer knowledgeable demographic has limited initiative to help those less informed without an external incentive.
Second, Government Involvement, from Quadrant 1 was discussed. Either a national government or world government organization (ITU) would be responsible for defending against cyber attacks through programs such as Einstein 1,2, or 3, currently used for the military and federal government computers. However, this type of solution highlighted issues such as what level of government should be involved and responsible? The American people have a history of being more comfortable with state government involvement in regulating large aspects of their lives. While a centralized firewall would bring security, it gives the central government more control over an individual’s computer. Also, a combination of government and corporate solutions was discussed, in which the government provides the ultimate firewall but keeps ISPs liable for problems arising on their networks.
Next, the Corporate Solution, in Quadrant 2, was discussed in which Corporations limit the ability of their networks to be attacked by limiting access and modification of their products. Apple Iphones and Android phones were compared to highlight corporate control.
Finally, mutual cooperation with an institution of hierarchy, from Quadrant 3, was discussed. These solutions would rely upon cooperation between the users but have an institution of hierarchy to provide some stability or incentive for participation. Examples would be Wikipedia. However, this solution would also be limited because this solution relies upon the existence motivation.
A final problem was discussed being that there could be cybersecurity issues waiting for us in our hardware. This stuff is made all over the world, often in countries that aren’t friendly to the U.S. How do we stop this?
Possible Questions:
- Do we want to fix these problems or are the solutions too costly to freedom and privacy? (Example PKI- advertisers sign and get an electronic signature…)
- Is there an outside solution or must we change the inherent nature of the internet that must be changed?
- Can mutual aid work or is it too limited by its dependant on incentive and motivation?