Institutional structure: Difference between revisions
| Line 19: | Line 19: | ||
Under federal law, every agency has at least some cybersecurity responsibility: the Federal Information Security Management Act, [http://www.law.cornell.edu/uscode/uscode44/usc_sup_01_44_10_35_20_III.html|44 U.S.C § 3541 et seq.], requires the head of each federal agency to ensure compliance with information security standards promulgated by the National Institute of Standards and Technology (NIST). | Under federal law, every agency has at least some cybersecurity responsibility: the Federal Information Security Management Act, [http://www.law.cornell.edu/uscode/uscode44/usc_sup_01_44_10_35_20_III.html|44 U.S.C § 3541 et seq.], requires the head of each federal agency to ensure compliance with information security standards promulgated by the National Institute of Standards and Technology (NIST). | ||
== Responsibilities == | |||
One of the many uncertainties inherent in this discussion is how to go about classifying the types of responsibilities we want to allocate among the various federal agencies. The White House [http://www.whitehouse.gov/assets/documents/Cyberspace_Policy_Review_final.pdf Cyberspace Policy Review] (the 60-Day Review) notes that it considers "Cybersecurity policy" to include the following activities: | |||
* threat reduction | |||
* vulnerability reduction | |||
* deterrence, international engagement | |||
* incident response | |||
* resiliency | |||
* recovery policies and activities, | |||
"including computer network operations, information assurance, law enforcement, diplomacy, military, and intelligence missions as they relate to the security and stability of the global information and communications infrastructure." The 60-Day Review offers no explanation of what each term might entail (and in fact this might just be a throwaway list), but this provides at least a starting point for thinking about the array of responsibilities agencies may be saddled with in addressing potential and actual cyber-threats. | |||
== Links == | == Links == | ||
Revision as of 00:59, 19 December 2010
Introduction
Status Quo
While an increasing number of statutes and executive decisions organize agencies, allocate responsibilities and create inter-agency relationships, the current structure principally reflects historical and bureaucratic decisions by the agencies themselves rather than an overarching institutional design decision. As a result, the government structures for responding to cyber-threats are complex, with a number of agencies sharing authority in occasionally overlapping areas.
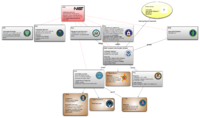
This chart, while by no means an exhaustive survey of government action in the realm of cybercrime and cyberwar, attempts to plot several of the major actors in those areas as well as the key relationships linking those actors together.
One consequence of this lack of centralization is the lack of agreed-upon categories and terms for discussing types and threats and forms of response.
Actors
Various government and private actors participate in preventing, detecting, and responding to various cyber-threats. Broadly speaking, these actors fall into four different categories:
- Cyber-specific federal agencies (e.g. Cyber Command)
- Defense and investigation agencies (e.g. Department of Defense, FBI, CIA, NSA, DOJ)
- Independent agencies with relevant concerns and vulnerabilities (e.g. Department of State, Federal Communications Commission)
- Private corporations
Under federal law, every agency has at least some cybersecurity responsibility: the Federal Information Security Management Act, U.S.C § 3541 et seq., requires the head of each federal agency to ensure compliance with information security standards promulgated by the National Institute of Standards and Technology (NIST).
Responsibilities
One of the many uncertainties inherent in this discussion is how to go about classifying the types of responsibilities we want to allocate among the various federal agencies. The White House Cyberspace Policy Review (the 60-Day Review) notes that it considers "Cybersecurity policy" to include the following activities:
- threat reduction
- vulnerability reduction
- deterrence, international engagement
- incident response
- resiliency
- recovery policies and activities,
"including computer network operations, information assurance, law enforcement, diplomacy, military, and intelligence missions as they relate to the security and stability of the global information and communications infrastructure." The 60-Day Review offers no explanation of what each term might entail (and in fact this might just be a throwaway list), but this provides at least a starting point for thinking about the array of responsibilities agencies may be saddled with in addressing potential and actual cyber-threats.
Links
- Structural
- Statutory
- Negotiated cooperation
- De facto cooperation
Current Problems
A Government Accountability Office report discussing the Comprehensive National Cybersecurity Initiative sums up one of the major problems with the current organizational situation thus: "Federal agencies have overlapping and uncoordinated responsibilities for cybersecurity, and it is unclear where overall responsibility for coordination lies."
The scarcity of official coordination between different government agencies raises a number of issues. Agencies may claim overlapping jurisdiction, leading to inefficient staffing and funding decisions (as well as inter-agency tension). At the same time, gaps in coverage between the jurisdictions of various agencies may emerge elsewhere. The inability of agencies effectively to share intelligence about possible threats in new technological contexts contributes to slower and less successful government responses.
As one example, this New York Times article describes how one hacker, Albert Gonzalez, was able to evade capture by the police for a number of attacks on different commercial websites while he was simultaneously under protection as a Secret Service informant.