Four Quadrants: Difference between revisions
BerkmanSysop (talk | contribs) UTurn to 1297036800 |
|||
| (109 intermediate revisions by 7 users not shown) | |||
| Line 1: | Line 1: | ||
== Introduction == | |||
Cyber-security has emerged as a [http://www.pattonboggs.com/news/detail.aspx?news=1054 hot topic] for social and legal scholars. Despite the widespread interest, it remains unclear what the problem entails and how we can work towards one or more solutions. This Wiki attempts to define key terms used in cyber-security, clarify the problems and solutions identified by various scholars, and view these approaches through Professor Zittrain's four-quadrants framework. | |||
== Terms == | == Terms == | ||
===Definitions=== | ===Definitions=== | ||
'''Cyber''' as a prefix refers to electronic and computer-based technology. Cyber-space is “an operational domain framed by use of electronics to … exploit information via interconnected systems and their associated infra structure.” (Kuehl cited in ''[http://belfercenter.ksg.harvard.edu/files/cyber-power.pdf Joseph Nye]'', 2010: 3) According to ''[http://www.amazon.com/Profiling-Hackers-Science-Criminal-Applied/dp/1420086936 Raul Chiesa]'' there is a | |||
: “need to avoid terms such as ‘real-world’ and ‘virtual reality’, which have been and still are abused, apart from being evidently wrong. In fact, those who commit electronic attacks not only don’t consider there to be any difference between the two, but indeed the second category does not exist, as whatever takes place on a network, Web, or ‘behind the scenes’ of telephone exchanges or lines is not at all virtual but real. We believe it to be more precise and less misleading to talk about electronic world and physical world.” (Chiesa et al, 2009: XXII) | |||
'''Cyber-space''' is therefore “a unique hybrid regime of physical and virtual properties,” hardware and software, which is all of the computer networks in the world including the Internet plus the other networks separate and not linked to the Internet. (Nye, 2010: 3; ''[http://www.amazon.com/Cyber-War-Threat-National-Security/dp/0061962236 Clarke and Knake]'', 2010: 70) | |||
'''Cyber-security''' can be divided to face four major threats: espionage, crime, cyber war, and cyber terrorism (Nye, 2010: 16). The possibility for the existence of a threat in the first place goes back to three sources: “(1) flaws in the design of the Internet; (2) flaws in the hardware and software; and (3) the move to put more and more critical systems online.” (Clarke and Knake, 2010: 73) | |||
'''Cyber-warfare''' has been defined by Clarke and Knake as “the unauthorized penetration by, on behalf of, or in support of, a government into another nation’s computer or network, or any other activity affecting a computer system, in which the purpose is to add, alter, or falsify data, or cause the disruption of or damage to a computer, or network device, or the objects a computer system controls.” (Clarke and Knake, 2010: 227) | |||
The ''[http://www.unicri.it/emerging_crimes/cybercrime/cyber_crimes/hpp.php Hackers Profiling Project]'' of the United Nations Interregional Crime and Justice Research Institute (UNICRI) proposes a typology for actors in cyber-space. They identify Wannabee Lamer; Script-kiddie; the “37337 K-rAd iRC #hack 0-day exploitz” guy; Cracker; Ethical Hacker; Quiet, paranoid, and skilled hacker; Industrial Spy; Cyber-warrior; Government Agent, Military Hacker. (Chiesa et al, 2009: 52-56, 61) As these types sometimes overlap, they can be reduced to the following three groups relevant in cyber-warfare: | |||
*'''Cyber-warrior''': private actors who are highly skilled mercenaries hacking for money or for ideals | |||
*'''Government Agent''': “the civilian state actor” - hackers employed by a country’s civilian government for (counter)espionage, information monitoring of governments, terrorist groups, strategic industries, and individuals without the authority to cause physical death through the use of the electronic world. (Chiesa et al, 2009: 56) | |||
*'''Military Hacker''': “the military state actors” - hackers employed by a country’s military potentially with the authority to cause physical death through the use of the electronic world in times of war. | |||
This categorization is more elaborate than Clarke and Knake’s general usage of the term "cyber warriors," which simply distinguishes between criminals and military hackers. The UNICRI-based categories provide greater clarity to differentiate between the various actors in cyber-warfare, state and non-state as well as military and civilian. | |||
'''Cyber Equilibrium 1.0'''. In the 20th century the cyber environment from a hacker’s point of view can be described as an equilibrium between “three different entities in our society – superpowers that are competing against each other: the hacker community, governments, and the Internet community in general […] a shift in the balance of power and consequently concentrating it all in one group’s hands […] is unacceptable for hackers, as power should always be equally shared between the three entities […] Hackers have no concept of a hierarchical, authoritarian (vertical) relation between the three entities, but that only an equal relationship (horizontal), peer to peer, can be considered synonymous with true democracy.” (Chiesa et al, 2009: 114-15) | |||
'''Hacker ethics''' played an important role. (Chiesa et al, 2009: 172-76) This ideal picture began to crack at the end of the 1990s when hacking became increasingly politicized. Before hacking was considered apolitical by its nature in the sense that the political actions of hackers were reduced to ensuring the aforementioned equilibrium. However, eventually “hacktivism” emerged, political activism through hacking. Hacking moved from being an end in itself to being a means for achieving a different political end. The first HackMeeeting took place in Florence in 1997. It remains unclear if the events in Estonia in 2007 were also an expression of a nationalist Russian hacktivism. At the same time, the hacker crackdowns started driving hackers into the underground. (Chiesa et al, 2009: 120, 162) | |||
'''Cyber Equilibrium 2.0'''. The 21st century paints a different picture. During most of the 20th century the vast majority of Internet users were Westerners who shared a common set of norms. That is why the equilibrium was a representation of citizens vs. governments or rather the individual vs. the state. The cultural difference between a hacker in the US, the UK, or Spain was much smaller than their cultural similarity in opposing their respective government in restricting their hacking activity. But with the rapid expansion of Internet users around the globe and the politicization of hacking, this has changed. A new type of alliance has emerged as illustrated by the activities of hackers after 9/11 in support of the U.S. government or the Russian hackers supporting the Russian government during its [http://en.wikipedia.org/wiki/2008_South_Ossetia_war war with Georgia] in 2008. While the Cyber Equilibrium 1.0 continues to exist in the various societies though less openly as a result of the crackdowns, it is now complemented by an internationalized Cyber Equilibrium 2.0 that resembles more a classic balance of power concept. | |||
'''Cyber-power''' “is ‘the ability to use cyberspace to create advantages and influence events in other operational environments and across the instruments of power.’ Cyber power can be used to produce preferred outcomes within cyberspace or it can use cyber instruments to produce preferred outcomes in other domains outside cyberspace.” (Kuehl cited in Nye, 2010: 4) A good overview of the different techniques of hacking is given in UNICRI’s ''Profiling Hackers – The Science of Criminal Profiling as Applied to the World of Hacking''. (Chiesa et al, 2009: 20-32) In addition to power derived from the mastering of hacking techniques, a legitimate source of power is the root authority which is “the power to issue orders respecting domain names and numbers and have those orders obeyed.” (Goldsmith and Wu, 2008: 32) This power is currently in the hands of ICANN, which is under contract of the U.S. Department of Commerce. Given the U.S. government’s interpretation of such contractual relationships when dealing with [http://en.wikipedia.org/wiki/Jon_Postel#The_US_takeover_of_the_DNS_Root_Authority Jon Postel and the MoUvement] in the 1990s, it is safe to argue that through ICANN, it is the U.S. government that controls the root authority (''[http://www.amazon.com/Who-Controls-Internet-Illusions-Borderless/dp/0195340647/ref=sr_1_1?s=books&ie=UTF8&qid=1292883705&sr=1-1 Goldsmith and Wu]'', 2008: 29-46). | |||
'''The Internet''' as the biggest network in cyber-space is designed to be “open, minimalist, and neutral.” (Goldsmith and Wu, 2008: 23) Similar to the constructivist critique of the realist balance of power, the Internet’s architecture is contingent, however, and “ a choice – not fate, not destiny, and not natural law.” (Goldsmith and Wu, 2008: 90) Alternative manifestations can be found in China or Saudi-Arabia. The “bordered Internet” that emerged through national changes of the Internet’s architecture is the result of national laws, technological developments enabling the implementation of certain policies, and on a broader level the preferences of different cultures. (Goldsmith and Wu, 2008: 149-50) | |||
===The Four Quadrants=== | ===The Four Quadrants=== | ||
| Line 17: | Line 63: | ||
*'''Top-down''': systems in which “there is a separation between those who make the rules and those who live under them . . . .” | *'''Top-down''': systems in which “there is a separation between those who make the rules and those who live under them . . . .” | ||
*'''Bottom-up''': systems where the rules can come from any person without separation between the people who make the rules and people who live under them. | *'''Bottom-up''': systems where the rules can come from any person without separation between the people who make the rules and people who live under them. | ||
*'''Hierarchy''': | *'''Hierarchy''': a system in which "gatekeepers control the allocation of attention and resources to an idea" or "a system for which there is no alternative, either because it does not exist, because it would be too costly, or because law precludes it." | ||
*'''Polyarchy''': being able to choose between multiple regimes or systems. | :*Note: to see how Professor Zittrain's definition of hierarchy might differ from the lay person understanding, see [http://en.wikipedia.org/wiki/Hierarchy#History_of_the_term Wikipedia]. | ||
*'''Polyarchy''': being able to choose between multiple regimes or systems and pursue ideas independently. | |||
For more on this system, see ''[http://yupnet.org/zittrain/archives/13 The Future of the Internet and How to Stop It]'', chapter 4. | |||
== Proposals == | == Proposals == | ||
This section will summarize the proposals of various cyber security authors. The next section will attempt to map these proposals onto Professor Zittrain's framework. | This section will summarize the proposals of various cyber-security authors. The next section will attempt to map these proposals onto Professor Zittrain's framework. | ||
=== Richard Clarke & Robert Knake === | |||
In their book ''Cyber War'' Richard Clarke and Robert Knake discuss “the next great threat to national security.” | |||
Clarke and Knake identify the following key vulnerabilities: | |||
: I) Internet addressing system using the Domain Name System | |||
: II) routing among ISPs, the Border Gateway Protocol | |||
: III) openness, unencrypted Internet | |||
: IV) propagation of intentionally malicious traffic, malware | |||
: V) one big network with a decentralized design | |||
They recount the cyber attack on Syria on 6 September 2007, the DDoS attack on Estonia in May 2007, and on Georgia in 2008. Aware of the near impossibility to attribute an attack to its source, they outline the '''range of possible means of attacks''' such as logic bombs, ghost nets, and botnets. Their book tells the story of the internal fight within the US government over who has authority in the cyber realm ultimately resulting in the creation of the U.S. Cyber Command headed by the head of the NSA. The USG also adopted a ''[http://www.dod.gov/pubs/foi/ojcs/07-F-2105doc1.pdf National Military Strategy for Cyber Operations]''. | |||
Some of what seemed far-fetched in the book (published in April 2010) has since become reality: | |||
'''Wikileaks''': | |||
:The “sneakernet threat” posed by the air gap between the unclassified and secret level network SIPRNET is at the core of the current Wikileaks affair (p. 171). | |||
:''[http://www.bbc.co.uk/news/world-us-canada-11863618 BBC: SIPRNET]'' | |||
'''Stuxnet''': | |||
:The description of a manipulation of generators resembles the latest analyzes of the Stuxnet virus altering centrifuges (p. 100). | |||
:''[http://www.economist.com/node/17147818 The Economist: A Worm in the Centrifuge]'' | |||
:''[http://www.theatlantic.com/technology/archive/2010/11/ahmadinejad-publicly-acknowledges-stuxnet-disrupted-iranian-centrifuges/67155/ The Atlantic: Stuxnet]'' | |||
:For more information on major cyber attacks from the past few years, see the recent article in [http://www.newscientist.com/article/mg20827915.100-are-states-unleashing-the-dogs-of-cyber-war.html NewScientist]. The article looked at each attack's level of sophistication and the likelihood that it was state-sponsored, presenting its results in a useful [http://www.newscientist.com/data/images/archive/2791/27915101.jpg image]. | |||
[[Image:sshot-1.jpg]] | |||
'''KEY QUESTIONS (pp. 152-154)''' | |||
: 1) What do we do if we wake up one day and find the western half of the U.S. without electrical power as the result of a cyber attack? | |||
: 2) Is the advent of cyber war a good thing, or does it place us at a disadvantage? | |||
: 3) Do we envision the use of cyber war weapons only in response to the use of cyber war weapons against us? | |||
: 4) Are cyber weapons something that we will employ routinely in both small and large conflicts? Will we use them early in a conflict because they give us a unique advantage in seeking our goals, such as maybe affecting a rapid end to the conflict? | |||
: 5) Do we think we want to have plans and capabilities to conduct “stand-alone” cyber war against another nation? And will we fight in cyberspace even when we’re not shooting at the other side in physical space? | |||
: 6) Do we see cyber space as another domain (like the sea, airspace, or outer space) in which we must be military dominant and in which we will engage an opponent while simultaneously conducting operations in other domains? | |||
: 7) How surely do we have to identify who attacked us in cyberspace before we respond? What standards will we use for these identifications? | |||
: 8) Will we ever hide the fact that it was us who attacked with cyber weapons? | |||
: 9) Should we be hacking into other nations’ networks in peacetime? If so, should there be any constraints on what we would do in peacetime? | |||
: 10) What do we do if we find that other nations have hacked into our networks in peacetime? What if they left behind logic bombs in our infrastructure networks? | |||
: 11) Do we intend to use cyber weapons primarily or initially against military targets only? How do we define military targets? | |||
: 12) Or do we see the utility of cyber weapons being their ability to inflict disruption on the economic infrastructure or the society at large? | |||
: 13) What is the importance of avoiding collateral damage with our cyber weapons? How might avoiding it limit our use of the weapons? | |||
: 14) If we are attacked with cyber weapons, under what circumstances would, or should, we respond with kinetic weapons? How much of the answer to that question should be publicly known in advance? | |||
: 15) What kind of goals specific to the employment of cyber weapons would we want to achieve if we conducted cyber war, either in conjunction with kinetic war or as a stand-alone activity? | |||
: 16) Should the line between peace and cyber war be brightly delineated, or is there an advantage to us in blurring that distinction? | |||
: 17) Would we fight cyber war in a coalition with other nations, helping to defend their cyberspace and sharing our cyber weapons, tactics, and targets? | |||
: 18) What level of command authority should authorize the use of cyber weapons, select the weapons, approve the targets? | |||
: 19) Are there types of targets that we believe should not be attacked using cyber weapons? Do we attack them anyway if similar U.S. facilities are hit first by cyber or other weapons? | |||
: 20) How do we signal our intentions with regard to cyber weapons in peacetime and in crisis? Are there ways that we can use our possession of cyber weapons to deter an opponent? | |||
: 21) If an opponent is successful in launching a widespread, disabling attack on our military or on our economic infrastructure, how does that affect our other military and political strategies? | |||
=== Goldsmith === | '''PROPOSALS ''' | ||
After a chapter on what the authors call “Defensive Triad Strategy”, a chapter on the limits of offensive use, and a chapter on an international framework for a cyber peace, the following recommendations conclude the book: | |||
: 1) '''Thinking About the Unseeable''': | |||
:: A broad public dialogue to raise awareness and allow for an open discussion of strategies and the balance of values they represent | |||
: 2) '''The Defensive Triad''': | |||
:: i) stop malware on the Internet at the backbone ISPs | |||
:: ii) hardens the controls of the electric grid [while it is unclear why the authors do not include all SCADA controlled systems] | |||
:: iii) increases the DoD networks and integrity of its weapons | |||
: 3) '''Cyber Crime: | |||
:: Combat cyber crime, reducing the economic incentive, prevent safe havens | |||
: 4) '''Cyber War Limitation Treaty (CWALT)''': | |||
:: CWALT I – initial agreement | |||
:::- establish a Cyber Risk Reduction Center to exchange information and provide nations with assistance; | |||
:::- create as international-law concepts the obligation to assist and national cyber accountability; | |||
:::- impose a ban on first use cyber attacks against civilian infrastructure, a ban that would be lifted against another nation when (a) the two nations were in a shooting war, or (b) the defending nation had been attacked by the other nation with cyber weapons; | |||
:::- prohibit the preparation of the battlefield in peacetime by the emplacement of trapdoors or logic bombs on civilian infrastructure, including electric grids, railroads, etc.; and | |||
:::- prohibit altering data or damaging networks of financial institutions at any time, including the preparation to do so by the emplacement of logic bombs | |||
: 5) '''A New Internet Architecture''' | |||
: 6) '''POTUS''': establish clear lines of authority with the President at the top and required to approve emplacement of logic bombs, trapdoors, etc. | |||
=== Jonathan Zittrain === | |||
Professor Zittrain begins his forthcoming article, ''A Mutual Aid Treaty for the Internet''*, by describing mutual aid theory broadly and applying it to individuals on the Internet. By taking mutually beneficial, reciprocal actions, individual Internet participants can deal with real problems more efficiently. | |||
This mutual aid framework is then extended to the World Wide Web. To ensure that cyber attacks cannot take down a website, Professor Zittrain proposes “Mirror As You Link.” This proposal takes the following form: | |||
:1. You visit a website. | |||
:2. The website appears on your computer. | |||
:3. As the site loads, your computer follows any links on the page and makes a local copy of these pages. | |||
:4. If a link no longer works, you can ask the linking site “to show you its best rendition of what you’re missing at the linked site.” | |||
This system would require a change in the code, modifying the way Web servers work. Because Microsoft and Apache control 80% of the web server market, however, this would not be difficult. Additionally, if someone didn’t want their website to participate in Mirror As You Link, they could choose to block your computer from making a local copy. | |||
-*This piece isn't currently available on the Internet. For a brief summary of these arguments see Professor Zittrain's New York Times piece on the subject, [http://roomfordebate.blogs.nytimes.com/2010/01/15/can-google-beat-china/#jonathan What Websites Can Do]. | |||
=== Jack Goldsmith === | |||
There are two relevant pieces by Jack Goldsmith in which he explores his thoughts on cyber security: the book he coauthored with Tim Wu, ''[http://books.google.com/books?id=GsylX8a_npcC&printsec=frontcover&dq=goldsmith+who+controls+the+internet&source=bl&ots=mzmdkDFC8N&sig=axkQkdD8P-06YzSPRRSACyZf_VI&hl=en&ei=WDAOTdLhFYT48Aa4ze3nDQ&sa=X&oi=book_result&ct=result&resnum=4&ved=0CDYQ6AEwAw#v=onepage&q&f=false Who Controls The Internet?: Illusions of a Borderless World]'', and a recent article published in The New Republic titled ''[http://www.tnr.com/article/books-and-arts/75262/the-new-vulnerability The New Vulnerability]''. | There are two relevant pieces by Jack Goldsmith in which he explores his thoughts on cyber security: the book he coauthored with Tim Wu, ''[http://books.google.com/books?id=GsylX8a_npcC&printsec=frontcover&dq=goldsmith+who+controls+the+internet&source=bl&ots=mzmdkDFC8N&sig=axkQkdD8P-06YzSPRRSACyZf_VI&hl=en&ei=WDAOTdLhFYT48Aa4ze3nDQ&sa=X&oi=book_result&ct=result&resnum=4&ved=0CDYQ6AEwAw#v=onepage&q&f=false Who Controls The Internet?: Illusions of a Borderless World]'', and a recent article published in The New Republic titled ''[http://www.tnr.com/article/books-and-arts/75262/the-new-vulnerability The New Vulnerability]''. | ||
| Line 37: | Line 203: | ||
'''Who Controls the Internet''' | '''Who Controls the Internet''' | ||
Globalization has diminished the importance of borders, territory and locations, and has undermined the role of nation state's governments as the central institution for the governance and regulation of human affairs. The | Globalization has diminished the importance of borders, territory and locations, and has undermined the role of nation state's governments as the central institution for the governance and regulation of human affairs. The Internet has been seen as the catalyst of globalization and therefore it is essential in re-assessing if, and how, the role of governments has changed. Goldsmith and Wu conclude that physical coercion by government, which is a feature of traditional legal systems, has not been affected by the Internet and by globalization and remains today more important than expected. A number of examples gives evidence of this allegation: from the [http://en.wikipedia.org/wiki/Internet_censorship_in_the_People's_Republic_of_China actions taken by Chinese government against dissidents], to the softer approach taken by western governments in inducing ISP to filter [http://en.wikipedia.org/wiki/LICRA_vs._Yahoo offensive communications] and fighting [http://en.wikipedia.org/wiki/Internet_censorship P2P file sharing]. | ||
*''The role of governments'' | |||
:Goldsmith and Wu contend that governmental powers around the globe are striving to shape the architecture of the Internet through the use of their coercive power. This is leading to the de facto establishment of different local networks, more or less far from the open, free and worldwide Internet we have seen so far. | |||
::*According to this thesis, the openness of the Internet is not an inherent feature of the architecture, but rather a contingency due to the governmental coercion model that has prevailed so far. The differences between models for controlling the Internet would lead to a new technological cold war, where each side would push its own model for architecting the Internet, with the result of transforming the Internet into a collection of nation-state networks, separate from each other for many purposes. | |||
In spite of the prominent role that governments still have on the | *''The role of communities'' | ||
:In spite of the prominent role that governments still have on the Internet, Goldsmith and Wu suggest that private self-governing communities can still be an alternative to traditional government. | |||
::*At the same time, they suggest that this alternative governance model based on social norms, morality and the market cannot survive without an “underlying system of territorial government and physical coercion”. [http://www.icann.org ICANN] is brought as an example of this: a self-governance model based on technology and technocracy has managed to emerge and survive on the basis of the guarantees provided by the US government. | |||
*''Cybercrime'' | |||
:In this context of nation-states networks, the book still calls for a global solution to cybercrime, a solution that would establish international legal instruments prohibiting computer invasion and disruption and set standards for inter-governmental cooperation. | |||
::*However, the authors also points at the inefficacy of a traditional international treaty in tackling cyber threats. The one example currently in place, for instance, the [http://conventions.coe.int/Treaty/Commun/QueVoulezVous.asp?NT=185&CL=ENG Council of Europe's Cybercrime Convention], has only been implemented by a scarce number of states and the response mechanisms set forth therein are deemed to be inappropriate. | |||
*''Cybercrime: an architectural solution'' | |||
The conclusion reached by Goldsmith and Wu is that the future of the Internet's security is not likely to rest on a traditional international treaty, but rather on an architectural solution. A “global law”, it is argued, already exists and it is the domain name system managed by ICANN. ICANN has been portrayed by the US as a form of bottom-up governance, serving and drawing inputs from the | :The conclusion reached by Goldsmith and Wu is that the future of the Internet's security is not likely to rest on a traditional international treaty, but rather on an architectural solution. | ||
::*A “global law”, it is argued, already exists and it is the domain name system managed by ICANN. ICANN has been portrayed by the US as a form of bottom-up governance, serving and drawing inputs from the Internet “community” in the spirit of self-regulation. | |||
::*It is also pointed out that along the years the US has abandoned the rhetoric about a self-governed ICANN and has asserted that the control over ICANN will not be relinquished. While Goldsmith and Wu do not take a position on the outcome of the battle over control of ICANN, they stress that, as a matter of fact, the actors of such battle are nation-states rather than Internet communities and private companies. | |||
'''The New Vulnerability''' | '''The New Vulnerability''' | ||
Excessive focus on cyber war | In a recent article published in [http://www.tnr.com/article/books-and-arts/75262/the-new-vulnerability ''The New Republic''], Goldsmith takes a stand on Clarke's book [http://www.richardaclarke.net/index.php ''Cyber War: The Next Threat to National Security and What to Do About It"]. The main areas of criticism in Clarke's approach indicated by Goldsmith are the following: | ||
Greatest cyber threats come from espionage and theft | :*Excessive focus on cyber war | ||
Private actors are becoming more dangerous and sophisticated | :*The terrorism threat is underestimated | ||
Potentiality of enormous economic damages | :*Greatest cyber threats come instead from espionage and theft | ||
:*Private actors are becoming more dangerous and sophisticated | |||
:*Potentiality of enormous economic damages | |||
On the other hand, Goldsmith identifies several distinct difficulties that the US faces in tackling the new cyber threats: | |||
Companies underinvest in cyber safety: private profit vs. larger national interest | :*Companies underinvest in cyber safety: private profit vs. larger national interest | ||
Government fails to regulate software quality and service providers to avoid raising the costs of Internet access | :*Government fails to regulate software quality and service providers to avoid raising the costs of Internet access | ||
US skepticism in extensive Government action prevents a governmental involvement in defending private computer networks | :*US skepticism in extensive Government action prevents a governmental involvement in defending private computer networks | ||
In his article, ''[http://belfercenter.ksg.harvard.edu/files/cyber-power.pdf Cyber Power]'' Joseph Nye argues that barriers to entry into the cyber domain are so low that non-state actors and small states can play significant roles at low levels of cost. He points to three characteristics of cyber warfare, which distinguishes it from other kinds of traditional warfare: | === Joseph Nye === | ||
In his article, ''[http://belfercenter.ksg.harvard.edu/files/cyber-power.pdf Cyber Power]'', Joseph Nye argues that barriers to entry into the cyber domain are so low that non-state actors and small states can play significant roles at low levels of cost. He points to three characteristics of cyber warfare, which distinguishes it from other kinds of traditional warfare: | |||
:1. High number of players | :1. High number of players | ||
:2. Ease of entry | :2. Ease of entry | ||
| Line 93: | Line 272: | ||
:*While governments will end up remaining the stronger actors, cyberspace is likely to increase the diffusion of power to non-state actors. | :*While governments will end up remaining the stronger actors, cyberspace is likely to increase the diffusion of power to non-state actors. | ||
=== Lynn === | |||
=== William Lynn === | |||
In his article, ''[http://www.foreignaffairs.com/articles/66552/william-j-lynn-iii/defending-a-new-domain Defending a New Domain, The Pentagon Strategy]'', William Lynn starts from the assumption that the US government's digital infrastructure gives the US critical advantages over other countries. On the other hand, reliance on computer infrastructures exposes the US to disruptive attacks. The strategy adopted by the Pentagon, according to Lynn, must be based on the peculiar features of threats in cyberspace. In fact, the distinctive characteristics of cyberspace have led the Pentagon to recognize it as a new domain of warfare, as critical to military operations as other more traditional domain like air, space and land. | In his article, ''[http://www.foreignaffairs.com/articles/66552/william-j-lynn-iii/defending-a-new-domain Defending a New Domain, The Pentagon Strategy]'', William Lynn starts from the assumption that the US government's digital infrastructure gives the US critical advantages over other countries. On the other hand, reliance on computer infrastructures exposes the US to disruptive attacks. The strategy adopted by the Pentagon, according to Lynn, must be based on the peculiar features of threats in cyberspace. In fact, the distinctive characteristics of cyberspace have led the Pentagon to recognize it as a new domain of warfare, as critical to military operations as other more traditional domain like air, space and land. | ||
| Line 99: | Line 279: | ||
:'''Government role''' | :'''Government role''' | ||
:*Cyber warfare is asymmetric. Cyber weapons can be obtained at a relatively low cost, with high potentiality for disruptive results. This leads to ineffectiveness of a traditional deterrence model based on the acquisition of offensive capabilities against potential attackers. | :*Cyber warfare is asymmetric. Cyber weapons can be obtained at a relatively low cost, with high potentiality for disruptive results. This leads to ineffectiveness of a traditional deterrence model based on the acquisition of offensive capabilities against potential attackers. | ||
:*Lynn focuses instead on '''“active defense”''' mechanisms, capable of anticipating intrusion and attacks. This should be implemented through the new unified Cyber Command. | :*Lynn focuses instead on '''“active defense”''' mechanisms, capable of anticipating intrusion and attacks. This should be implemented through the new unified [http://www.defense.gov/home/features/2010/0410_cybersec/ Cyber Command]. | ||
:'''Private sector and international level''' | :'''Private sector and international level''' | ||
| Line 105: | Line 285: | ||
:*In order to achieve the goal of enhanced security the Pentagon should further explore how major private companies can help the public sector in tackling cyber threats. Additionally, the US should also find ways to exploit the private sector's innovative capacity in information technology, especially since a dramatic importance in the cyber defense is predicated on the human factor, namely the availability of highly trained human resources. The dynamism and fast development capabilities of the private sector are also taken by Lynn as an example. | :*In order to achieve the goal of enhanced security the Pentagon should further explore how major private companies can help the public sector in tackling cyber threats. Additionally, the US should also find ways to exploit the private sector's innovative capacity in information technology, especially since a dramatic importance in the cyber defense is predicated on the human factor, namely the availability of highly trained human resources. The dynamism and fast development capabilities of the private sector are also taken by Lynn as an example. | ||
:*In addition to this internal connection between military and civilian infrastructures, Lynn also points out that any efforts made by the US must take into account allied countries in order to cooperate in the monitor of computer networks intrusions. | :*In addition to this internal connection between military and civilian infrastructures, Lynn also points out that any efforts made by the US must take into account allied countries in order to cooperate in the monitor of computer networks intrusions. | ||
=== Wesley Clark === | === Wesley Clark === | ||
| Line 110: | Line 291: | ||
''“Sabotaged circuits cannot be patched; they are the ultimate sleeper cell.”'' | ''“Sabotaged circuits cannot be patched; they are the ultimate sleeper cell.”'' | ||
General Clark's article, ''[http://cognosys.net/classes/fall10/cs446/resources/Securing%20the%20Information%20Highway-foreign-affairs-1109.pdf Securing the Information Highway]'', focuses on the problem of compromised hardware -- usually chips with rogue transistors | General Clark's article, ''[http://cognosys.net/classes/fall10/cs446/resources/Securing%20the%20Information%20Highway-foreign-affairs-1109.pdf Securing the Information Highway]'', focuses on the problem of compromised hardware -- usually computer chips with built-in rogue transistors that allow another party to gain control of a system. Clark believes this is the greatest threat for cyber security. | ||
*Software attacks, on the other hand, “are generally detectable, are mostly curable, and, until now, have been largely containable through the use of software patches." | *Software attacks, on the other hand, “are generally detectable, are mostly curable, and, until now, have been largely containable through the use of software patches." | ||
| Line 138: | Line 319: | ||
::Note that this doesn’t mean we have to manufacture everything here – that’s a practical impossibility given the demand. We just need to ensure foreign-made products are “authentic and secure.” | ::Note that this doesn’t mean we have to manufacture everything here – that’s a practical impossibility given the demand. We just need to ensure foreign-made products are “authentic and secure.” | ||
=== Knake === | === Robert Knake === | ||
In its report for the Council on Foreign Relations, | In its report for the Council on Foreign Relations, | ||
''[http://www.cfr.org/content/publications/attachments/Cybersecurity_CSR56.pdf Internet Governance in an Age of Cyber Insecurity]'', Knake examines the current position of the United States in dealing with cyber-security at the international level and the challenges faced by the international community. | ''[http://www.cfr.org/content/publications/attachments/Cybersecurity_CSR56.pdf Internet Governance in an Age of Cyber Insecurity]'', Knake examines the current position of the United States in dealing with cyber-security at the international level and the challenges faced by the international community. | ||
Knake points out that while the US have refused to cooperate at the international level on a new governance for the | Knake points out that while the US have refused to cooperate at the international level on a new governance for the Internet, China, Russia and other non democratic regimes have been organizing a united front to promote a new model for the Internet, tightly controlled by states. According to Knake, a free and open Internet is in the US’ national interest and therefore the government should actively fight the threats arising from cyber crime, espionage and warfare while at the same time preserving the democratic infrastructure of the web. | ||
In order to reach this goal Knake indicates three basic principles, to be implemented through a three-part agenda the US should implement: | In order to reach this goal Knake indicates three basic principles, to be implemented through a three-part agenda the US should implement: | ||
| Line 156: | Line 336: | ||
:'''1. Create a stronger sets of international regimes to fight crime in cyberspace''' | :'''1. Create a stronger sets of international regimes to fight crime in cyberspace''' | ||
::Knake appears to be a supporter of a hands-off approach to the Internet. He points out that so far the US has only maintained control of one necessary infrastructure component (the DNS, Domain Name System) which needs active management, but otherwise has taken the position that the role of the government should be limited. According to Knake this approach should be adapted at changing times and increased cyber threats at the international level. New times demand the development of new international instruments to fight cyber crime and implement real-time mechanisms for international cooperation in fighting and investigating cross-border attacks. | ::*Knake appears to be a supporter of a hands-off approach to the Internet. He points out that so far the US has only maintained control of one necessary infrastructure component (the DNS, Domain Name System) which needs active management, but otherwise has taken the position that the role of the government should be limited. | ||
:::*According to Knake this approach should be adapted at changing times and increased cyber threats at the international level. New times demand the development of new international instruments to fight cyber crime and implement real-time mechanisms for international cooperation in fighting and investigating cross-border attacks. | |||
::Russia has been pushing since 1998 for a UN treaty to address conflicts in cyberspace creating a centralized international body to tackle cyber security issues. Knake, however, opposes a state-centric intergovernmental organization in that contrary to US interests, but rather supports a cooperative solution involving non-governmental organizations and the private sector in the development of new norms and the implementation of a more secure infrastructure. | ::*Russia has been pushing since 1998 for a UN treaty to address conflicts in cyberspace creating a centralized international body to tackle cyber security issues. [http://www.nytimes.com/2009/06/28/world/28cyber.html?pagewanted=all NYT] | ||
:::*Knake, however, opposes a state-centric intergovernmental organization in that contrary to US interests, but rather supports a cooperative solution involving non-governmental organizations and the private sector in the development of new norms and the implementation of a more secure infrastructure. | |||
:::*In certain areas, however, governmental intervention is the only practicable solution, where decentralized and inclusive approach does not work. Cyber crime (and relating problems of investigating, apprehending and prosecuting cyber criminals) is one of these areas. Council of Europe's convention on cybercrime helped in establishing laws to criminalize computer crimes and a mechanism for cross-border cooperation. However, according to Knake, it did not lead to a reduction of cybercrime. Further, such convention only envisages bilateral and prosecutorial mechanisms, ineffective in preventing attacks or tackling an attack when it occurs. | |||
:: | ::*Knake suggested the creation of national level criminal laws and development of less formal mechanisms of cooperation through a “light” intergovernmental body. Knake's goal is a stronger international governance of the Internet, but “tailored to specifically address a narrow set of security concerns surrounding crime and warfare”. An approach clearly opposed to Russia's and China's “information security”. | ||
: | :'''2. Constrain state actors in cyberspace''' | ||
: | ::*In order to solve the attribution problem (i.e., the extreme difficulties in tracking the origin of attacks in the cyberspace) Knake suggests that US should commit to pursue criminal prosecution of citizens engaging in hacktivism against foreign countries. | ||
:::*Foreign states should do the same, and failure to cooperate in doing so should be deemed as a sign of complicity. States should be accountable for their actions, as well as those of their citizens and their systems. | |||
::In | ::*In the past decade US has been focusing on cybercrime and refused to enter into negotiations on warfare and espionage. | ||
:::*Knake says US should now overthrow the perception that US wants to maintain exploitation and attack capabilities at a level above other states. While keeping such capabilities is in the US interest, giving away such perception may be detrimental, and refusing in particular to enter into negotiations on state limitations to cyber warfare attracts critics. | |||
:::*Knake suggests a renewed engagement of the US, but not as set forth in current treaty options. The Russian proposal, for instance, would commit signatories to abstain from developing offensive cyber capabilities while not providing any mechanism for the verification of their compliance. His proposed solution would be not to focus on limiting state actors offensive capabilities, bur rather limiting their penetration into civilian infrastructures (power grids, financial infrastructures). | |||
: | :'''3. Secure the Internet's underlying technology''' | ||
::Knake suggests | ::*Knake suggests that it is now time to shift the focus of international and local attention from coordination and interoperability to security. | ||
:::*The development of more secure technical protocols is much needed, Knake argues, and the government should provide guidance in the technical area. | |||
:::*The private sector should be involved in a centralized forum established by the government to coordinate the Internet governance agenda, including big US corporations such as Microsoft and Symantec. | |||
== Mapping Onto the Four Quadrants == | == Mapping Onto the Four Quadrants == | ||
===Four Quadrants: Elaborated=== | ===Four Quadrants: Elaborated=== | ||
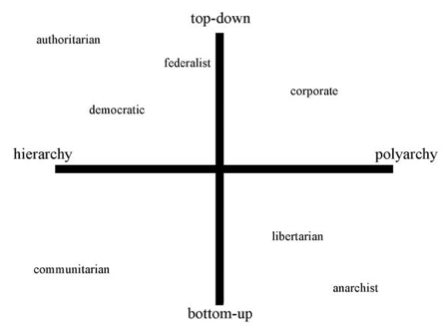
Professor Zittrain mapped existing political philosophies onto his four quadrants. The result was presented in his article: | Professor Zittrain mapped existing political philosophies onto his four quadrants. The result was presented in his article: | ||
[[Image:Four_Quadrants_Detail.png]] | [[Image:Four_Quadrants_Detail.png]] | ||
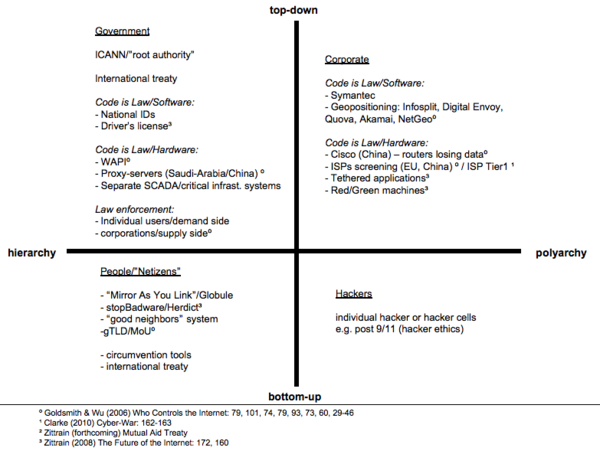
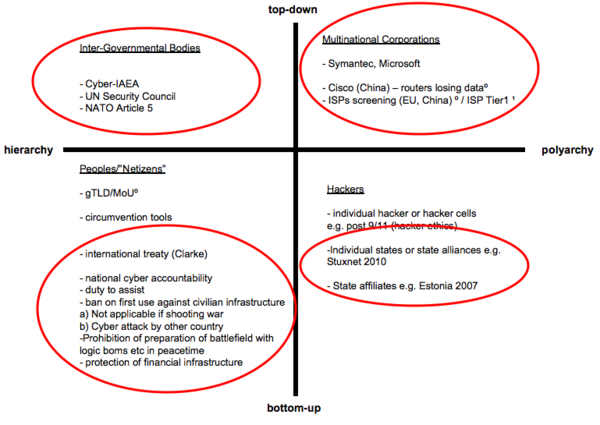
We have taken this framework and tried to determine which Internet groups generally occupy each quadrant. | |||
[[Image:chart1.png|600px]] | |||
:1. We believe that the first quadrant is the traditional domain of '''governments'''. Governments promulgate and enforce rules, and generally offer few or no alternatives. | |||
:2. The second quadrant is occupied by '''corporations''', who act similarly to governments but offer the choice between numerous systems. | |||
:3. '''Hackers''' are the best example of the third quadrant. These groups create their own hacker ethics from the bottom-up, and encourage polyarchy. | |||
:4. The fourth quadrant is occupied by "'''[http://en.wikipedia.org/wiki/Netizen Netizens]'''" -- active users of Internet sites like Wikipedia. These groups typically promulgate their own rules, but offer a more hierarchical structure. | |||
===Mapping the Proposals=== | ===Mapping the Proposals=== | ||
====''Why the mapping?''==== | |||
The four quadrants can be a useful tool to dissect each of the proposals examined above: placing each proposal on a map allows the reader to more fully understand the interests at stake, the actors involved, and the consequences of each approach. | |||
The mapping of the proposals is also helpful in understanding where each proposal actually stands, as opposed as where it purports to stand. In this respect, we argue that the perception of a proposal may determine how much support it can gain, but such perception does not necessarily capture all the implications of that proposal. | |||
====''Difficulties with Mapping''==== | |||
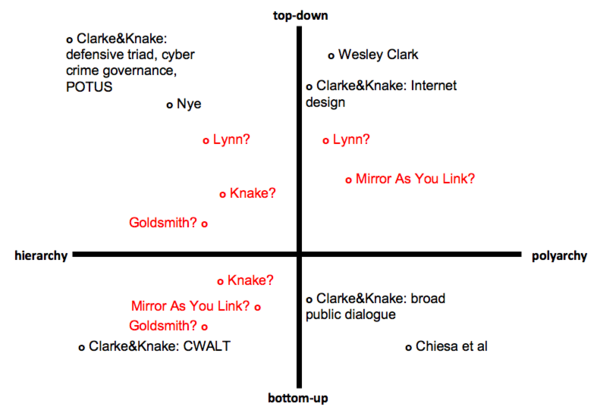
Consider Professor Zittrain's article: at a first glance the Mirror As You Link approach would clearly place his proposal in the fourth quadrant, due to the communitarian and distributed nature of the solution. However, it is also suggested that the practical implementation should not occur through an action by users, but through a basic technological change adopted by two major servers manufacturers, Microsoft and Apache (an "architectural" modification). Does this way of implementation place this proposal in the second quadrant along with other solutions enacted by corporate actors? Would an article called the Second Quadrant be perceived in the same way and gain the same support? | |||
[[Image:chart2.png|600px]] | |||
Clarke's solution for increasing the security of the US national network encompasses a nation-wide scanning and sanitization of all the communications entering, or passing through the US computer infrastructure. This solution appears to be a typical form of government action that would place this proposal in the first quadrant. On the other hand, Clarke argues that the proposed security barrier should not be managed by governmental authorities themselves, but rather by private actors entrusted to do so by the government. How would the role of private corporations in implementing Clarke;s solution affect their position on the four quadrants? Should they be moved to the second quadrant? Why would the privacy concerns expressed by Clarke be better assessed by a corporate solution? | |||
[[Image:chart3.png|600px]] | |||
If we take into consideration the proposed solutions (Clarke's and others) at the international level, it is even harder to identify their position on the map, and how their approach should be defined. When confronted with the plurality of state actors on the international scene, even proposals that focus on governmental intervention may be easily shifted to other parts of the map due to the very nature of intergovernmental interaction. | |||
[[Image:chart4.png|600px]] | |||
====''More Clear''==== | ====''More Clear''==== | ||
:'''Quadrant 1''' | :'''Quadrant 1''' | ||
:*'''Nye''': Nye's proposal appears to fall squarely in the first quadrant. He believes governmental authorities to be the most important actors in the cyber domain, and while he calls for the enhancement of private sector infrastructures' security, he seems to suggest that it should be done through government intervention. Furthermore, Nye do not believe that an international solution would be easily found. | :*'''Nye''': Nye's proposal appears to fall squarely in the first quadrant. He believes governmental authorities to be the most important actors in the cyber domain, and while he calls for the enhancement of private sector infrastructures' security, he seems to suggest that it should be done through government intervention. Furthermore, Nye do not believe that an international solution would be easily found. | ||
:*'''Clarke&Knake''': The proposal of Clarke and Nye to implement the Defensive Triad Strategy together with a stronger cetnralized role of POTUS in authorizing and monitoring cyber-activity including cybercrime falls clearly into Quadrant 1. It aims to create a more hierarchical, top-down structure within a democratic system. | |||
:'''Quadrant 2''' | :'''Quadrant 2''' | ||
:*'''Wesley Clark''': Clark's proposal clearly falls in the second quadrant. His call to diversify the digital infrastructure is a polyarchical solution. Additionally, Clark intends for the government to promulgate all of these rules, which is a top-down solution. | :*'''Wesley Clark''': Clark's proposal clearly falls in the second quadrant. His call to diversify the digital infrastructure is a polyarchical solution. Additionally, Clark intends for the government to promulgate all of these rules, which is a top-down solution. | ||
:*'''Clarke&Knake''': The idea of redesigning the Internet's architecture seems to be part of Quadrant 2. Despite a potential stronger governmental role, the polyarchical corporate sector would remain the key actor providing the infrastructure and top-down implementation. | |||
:'''Quadrant | :'''Quadrant 4''' | ||
:*'''CWALT''': this proposal from Clarke & Knake calls for nations to create rules for one another, which is a bottom-up approach, but is structured to prevent individual nations from pursuing other systems independently. | |||
====''Less Clear''==== | |||
:''' | '''Quadrant 1 or 2?''' | ||
:*'''Lynn''': His approach appears prima facie based on strong government intervention, which would place his proposal in the first quadrant. However, Lynn also stresses the importance of vital energies that can be found in the private sector, and in particular the need to actively involve in the prevention of cyber threats private actors having technological know-how and capabilities. | |||
'''Quadrant 1 or 4?''' | |||
'''Quadrant 4 or 1 | :*'''Clarke&Knake''': An international framework among states can fall either into Quadrant 1 or 4 depending on the perspective. As all of the actors are governments - authoritarian, liberal, or democratic - one could argue the CWALT falls within Quadrant 1. However, from an international relations point of view and the anarchy of the international system, a CWALT would exhibit more of a communitarian approach as a symbol of the notion of an international "community/society" and could therefore also be situated within Quadrant 4. | ||
:*'''Knake''': At a first sight Knake's set of proposals appears to fall within the fourth quadrant. He is in fact proposing a ''Networked and distributed approach'', to be implemented through the active involvement of a wide range of participants from the technical community, the private sector, as well as users and consumer groups, to shape policy and avoid state-centric processes. Not a single forum, at either national or international level, bur rather a range of forums. | :*'''Knake''': At a first sight Knake's set of proposals appears to fall within the fourth quadrant. He is in fact proposing a ''Networked and distributed approach'', to be implemented through the active involvement of a wide range of participants from the technical community, the private sector, as well as users and consumer groups, to shape policy and avoid state-centric processes. Not a single forum, at either national or international level, bur rather a range of forums. | ||
:::At a deeper reading of Knake's arguments, however, it appears more clear that - in his mind - the US should nurture and indirectly control his proposed "light intergovernmental body". When Knake urges the US to be involved in international negotiations concerning the fight of cyber crime, he does so to avoid a "perception" that would eventually turn out to be detrimental to the US. Even private actors, such as Microsoft and Symantec, would be captured in the governmental sphere, by being made aware of the goals of the US government and actively help in achieving such goals. | :::*At a deeper reading of Knake's arguments, however, it appears more clear that - in his mind - the US should nurture and indirectly control his proposed "light intergovernmental body". When Knake urges the US to be involved in international negotiations concerning the fight of cyber crime, he does so to avoid a "perception" that would eventually turn out to be detrimental to the US. Even private actors, such as Microsoft and Symantec, would be captured in the governmental sphere, by being made aware of the goals of the US government and actively help in achieving such goals. | ||
:*'''Goldsmith''': His approach appears to rely heavily on communitarian, self-governed mechanisms to face the new cyber threats, which would place it in the fourth quadrant. However, Goldsmith himself acknowledges that governmental intervention is to some extent necessary to support and guarantee the efficacy of community organizations. | |||
:*''' | '''Quadrant 2 or 4?''' | ||
:*'''Mirror As You Link''': Professor Zittrain's proposal allows Internet users to download a website from different servers, which seems to be a polyarchical solution. Additionally, this system needs to be adopted and maintained by web server vendors, which are top-down institutions. This seems to indicate that Mirror As You Link is a first quadrant solution. It could be argued, however, that this system also falls in the fourth quadrant. Mirror As You Link could be adopted in such a way that rules are agreed upon by the Internet users themselves, and it's unclear whether there would be an ability for users to choose between multiple linking regimes. | |||
'''Quadrant 3 or 4?''' | |||
:*'''Clarke&Knake''': The idea of a broad public dialogue is clearly closer at the bottom-up end of the vertical axis but seems to move along the horizontal one. The question is to what degree the public at large can be engaged or if the technical required knowhow will limit the extent to the breadth of the dialogue. | |||
====''A New Mapping''==== | |||
How did the use of the four quadrants tool impact our analysis? Below is our attempt to map all of the approaches onto a single chart: | |||
[[Image:ourchart1.png|600px]] | |||
Latest revision as of 10:46, 13 August 2020
Introduction
Cyber-security has emerged as a hot topic for social and legal scholars. Despite the widespread interest, it remains unclear what the problem entails and how we can work towards one or more solutions. This Wiki attempts to define key terms used in cyber-security, clarify the problems and solutions identified by various scholars, and view these approaches through Professor Zittrain's four-quadrants framework.
Terms
Definitions
Cyber as a prefix refers to electronic and computer-based technology. Cyber-space is “an operational domain framed by use of electronics to … exploit information via interconnected systems and their associated infra structure.” (Kuehl cited in Joseph Nye, 2010: 3) According to Raul Chiesa there is a
- “need to avoid terms such as ‘real-world’ and ‘virtual reality’, which have been and still are abused, apart from being evidently wrong. In fact, those who commit electronic attacks not only don’t consider there to be any difference between the two, but indeed the second category does not exist, as whatever takes place on a network, Web, or ‘behind the scenes’ of telephone exchanges or lines is not at all virtual but real. We believe it to be more precise and less misleading to talk about electronic world and physical world.” (Chiesa et al, 2009: XXII)
Cyber-space is therefore “a unique hybrid regime of physical and virtual properties,” hardware and software, which is all of the computer networks in the world including the Internet plus the other networks separate and not linked to the Internet. (Nye, 2010: 3; Clarke and Knake, 2010: 70)
Cyber-security can be divided to face four major threats: espionage, crime, cyber war, and cyber terrorism (Nye, 2010: 16). The possibility for the existence of a threat in the first place goes back to three sources: “(1) flaws in the design of the Internet; (2) flaws in the hardware and software; and (3) the move to put more and more critical systems online.” (Clarke and Knake, 2010: 73)
Cyber-warfare has been defined by Clarke and Knake as “the unauthorized penetration by, on behalf of, or in support of, a government into another nation’s computer or network, or any other activity affecting a computer system, in which the purpose is to add, alter, or falsify data, or cause the disruption of or damage to a computer, or network device, or the objects a computer system controls.” (Clarke and Knake, 2010: 227)
The Hackers Profiling Project of the United Nations Interregional Crime and Justice Research Institute (UNICRI) proposes a typology for actors in cyber-space. They identify Wannabee Lamer; Script-kiddie; the “37337 K-rAd iRC #hack 0-day exploitz” guy; Cracker; Ethical Hacker; Quiet, paranoid, and skilled hacker; Industrial Spy; Cyber-warrior; Government Agent, Military Hacker. (Chiesa et al, 2009: 52-56, 61) As these types sometimes overlap, they can be reduced to the following three groups relevant in cyber-warfare:
- Cyber-warrior: private actors who are highly skilled mercenaries hacking for money or for ideals
- Government Agent: “the civilian state actor” - hackers employed by a country’s civilian government for (counter)espionage, information monitoring of governments, terrorist groups, strategic industries, and individuals without the authority to cause physical death through the use of the electronic world. (Chiesa et al, 2009: 56)
- Military Hacker: “the military state actors” - hackers employed by a country’s military potentially with the authority to cause physical death through the use of the electronic world in times of war.
This categorization is more elaborate than Clarke and Knake’s general usage of the term "cyber warriors," which simply distinguishes between criminals and military hackers. The UNICRI-based categories provide greater clarity to differentiate between the various actors in cyber-warfare, state and non-state as well as military and civilian.
Cyber Equilibrium 1.0. In the 20th century the cyber environment from a hacker’s point of view can be described as an equilibrium between “three different entities in our society – superpowers that are competing against each other: the hacker community, governments, and the Internet community in general […] a shift in the balance of power and consequently concentrating it all in one group’s hands […] is unacceptable for hackers, as power should always be equally shared between the three entities […] Hackers have no concept of a hierarchical, authoritarian (vertical) relation between the three entities, but that only an equal relationship (horizontal), peer to peer, can be considered synonymous with true democracy.” (Chiesa et al, 2009: 114-15)
Hacker ethics played an important role. (Chiesa et al, 2009: 172-76) This ideal picture began to crack at the end of the 1990s when hacking became increasingly politicized. Before hacking was considered apolitical by its nature in the sense that the political actions of hackers were reduced to ensuring the aforementioned equilibrium. However, eventually “hacktivism” emerged, political activism through hacking. Hacking moved from being an end in itself to being a means for achieving a different political end. The first HackMeeeting took place in Florence in 1997. It remains unclear if the events in Estonia in 2007 were also an expression of a nationalist Russian hacktivism. At the same time, the hacker crackdowns started driving hackers into the underground. (Chiesa et al, 2009: 120, 162)
Cyber Equilibrium 2.0. The 21st century paints a different picture. During most of the 20th century the vast majority of Internet users were Westerners who shared a common set of norms. That is why the equilibrium was a representation of citizens vs. governments or rather the individual vs. the state. The cultural difference between a hacker in the US, the UK, or Spain was much smaller than their cultural similarity in opposing their respective government in restricting their hacking activity. But with the rapid expansion of Internet users around the globe and the politicization of hacking, this has changed. A new type of alliance has emerged as illustrated by the activities of hackers after 9/11 in support of the U.S. government or the Russian hackers supporting the Russian government during its war with Georgia in 2008. While the Cyber Equilibrium 1.0 continues to exist in the various societies though less openly as a result of the crackdowns, it is now complemented by an internationalized Cyber Equilibrium 2.0 that resembles more a classic balance of power concept.
Cyber-power “is ‘the ability to use cyberspace to create advantages and influence events in other operational environments and across the instruments of power.’ Cyber power can be used to produce preferred outcomes within cyberspace or it can use cyber instruments to produce preferred outcomes in other domains outside cyberspace.” (Kuehl cited in Nye, 2010: 4) A good overview of the different techniques of hacking is given in UNICRI’s Profiling Hackers – The Science of Criminal Profiling as Applied to the World of Hacking. (Chiesa et al, 2009: 20-32) In addition to power derived from the mastering of hacking techniques, a legitimate source of power is the root authority which is “the power to issue orders respecting domain names and numbers and have those orders obeyed.” (Goldsmith and Wu, 2008: 32) This power is currently in the hands of ICANN, which is under contract of the U.S. Department of Commerce. Given the U.S. government’s interpretation of such contractual relationships when dealing with Jon Postel and the MoUvement in the 1990s, it is safe to argue that through ICANN, it is the U.S. government that controls the root authority (Goldsmith and Wu, 2008: 29-46).
The Internet as the biggest network in cyber-space is designed to be “open, minimalist, and neutral.” (Goldsmith and Wu, 2008: 23) Similar to the constructivist critique of the realist balance of power, the Internet’s architecture is contingent, however, and “ a choice – not fate, not destiny, and not natural law.” (Goldsmith and Wu, 2008: 90) Alternative manifestations can be found in China or Saudi-Arabia. The “bordered Internet” that emerged through national changes of the Internet’s architecture is the result of national laws, technological developments enabling the implementation of certain policies, and on a broader level the preferences of different cultures. (Goldsmith and Wu, 2008: 149-50)
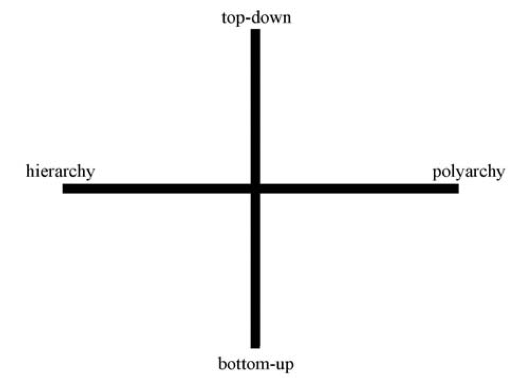
The Four Quadrants
In his article, The Fourth Quadrant, Professor Zittrain develops a four quadrant framework for thinking about the Internet. This framework looks at two criteria: (1) how generative something is, and (2) how singular it is.
The generativity of a phenomena is assessed on a scale from entirely “top-down” to entirely “bottom-up.” The range of singularity runs from “hierarchy” to “polyarchy.” This is captured in the following chart from the article:
Professor Zittrain uses precise (sometimes unconventional) definitions of these terms:
- Top-down: systems in which “there is a separation between those who make the rules and those who live under them . . . .”
- Bottom-up: systems where the rules can come from any person without separation between the people who make the rules and people who live under them.
- Hierarchy: a system in which "gatekeepers control the allocation of attention and resources to an idea" or "a system for which there is no alternative, either because it does not exist, because it would be too costly, or because law precludes it."
- Note: to see how Professor Zittrain's definition of hierarchy might differ from the lay person understanding, see Wikipedia.
- Polyarchy: being able to choose between multiple regimes or systems and pursue ideas independently.
For more on this system, see The Future of the Internet and How to Stop It, chapter 4.
Proposals
This section will summarize the proposals of various cyber-security authors. The next section will attempt to map these proposals onto Professor Zittrain's framework.
Richard Clarke & Robert Knake
In their book Cyber War Richard Clarke and Robert Knake discuss “the next great threat to national security.”
Clarke and Knake identify the following key vulnerabilities:
- I) Internet addressing system using the Domain Name System
- II) routing among ISPs, the Border Gateway Protocol
- III) openness, unencrypted Internet
- IV) propagation of intentionally malicious traffic, malware
- V) one big network with a decentralized design
They recount the cyber attack on Syria on 6 September 2007, the DDoS attack on Estonia in May 2007, and on Georgia in 2008. Aware of the near impossibility to attribute an attack to its source, they outline the range of possible means of attacks such as logic bombs, ghost nets, and botnets. Their book tells the story of the internal fight within the US government over who has authority in the cyber realm ultimately resulting in the creation of the U.S. Cyber Command headed by the head of the NSA. The USG also adopted a National Military Strategy for Cyber Operations.
Some of what seemed far-fetched in the book (published in April 2010) has since become reality:
Wikileaks:
- The “sneakernet threat” posed by the air gap between the unclassified and secret level network SIPRNET is at the core of the current Wikileaks affair (p. 171).
- BBC: SIPRNET
Stuxnet:
- The description of a manipulation of generators resembles the latest analyzes of the Stuxnet virus altering centrifuges (p. 100).
- The Economist: A Worm in the Centrifuge
- The Atlantic: Stuxnet
- For more information on major cyber attacks from the past few years, see the recent article in NewScientist. The article looked at each attack's level of sophistication and the likelihood that it was state-sponsored, presenting its results in a useful image.
KEY QUESTIONS (pp. 152-154)
- 1) What do we do if we wake up one day and find the western half of the U.S. without electrical power as the result of a cyber attack?
- 2) Is the advent of cyber war a good thing, or does it place us at a disadvantage?
- 3) Do we envision the use of cyber war weapons only in response to the use of cyber war weapons against us?
- 4) Are cyber weapons something that we will employ routinely in both small and large conflicts? Will we use them early in a conflict because they give us a unique advantage in seeking our goals, such as maybe affecting a rapid end to the conflict?
- 5) Do we think we want to have plans and capabilities to conduct “stand-alone” cyber war against another nation? And will we fight in cyberspace even when we’re not shooting at the other side in physical space?
- 6) Do we see cyber space as another domain (like the sea, airspace, or outer space) in which we must be military dominant and in which we will engage an opponent while simultaneously conducting operations in other domains?
- 7) How surely do we have to identify who attacked us in cyberspace before we respond? What standards will we use for these identifications?
- 8) Will we ever hide the fact that it was us who attacked with cyber weapons?
- 9) Should we be hacking into other nations’ networks in peacetime? If so, should there be any constraints on what we would do in peacetime?
- 10) What do we do if we find that other nations have hacked into our networks in peacetime? What if they left behind logic bombs in our infrastructure networks?
- 11) Do we intend to use cyber weapons primarily or initially against military targets only? How do we define military targets?
- 12) Or do we see the utility of cyber weapons being their ability to inflict disruption on the economic infrastructure or the society at large?
- 13) What is the importance of avoiding collateral damage with our cyber weapons? How might avoiding it limit our use of the weapons?
- 14) If we are attacked with cyber weapons, under what circumstances would, or should, we respond with kinetic weapons? How much of the answer to that question should be publicly known in advance?
- 15) What kind of goals specific to the employment of cyber weapons would we want to achieve if we conducted cyber war, either in conjunction with kinetic war or as a stand-alone activity?
- 16) Should the line between peace and cyber war be brightly delineated, or is there an advantage to us in blurring that distinction?
- 17) Would we fight cyber war in a coalition with other nations, helping to defend their cyberspace and sharing our cyber weapons, tactics, and targets?
- 18) What level of command authority should authorize the use of cyber weapons, select the weapons, approve the targets?
- 19) Are there types of targets that we believe should not be attacked using cyber weapons? Do we attack them anyway if similar U.S. facilities are hit first by cyber or other weapons?
- 20) How do we signal our intentions with regard to cyber weapons in peacetime and in crisis? Are there ways that we can use our possession of cyber weapons to deter an opponent?
- 21) If an opponent is successful in launching a widespread, disabling attack on our military or on our economic infrastructure, how does that affect our other military and political strategies?
PROPOSALS
After a chapter on what the authors call “Defensive Triad Strategy”, a chapter on the limits of offensive use, and a chapter on an international framework for a cyber peace, the following recommendations conclude the book:
- 1) Thinking About the Unseeable:
- A broad public dialogue to raise awareness and allow for an open discussion of strategies and the balance of values they represent
- 2) The Defensive Triad:
- i) stop malware on the Internet at the backbone ISPs
- ii) hardens the controls of the electric grid [while it is unclear why the authors do not include all SCADA controlled systems]
- iii) increases the DoD networks and integrity of its weapons
- 3) Cyber Crime:
- Combat cyber crime, reducing the economic incentive, prevent safe havens
- 4) Cyber War Limitation Treaty (CWALT):
- CWALT I – initial agreement
- - establish a Cyber Risk Reduction Center to exchange information and provide nations with assistance;
- - create as international-law concepts the obligation to assist and national cyber accountability;
- - impose a ban on first use cyber attacks against civilian infrastructure, a ban that would be lifted against another nation when (a) the two nations were in a shooting war, or (b) the defending nation had been attacked by the other nation with cyber weapons;
- - prohibit the preparation of the battlefield in peacetime by the emplacement of trapdoors or logic bombs on civilian infrastructure, including electric grids, railroads, etc.; and
- - prohibit altering data or damaging networks of financial institutions at any time, including the preparation to do so by the emplacement of logic bombs
- CWALT I – initial agreement
- 5) A New Internet Architecture
- 6) POTUS: establish clear lines of authority with the President at the top and required to approve emplacement of logic bombs, trapdoors, etc.
Jonathan Zittrain
Professor Zittrain begins his forthcoming article, A Mutual Aid Treaty for the Internet*, by describing mutual aid theory broadly and applying it to individuals on the Internet. By taking mutually beneficial, reciprocal actions, individual Internet participants can deal with real problems more efficiently.
This mutual aid framework is then extended to the World Wide Web. To ensure that cyber attacks cannot take down a website, Professor Zittrain proposes “Mirror As You Link.” This proposal takes the following form:
- 1. You visit a website.
- 2. The website appears on your computer.
- 3. As the site loads, your computer follows any links on the page and makes a local copy of these pages.
- 4. If a link no longer works, you can ask the linking site “to show you its best rendition of what you’re missing at the linked site.”
This system would require a change in the code, modifying the way Web servers work. Because Microsoft and Apache control 80% of the web server market, however, this would not be difficult. Additionally, if someone didn’t want their website to participate in Mirror As You Link, they could choose to block your computer from making a local copy.
-*This piece isn't currently available on the Internet. For a brief summary of these arguments see Professor Zittrain's New York Times piece on the subject, What Websites Can Do.
Jack Goldsmith
There are two relevant pieces by Jack Goldsmith in which he explores his thoughts on cyber security: the book he coauthored with Tim Wu, Who Controls The Internet?: Illusions of a Borderless World, and a recent article published in The New Republic titled The New Vulnerability.
Who Controls the Internet
Globalization has diminished the importance of borders, territory and locations, and has undermined the role of nation state's governments as the central institution for the governance and regulation of human affairs. The Internet has been seen as the catalyst of globalization and therefore it is essential in re-assessing if, and how, the role of governments has changed. Goldsmith and Wu conclude that physical coercion by government, which is a feature of traditional legal systems, has not been affected by the Internet and by globalization and remains today more important than expected. A number of examples gives evidence of this allegation: from the actions taken by Chinese government against dissidents, to the softer approach taken by western governments in inducing ISP to filter offensive communications and fighting P2P file sharing.
- The role of governments
- Goldsmith and Wu contend that governmental powers around the globe are striving to shape the architecture of the Internet through the use of their coercive power. This is leading to the de facto establishment of different local networks, more or less far from the open, free and worldwide Internet we have seen so far.
- According to this thesis, the openness of the Internet is not an inherent feature of the architecture, but rather a contingency due to the governmental coercion model that has prevailed so far. The differences between models for controlling the Internet would lead to a new technological cold war, where each side would push its own model for architecting the Internet, with the result of transforming the Internet into a collection of nation-state networks, separate from each other for many purposes.
- The role of communities
- In spite of the prominent role that governments still have on the Internet, Goldsmith and Wu suggest that private self-governing communities can still be an alternative to traditional government.
- At the same time, they suggest that this alternative governance model based on social norms, morality and the market cannot survive without an “underlying system of territorial government and physical coercion”. ICANN is brought as an example of this: a self-governance model based on technology and technocracy has managed to emerge and survive on the basis of the guarantees provided by the US government.
- Cybercrime
- In this context of nation-states networks, the book still calls for a global solution to cybercrime, a solution that would establish international legal instruments prohibiting computer invasion and disruption and set standards for inter-governmental cooperation.
- However, the authors also points at the inefficacy of a traditional international treaty in tackling cyber threats. The one example currently in place, for instance, the Council of Europe's Cybercrime Convention, has only been implemented by a scarce number of states and the response mechanisms set forth therein are deemed to be inappropriate.
- Cybercrime: an architectural solution
- The conclusion reached by Goldsmith and Wu is that the future of the Internet's security is not likely to rest on a traditional international treaty, but rather on an architectural solution.
- A “global law”, it is argued, already exists and it is the domain name system managed by ICANN. ICANN has been portrayed by the US as a form of bottom-up governance, serving and drawing inputs from the Internet “community” in the spirit of self-regulation.
- It is also pointed out that along the years the US has abandoned the rhetoric about a self-governed ICANN and has asserted that the control over ICANN will not be relinquished. While Goldsmith and Wu do not take a position on the outcome of the battle over control of ICANN, they stress that, as a matter of fact, the actors of such battle are nation-states rather than Internet communities and private companies.
The New Vulnerability
In a recent article published in The New Republic, Goldsmith takes a stand on Clarke's book Cyber War: The Next Threat to National Security and What to Do About It". The main areas of criticism in Clarke's approach indicated by Goldsmith are the following:
- Excessive focus on cyber war
- The terrorism threat is underestimated
- Greatest cyber threats come instead from espionage and theft
- Private actors are becoming more dangerous and sophisticated
- Potentiality of enormous economic damages
On the other hand, Goldsmith identifies several distinct difficulties that the US faces in tackling the new cyber threats:
- Companies underinvest in cyber safety: private profit vs. larger national interest
- Government fails to regulate software quality and service providers to avoid raising the costs of Internet access
- US skepticism in extensive Government action prevents a governmental involvement in defending private computer networks
Joseph Nye
In his article, Cyber Power, Joseph Nye argues that barriers to entry into the cyber domain are so low that non-state actors and small states can play significant roles at low levels of cost. He points to three characteristics of cyber warfare, which distinguishes it from other kinds of traditional warfare:
- 1. High number of players
- 2. Ease of entry
- 3. Opportunity for concealment
Each actor in the cyber domain has, according to Nye, specific powers and different sets of vulnerabilities, as shown in this chart from Nye's article:
Providing security is a classic function of government according to Nye, and increasing insecurity is believed to lead to an increased role of government in cyberspace. Nye indicates four major threats that should lead in principle to different solutions:
- 1. Economic espionage
- 2. Crime
- 3. Cyber war
- 4. Cyber terrorism
According to Nye, currently the highest costs come from the first two categories (economic espionage and crime), i.e., crimes committed by individual and small groups targeting civilian infrastructures and organizations. However, Nye envisages a change in the upcoming future, with cyberwar and cyber terrorism gaining importance.
- Nye's proposals
- Cyberwar:
- can be managed through inter-state deterrence, along with offensive capabilities to be used in the event that deterrence fails.
- can be regulated in the medium/long term through evolving norms of warfare comparable to the ones developed in relation to traditional warfare, such as proportionality.
- Cyber terrorism:
- is harder to contrast.
- Insofar as the attacks are directed against private infrastructures and organization, the threat can be dealt by incentivizing private actors, particularly owners of strategic infrastructure, to join secure systems rather than relying on the open Internet.
- International treaties:
- Large scale formal treaties regulating cyberspace, according to Nye, are unlikely at the moment.
- While governments will end up remaining the stronger actors, cyberspace is likely to increase the diffusion of power to non-state actors.
William Lynn
In his article, Defending a New Domain, The Pentagon Strategy, William Lynn starts from the assumption that the US government's digital infrastructure gives the US critical advantages over other countries. On the other hand, reliance on computer infrastructures exposes the US to disruptive attacks. The strategy adopted by the Pentagon, according to Lynn, must be based on the peculiar features of threats in cyberspace. In fact, the distinctive characteristics of cyberspace have led the Pentagon to recognize it as a new domain of warfare, as critical to military operations as other more traditional domain like air, space and land.
- Government role
- Cyber warfare is asymmetric. Cyber weapons can be obtained at a relatively low cost, with high potentiality for disruptive results. This leads to ineffectiveness of a traditional deterrence model based on the acquisition of offensive capabilities against potential attackers.
- Lynn focuses instead on “active defense” mechanisms, capable of anticipating intrusion and attacks. This should be implemented through the new unified Cyber Command.
- Private sector and international level
- Lynn recognizes that any plans aimed at defending military networks would be ineffective if civilian infrastructures are not secured against potential attacks, which could also be a target in military conflicts.
- In order to achieve the goal of enhanced security the Pentagon should further explore how major private companies can help the public sector in tackling cyber threats. Additionally, the US should also find ways to exploit the private sector's innovative capacity in information technology, especially since a dramatic importance in the cyber defense is predicated on the human factor, namely the availability of highly trained human resources. The dynamism and fast development capabilities of the private sector are also taken by Lynn as an example.
- In addition to this internal connection between military and civilian infrastructures, Lynn also points out that any efforts made by the US must take into account allied countries in order to cooperate in the monitor of computer networks intrusions.
Wesley Clark
“Sabotaged circuits cannot be patched; they are the ultimate sleeper cell.”
General Clark's article, Securing the Information Highway, focuses on the problem of compromised hardware -- usually computer chips with built-in rogue transistors that allow another party to gain control of a system. Clark believes this is the greatest threat for cyber security.
- Software attacks, on the other hand, “are generally detectable, are mostly curable, and, until now, have been largely containable through the use of software patches."
- Two challenges with enhancing hardware security:
- 1. Ensuring authenticity.
- 2. Detecting malevolent function inside the device.
- Other problems that are making things worse:
- 1. Americans have a false sense of security.
- 2. We’re not doing anything – the longer we wait, the better adversaries will get.
Clark’s Solution:
We need to learn from the open-source community and create security standards that allow us to quickly discover and correct security flaws.
- We “need to endow U.S. networks, software, and even hardware with a digital immune system—one that is openly described and freely discussed.”
- Clark proposes a two-step approach:
- 1. Diversify the digital infrastructure.
- We need more diversity in both hardware and software (operating systems) to make it harder to attack large sections at once.
- 2. Secure the supply chain for hardware.
- Embed compact authentication codes directly into devices.
- Anti-tamper safeguards after devices are produced
- 1. Diversify the digital infrastructure.
- Note that this doesn’t mean we have to manufacture everything here – that’s a practical impossibility given the demand. We just need to ensure foreign-made products are “authentic and secure.”
Robert Knake
In its report for the Council on Foreign Relations, Internet Governance in an Age of Cyber Insecurity, Knake examines the current position of the United States in dealing with cyber-security at the international level and the challenges faced by the international community.
Knake points out that while the US have refused to cooperate at the international level on a new governance for the Internet, China, Russia and other non democratic regimes have been organizing a united front to promote a new model for the Internet, tightly controlled by states. According to Knake, a free and open Internet is in the US’ national interest and therefore the government should actively fight the threats arising from cyber crime, espionage and warfare while at the same time preserving the democratic infrastructure of the web.
In order to reach this goal Knake indicates three basic principles, to be implemented through a three-part agenda the US should implement:
- 1. Take a networked and distributed approach
- 2. Establish accountability of states for their actions, the actions of their citizens, and their systems
- 3. Start cleaning up the US national network
The above three principles should be implemented through the following three-part agenda:
- 1. Create a stronger sets of international regimes to fight crime in cyberspace
- Knake appears to be a supporter of a hands-off approach to the Internet. He points out that so far the US has only maintained control of one necessary infrastructure component (the DNS, Domain Name System) which needs active management, but otherwise has taken the position that the role of the government should be limited.
- According to Knake this approach should be adapted at changing times and increased cyber threats at the international level. New times demand the development of new international instruments to fight cyber crime and implement real-time mechanisms for international cooperation in fighting and investigating cross-border attacks.
- Russia has been pushing since 1998 for a UN treaty to address conflicts in cyberspace creating a centralized international body to tackle cyber security issues. NYT
- Knake, however, opposes a state-centric intergovernmental organization in that contrary to US interests, but rather supports a cooperative solution involving non-governmental organizations and the private sector in the development of new norms and the implementation of a more secure infrastructure.
- In certain areas, however, governmental intervention is the only practicable solution, where decentralized and inclusive approach does not work. Cyber crime (and relating problems of investigating, apprehending and prosecuting cyber criminals) is one of these areas. Council of Europe's convention on cybercrime helped in establishing laws to criminalize computer crimes and a mechanism for cross-border cooperation. However, according to Knake, it did not lead to a reduction of cybercrime. Further, such convention only envisages bilateral and prosecutorial mechanisms, ineffective in preventing attacks or tackling an attack when it occurs.
- Knake suggested the creation of national level criminal laws and development of less formal mechanisms of cooperation through a “light” intergovernmental body. Knake's goal is a stronger international governance of the Internet, but “tailored to specifically address a narrow set of security concerns surrounding crime and warfare”. An approach clearly opposed to Russia's and China's “information security”.
- 2. Constrain state actors in cyberspace
- In order to solve the attribution problem (i.e., the extreme difficulties in tracking the origin of attacks in the cyberspace) Knake suggests that US should commit to pursue criminal prosecution of citizens engaging in hacktivism against foreign countries.
- Foreign states should do the same, and failure to cooperate in doing so should be deemed as a sign of complicity. States should be accountable for their actions, as well as those of their citizens and their systems.
- In the past decade US has been focusing on cybercrime and refused to enter into negotiations on warfare and espionage.
- Knake says US should now overthrow the perception that US wants to maintain exploitation and attack capabilities at a level above other states. While keeping such capabilities is in the US interest, giving away such perception may be detrimental, and refusing in particular to enter into negotiations on state limitations to cyber warfare attracts critics.
- Knake suggests a renewed engagement of the US, but not as set forth in current treaty options. The Russian proposal, for instance, would commit signatories to abstain from developing offensive cyber capabilities while not providing any mechanism for the verification of their compliance. His proposed solution would be not to focus on limiting state actors offensive capabilities, bur rather limiting their penetration into civilian infrastructures (power grids, financial infrastructures).
- 3. Secure the Internet's underlying technology
- Knake suggests that it is now time to shift the focus of international and local attention from coordination and interoperability to security.
- The development of more secure technical protocols is much needed, Knake argues, and the government should provide guidance in the technical area.
- The private sector should be involved in a centralized forum established by the government to coordinate the Internet governance agenda, including big US corporations such as Microsoft and Symantec.
Mapping Onto the Four Quadrants
Four Quadrants: Elaborated
Professor Zittrain mapped existing political philosophies onto his four quadrants. The result was presented in his article:
We have taken this framework and tried to determine which Internet groups generally occupy each quadrant.
- 1. We believe that the first quadrant is the traditional domain of governments. Governments promulgate and enforce rules, and generally offer few or no alternatives.
- 2. The second quadrant is occupied by corporations, who act similarly to governments but offer the choice between numerous systems.
- 3. Hackers are the best example of the third quadrant. These groups create their own hacker ethics from the bottom-up, and encourage polyarchy.
- 4. The fourth quadrant is occupied by "Netizens" -- active users of Internet sites like Wikipedia. These groups typically promulgate their own rules, but offer a more hierarchical structure.
Mapping the Proposals
Why the mapping?
The four quadrants can be a useful tool to dissect each of the proposals examined above: placing each proposal on a map allows the reader to more fully understand the interests at stake, the actors involved, and the consequences of each approach. The mapping of the proposals is also helpful in understanding where each proposal actually stands, as opposed as where it purports to stand. In this respect, we argue that the perception of a proposal may determine how much support it can gain, but such perception does not necessarily capture all the implications of that proposal.
Difficulties with Mapping
Consider Professor Zittrain's article: at a first glance the Mirror As You Link approach would clearly place his proposal in the fourth quadrant, due to the communitarian and distributed nature of the solution. However, it is also suggested that the practical implementation should not occur through an action by users, but through a basic technological change adopted by two major servers manufacturers, Microsoft and Apache (an "architectural" modification). Does this way of implementation place this proposal in the second quadrant along with other solutions enacted by corporate actors? Would an article called the Second Quadrant be perceived in the same way and gain the same support?
Clarke's solution for increasing the security of the US national network encompasses a nation-wide scanning and sanitization of all the communications entering, or passing through the US computer infrastructure. This solution appears to be a typical form of government action that would place this proposal in the first quadrant. On the other hand, Clarke argues that the proposed security barrier should not be managed by governmental authorities themselves, but rather by private actors entrusted to do so by the government. How would the role of private corporations in implementing Clarke;s solution affect their position on the four quadrants? Should they be moved to the second quadrant? Why would the privacy concerns expressed by Clarke be better assessed by a corporate solution?
If we take into consideration the proposed solutions (Clarke's and others) at the international level, it is even harder to identify their position on the map, and how their approach should be defined. When confronted with the plurality of state actors on the international scene, even proposals that focus on governmental intervention may be easily shifted to other parts of the map due to the very nature of intergovernmental interaction.
More Clear
- Quadrant 1
- Nye: Nye's proposal appears to fall squarely in the first quadrant. He believes governmental authorities to be the most important actors in the cyber domain, and while he calls for the enhancement of private sector infrastructures' security, he seems to suggest that it should be done through government intervention. Furthermore, Nye do not believe that an international solution would be easily found.
- Clarke&Knake: The proposal of Clarke and Nye to implement the Defensive Triad Strategy together with a stronger cetnralized role of POTUS in authorizing and monitoring cyber-activity including cybercrime falls clearly into Quadrant 1. It aims to create a more hierarchical, top-down structure within a democratic system.
- Quadrant 2
- Wesley Clark: Clark's proposal clearly falls in the second quadrant. His call to diversify the digital infrastructure is a polyarchical solution. Additionally, Clark intends for the government to promulgate all of these rules, which is a top-down solution.
- Clarke&Knake: The idea of redesigning the Internet's architecture seems to be part of Quadrant 2. Despite a potential stronger governmental role, the polyarchical corporate sector would remain the key actor providing the infrastructure and top-down implementation.
- Quadrant 4
- CWALT: this proposal from Clarke & Knake calls for nations to create rules for one another, which is a bottom-up approach, but is structured to prevent individual nations from pursuing other systems independently.
Less Clear
Quadrant 1 or 2?
- Lynn: His approach appears prima facie based on strong government intervention, which would place his proposal in the first quadrant. However, Lynn also stresses the importance of vital energies that can be found in the private sector, and in particular the need to actively involve in the prevention of cyber threats private actors having technological know-how and capabilities.
Quadrant 1 or 4?
- Clarke&Knake: An international framework among states can fall either into Quadrant 1 or 4 depending on the perspective. As all of the actors are governments - authoritarian, liberal, or democratic - one could argue the CWALT falls within Quadrant 1. However, from an international relations point of view and the anarchy of the international system, a CWALT would exhibit more of a communitarian approach as a symbol of the notion of an international "community/society" and could therefore also be situated within Quadrant 4.
- Knake: At a first sight Knake's set of proposals appears to fall within the fourth quadrant. He is in fact proposing a Networked and distributed approach, to be implemented through the active involvement of a wide range of participants from the technical community, the private sector, as well as users and consumer groups, to shape policy and avoid state-centric processes. Not a single forum, at either national or international level, bur rather a range of forums.
- At a deeper reading of Knake's arguments, however, it appears more clear that - in his mind - the US should nurture and indirectly control his proposed "light intergovernmental body". When Knake urges the US to be involved in international negotiations concerning the fight of cyber crime, he does so to avoid a "perception" that would eventually turn out to be detrimental to the US. Even private actors, such as Microsoft and Symantec, would be captured in the governmental sphere, by being made aware of the goals of the US government and actively help in achieving such goals.
- Goldsmith: His approach appears to rely heavily on communitarian, self-governed mechanisms to face the new cyber threats, which would place it in the fourth quadrant. However, Goldsmith himself acknowledges that governmental intervention is to some extent necessary to support and guarantee the efficacy of community organizations.
Quadrant 2 or 4?
- Mirror As You Link: Professor Zittrain's proposal allows Internet users to download a website from different servers, which seems to be a polyarchical solution. Additionally, this system needs to be adopted and maintained by web server vendors, which are top-down institutions. This seems to indicate that Mirror As You Link is a first quadrant solution. It could be argued, however, that this system also falls in the fourth quadrant. Mirror As You Link could be adopted in such a way that rules are agreed upon by the Internet users themselves, and it's unclear whether there would be an ability for users to choose between multiple linking regimes.
Quadrant 3 or 4?
- Clarke&Knake: The idea of a broad public dialogue is clearly closer at the bottom-up end of the vertical axis but seems to move along the horizontal one. The question is to what degree the public at large can be engaged or if the technical required knowhow will limit the extent to the breadth of the dialogue.
A New Mapping
How did the use of the four quadrants tool impact our analysis? Below is our attempt to map all of the approaches onto a single chart: