Four Quadrants: Difference between revisions
| Line 40: | Line 40: | ||
=== Wesley Clark === | === Wesley Clark === | ||
''“Sabotaged circuits cannot be patched; they are the ultimate sleeper cell.”'' | |||
General Clark's article, ''[http://cognosys.net/classes/fall10/cs446/resources/Securing%20the%20Information%20Highway-foreign-affairs-1109.pdf Securing the Information Highway]'', focuses on the problem of compromised hardware -- usually chips with rogue transistors built in that allow another party to gain control of a system. Clark believes this is the greatest threat for cyber security. | General Clark's article, ''[http://cognosys.net/classes/fall10/cs446/resources/Securing%20the%20Information%20Highway-foreign-affairs-1109.pdf Securing the Information Highway]'', focuses on the problem of compromised hardware -- usually chips with rogue transistors built in that allow another party to gain control of a system. Clark believes this is the greatest threat for cyber security. | ||
*Software attacks, on the other hand, “are generally detectable, are mostly curable, and, until now, have been largely containable through the use of software patches." | |||
*Software attacks, on the other hand, “are generally detectable, are mostly curable, and, until now, have been largely containable through the use of software patches | |||
:'''Two challenges''' with enhancing hardware security: | :'''Two challenges''' with enhancing hardware security: | ||
Revision as of 20:23, 19 December 2010
Introduction
Terms
Definitions
The Four Quadrants
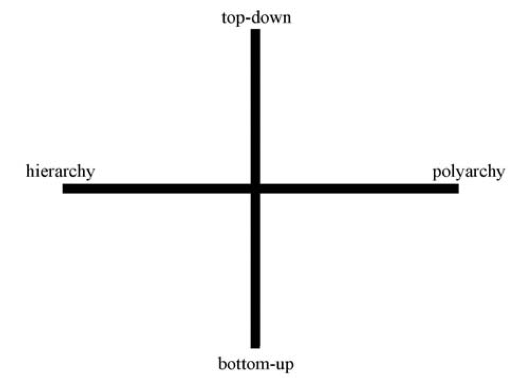
In his article, The Fourth Quadrant, Professor Zittrain develops a four quadrant framework for thinking about the Internet. This framework looks at two criteria: (1) how generative something is, and (2) how singular it is.
The generativity of a phenomena is assessed on a scale from entirely “top-down” to entirely “bottom-up.” The range of singularity runs from “hierarchy” to “polyarchy.” This is captured in the following chart from the article:
Professor Zittrain uses precise (sometimes unconventional) definitions of these terms:
- Top-down: systems in which “there is a separation between those who make the rules and those who live under them . . . .”
- Bottom-up: systems where the rules can come from any person without separation between the people who make the rules and people who live under them.
- Hierarchy: “a system for which there is no alternative, either because it does not exist, because it would be too costly, or because law precludes it.”
- Polyarchy: being able to choose between multiple regimes or systems.
PROVIDE LINKS TO HOW THESE DEFINITIONS DIFFER FROM TRADITIONAL UNDERSTANDINGS OF THEM.
Proposals
This section will summarize the proposals of various cyber security authors. The next section will attempt to map these proposals onto Professor Zittrain's framework.
Clarke
Zittrain
Goldsmith
Nye
Lynn
Wesley Clark
“Sabotaged circuits cannot be patched; they are the ultimate sleeper cell.”
General Clark's article, Securing the Information Highway, focuses on the problem of compromised hardware -- usually chips with rogue transistors built in that allow another party to gain control of a system. Clark believes this is the greatest threat for cyber security.
- Software attacks, on the other hand, “are generally detectable, are mostly curable, and, until now, have been largely containable through the use of software patches."
- Two challenges with enhancing hardware security:
- 1. Ensuring authenticity.
- 2. Detecting malevolent function inside the device.
- Other problems that are making things worse:
- 1. Americans have a false sense of security.
- 2. We’re not doing anything – the longer we wait, the better adversaries will get.
Clark’s Solution:
We need to learn from the open-source community and create security standards that allow us to quickly discover and correct security flaws.
- We “need to endow U.S. networks, software, and even hardware with a digital immune system—one that is openly described and freely discussed.”
- Clark proposes a two-step approach:
- 1. Diversify the digital infrastructure.
- We need more diversity in both hardware and software (operating systems) to make it harder to attack large sections at once.
- 2. Secure the supply chain for hardware.
- Embed compact authentication codes directly into devices.
- Anti-tamper safeguards after devices are produced
- 1. Diversify the digital infrastructure.
- Note that this doesn’t mean we have to manufacture everything here – that’s a practical impossibility given the demand. We just need to ensure foreign-made products are “authentic and secure.”