Four Quadrants: Difference between revisions
| Line 66: | Line 66: | ||
=== Lynn === | === Lynn === | ||
In his article, ''[http://www.foreignaffairs.com/articles/66552/william-j-lynn-iii/defending-a-new-domain Defending a New Domain, The Pentagon Strategy]'', William Lynn starts from the assumption that the US government's digital infrastructure gives the US critical advantages over other countries. On the other hand, reliance on computer infrastructures exposes the US to disruptive attacks. The strategy adopted by the Pentagon, according to Lynn, must be based on the peculiar features of threats in cyberspace. In fact, the distinctive characteristics of cyberspace have led the Pentagon to recognize it as a new domain of warfare, as critical to military operations as other more traditional domain like air, space and land. | |||
:'''Government role''' | |||
:*Cyber warfare is asymmetric. Cyber weapons can be obtained at a relatively low cost, with high potentiality for disruptive results. This leads to ineffectiveness of a traditional deterrence model based on the acquisition of offensive capabilities against potential attackers. | |||
:*Lynn focuses instead on '''“active defense”''' mechanisms, capable of anticipating intrusion and attacks. This should be implemented through the new unified Cyber Command. | |||
:'''Private sector and international level''' | |||
:*Lynn recognizes that any plans aimed at defending military networks would be ineffective if civilian infrastructures are not secured against potential attacks, which could also be a target in military conflicts. | |||
:*In order to achieve the goal of enhanced security the Pentagon should further explore how major private companies can help the public sector in tackling cyber threats. Additionally, the US should also find ways to exploit the private sector's innovative capacity in information technology, especially since a dramatic importance in the cyber defense is predicated on the human factor, namely the availability of highly trained human resources. The dynamism and fast development capabilities of the private sector are also taken by Lynn as an example. | |||
:*In addition to this internal connection between military and civilian infrastructures, Lynn also points out that any efforts made by the US must take into account allied countries in order to cooperate in the monitor of computer networks intrusions. | |||
=== Wesley Clark === | === Wesley Clark === | ||
Revision as of 02:39, 20 December 2010
Introduction
Terms
Definitions
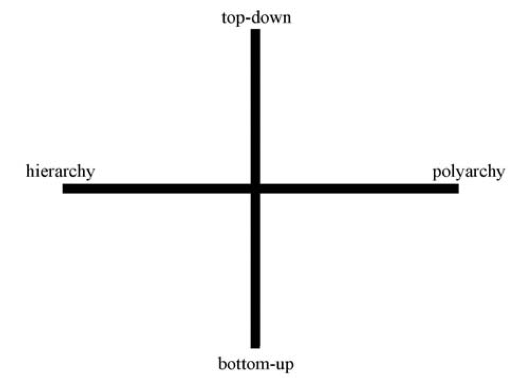
The Four Quadrants
In his article, The Fourth Quadrant, Professor Zittrain develops a four quadrant framework for thinking about the Internet. This framework looks at two criteria: (1) how generative something is, and (2) how singular it is.
The generativity of a phenomena is assessed on a scale from entirely “top-down” to entirely “bottom-up.” The range of singularity runs from “hierarchy” to “polyarchy.” This is captured in the following chart from the article:
Professor Zittrain uses precise (sometimes unconventional) definitions of these terms:
- Top-down: systems in which “there is a separation between those who make the rules and those who live under them . . . .”
- Bottom-up: systems where the rules can come from any person without separation between the people who make the rules and people who live under them.
- Hierarchy: “a system for which there is no alternative, either because it does not exist, because it would be too costly, or because law precludes it.”
- Polyarchy: being able to choose between multiple regimes or systems.
- To see how Professor Zittrain's definition of hierarchy differs from the lay person understanding, see Wikipedia.
Proposals
This section will summarize the proposals of various cyber security authors. The next section will attempt to map these proposals onto Professor Zittrain's framework.
Clarke
Zittrain
Goldsmith
Nye
In his article, Cyber Power Joseph Nye argues that barriers to entry into the cyber domain are so low that non-state actors and small states can play significant roles at low levels of cost. He points to three characteristics of cyber warfare, which distinguishes it from other kinds of traditional warfare:
- High number of players
- Ease of entry
- Opportunity for concealment
Each actor in the cyber domain has, according to Nye, specific powers and different sets of vulnerabilities, as shown in this chart from Nye's article:
Providing security is seen by Nye as a classic function of government, and increasing insecurity is believed to lead to an increased role of government in cyberspace. Nye indicates four major threats that should lead in principle to different solutions:
- Economic espionage
- Crime
- Cyber war
- Cyber terrorism
According to Nye, currently the highest costs come from the first two categories (economic espionage and crime), i.e., crimes committed by individual and small groups targeting civilian infrastructures and organizations. However, Nye envisages a change in the upcoming future, with cyberwar and cyber terrorism gaining importance.
- Nye's proposals
- Cyberwar:
- can be managed through inter-state deterrence, along with offensive capabilities to be used in the event that deterrence fails.
- can be regulated in the medium/long term through evolving norms of warfare comparable to the ones developed in relation to traditional warfare, such as proportionality.
- Cyber terrorism:
- is harder to contrast.
- Insofar as the attacks are directed against private infrastructures and organization, the threat can be dealt by incentivizing private actors, particularly owners of strategic infrastructure, to join secure systems rather than relying on the open internet.
- International treaties:
- Large scale formal treaties regulating cyberspace, according to Nye, are unlikely at the moment.
- While governments will end up remaining the stronger actors, cyberspace is likely to increase the diffusion of power to non-state actors.
Lynn
In his article, Defending a New Domain, The Pentagon Strategy, William Lynn starts from the assumption that the US government's digital infrastructure gives the US critical advantages over other countries. On the other hand, reliance on computer infrastructures exposes the US to disruptive attacks. The strategy adopted by the Pentagon, according to Lynn, must be based on the peculiar features of threats in cyberspace. In fact, the distinctive characteristics of cyberspace have led the Pentagon to recognize it as a new domain of warfare, as critical to military operations as other more traditional domain like air, space and land.
- Government role
- Cyber warfare is asymmetric. Cyber weapons can be obtained at a relatively low cost, with high potentiality for disruptive results. This leads to ineffectiveness of a traditional deterrence model based on the acquisition of offensive capabilities against potential attackers.
- Lynn focuses instead on “active defense” mechanisms, capable of anticipating intrusion and attacks. This should be implemented through the new unified Cyber Command.
- Private sector and international level
- Lynn recognizes that any plans aimed at defending military networks would be ineffective if civilian infrastructures are not secured against potential attacks, which could also be a target in military conflicts.
- In order to achieve the goal of enhanced security the Pentagon should further explore how major private companies can help the public sector in tackling cyber threats. Additionally, the US should also find ways to exploit the private sector's innovative capacity in information technology, especially since a dramatic importance in the cyber defense is predicated on the human factor, namely the availability of highly trained human resources. The dynamism and fast development capabilities of the private sector are also taken by Lynn as an example.
- In addition to this internal connection between military and civilian infrastructures, Lynn also points out that any efforts made by the US must take into account allied countries in order to cooperate in the monitor of computer networks intrusions.
Wesley Clark
“Sabotaged circuits cannot be patched; they are the ultimate sleeper cell.”
General Clark's article, Securing the Information Highway, focuses on the problem of compromised hardware -- usually chips with rogue transistors built in that allow another party to gain control of a system. Clark believes this is the greatest threat for cyber security.
- Software attacks, on the other hand, “are generally detectable, are mostly curable, and, until now, have been largely containable through the use of software patches."
- Two challenges with enhancing hardware security:
- 1. Ensuring authenticity.
- 2. Detecting malevolent function inside the device.
- Other problems that are making things worse:
- 1. Americans have a false sense of security.
- 2. We’re not doing anything – the longer we wait, the better adversaries will get.
Clark’s Solution:
We need to learn from the open-source community and create security standards that allow us to quickly discover and correct security flaws.
- We “need to endow U.S. networks, software, and even hardware with a digital immune system—one that is openly described and freely discussed.”
- Clark proposes a two-step approach:
- 1. Diversify the digital infrastructure.
- We need more diversity in both hardware and software (operating systems) to make it harder to attack large sections at once.
- 2. Secure the supply chain for hardware.
- Embed compact authentication codes directly into devices.
- Anti-tamper safeguards after devices are produced
- 1. Diversify the digital infrastructure.
- Note that this doesn’t mean we have to manufacture everything here – that’s a practical impossibility given the demand. We just need to ensure foreign-made products are “authentic and secure.”
Baker
Knake
In its report for the Council on Foreign Relations, Internet Governance in an Age of Cyber Insecurity, Knake examines the current position of the United States in dealing with cyber-security at the international level and the challenges faced by the international community.
Knake points out that while the US have refused to cooperate at the international level on a new governance for the internet, China, Russia and other non democratic regimes have been organizing a united front to promote a new model for the internet, tightly controlled by states. According to Knake, a free and open internet is in the US’ national interest and therefore the government should actively fight the threats arising from cyber crime, espionage and warfare while at the same time preserving the democratic infrastructure of the web.
In order to reach this goal Knake indicates three basic principles, to be implemented through a three-part agenda the US should implement:
- 1. Take a networked and distributed approach
- 2. Establish accountability of states for their actions, the actions of their citizens, and their systems
- 3. Start cleaning up the US national network
The above three principles should be implemented through the following three-part agenda:
- 1. Create a stronger sets of international regimes to fight crime in cyberspace
- Knake appears to be a supporter of a hands-off approach to the Internet. He points out that so far the US has only maintained control of one necessary infrastructure component (the DNS, Domain Name System) which needs active management, but otherwise has taken the position that the role of the government should be limited. According to Knake this approach should be adapted at changing times and increased cyber threats at the international level. New times demand the development of new international instruments to fight cyber crime and implement real-time mechanisms for international cooperation in fighting and investigating cross-border attacks.
- Russia has been pushing since 1998 for a UN treaty to address conflicts in cyberspace creating a centralized international body to tackle cyber security issues. Knake, however, opposes a state-centric intergovernmental organization in that contrary to US interests, but rather supports a cooperative solution involving non-governmental organizations and the private sector in the development of new norms and the implementation of a more secure infrastructure.
- In certain areas, however, governmental intervention is the only practicable solution, where decentralized and inclusive approach does not work. Cyber crime (and relating problems of investigating, apprehending and prosecuting cyber criminals) is one of these areas. Council of Europe's convention on cybercrime helped in establishing laws to criminalize computer crimes and a mechanism for cross-border cooperation. However, according to Knake, it did not lead to a reduction of cybercrime. Further, such convention only envisages bilateral and prosecutorial mechanisms, ineffective in preventing attacks or tackling an attack when it occurs.
- Knake suggested the creation of national level criminal laws and development of less formal mechanisms of cooperation through a “light” intergovernmental body. Knake's goal is a stronger international governance of the internet, but “tailored to specifically address a narrow set of security concerns surrounding crime and warfare”. An approach clearly opposed to Russia's and China's “information security”.
- 2. Constrain state actors in cyberspace
- In order to solve the attribution problem (i.e., the extreme difficulties in tracking the origin of attacks in the cyberspace) Knake suggests that US should commit to pursue criminal prosecution of citizens engaging in hacktivism against foreign countries. Foreign states should do the same, and failure to cooperate in doing so should be deemed as a sign of complicity. States should be accountable for their actions, as well as those of their citizens and their systems.
- In the past decade US has been focusing on cybercrime and refused to enter into negotiations on warfare and espionage.
- Knake says US should now overthrow the perception that US wants to maintain exploitation and attack capabilities at a level above other states. While keeping such capabilities is in the US interest, giving away such perception may be detrimental, and refusing in particular to enter into negotiations on state limitations to cyber warfare attracts critics.
- Knake suggests a renewed engagement of the US, but not as set forth in current treaty options. The Russian proposal, for instance, would commit signatories to abstain from developing offensive cyber capabilities while not providing any mechanism for the verification of their compliance. His proposed solution would be not to focus on limiting state actors offensive capabilities, bur rather limiting their penetration into civilian infrastructures (power grids, financial infrastructures).
- 3. Secure the internet's underlying technology
- Knake suggests that it is now time to shift the focus of international and local attention from coordination and interoperability to security. The development of more secure technical protocols is much needed, Knake argues, and the government should provide guidance in the technical area. The private sector should be involved in a centralized forum established by the government to coordinate the internet governance agenda, including big US corporations such as Microsoft and Symantec.
Mapping Onto the Four Quadrants
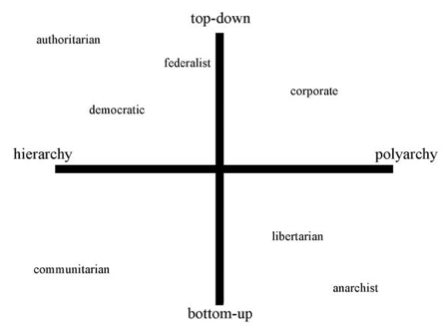
Four Quadrants: Elaborated
Professor Zittrain mapped existing political philosophies onto his four quadrants. The result was presented in his article:
Mapping the Proposals
Where We Think They Go
More Clear
INSERT CHART
- Quadrant 1
- Nye: Nye's proposal appears to fall squarely in the first quadrant. He believes governmental authorities to be the most important actors in the cyber domain, and while he calls for the enhancement of private sector infrastructures' security, he seems to suggest that it should be done through government intervention. Furthermore, Nye do not believe that an international solution would be easily found.
- Quadrant 2
- Wesley Clark: Clark's proposal clearly falls in the second quadrant. His call to diversify the digital infrastructure is a polyarchical solution. Additionally, Clark intends for the government to promulgate all of these rules, which is a top-down solution.
- Quadrant 3
- Quadrant 4
Less Clear
Quadrant 4 or 1?
- Knake: At a first sight Knake's set of proposals appears to fall within the fourth quadrant. He is in fact proposing a Networked and distributed approach, to be implemented through the active involvement of a wide range of participants from the technical community, the private sector, as well as users and consumer groups, to shape policy and avoid state-centric processes. Not a single forum, at either national or international level, bur rather a range of forums.
- At a deeper reading of Knake's arguments, however, it appears more clear that - in his mind - the US should nurture and indirectly control his proposed "light intergovernmental body". When Knake urges the US to be involved in international negotiations concerning the fight of cyber crime, he does so to avoid a "perception" that would eventually turn out to be detrimental to the US. Even private actors, such as Microsoft and Symantec, would be captured in the governmental sphere, by being made aware of the goals of the US government and actively help in achieving such goals.