Institutional structure: Difference between revisions
| (64 intermediate revisions by 4 users not shown) | |||
| Line 1: | Line 1: | ||
= Introduction = | = Introduction = | ||
As the importance of the Internet increases for citizens, corporations, and governments, so does the danger posed by attacks to and through these new systems. Awareness of the dangers posed by cyberthreats has increased gradually in tandem with their frequency and sophistication, and to a large extent, current government institutions have adapted existing capabilities to this new context. | As the importance of the Internet increases for citizens, corporations, and governments, so does the danger posed by attacks to and through these new systems. Awareness of the dangers posed by cyberthreats has increased gradually in tandem with their frequency and sophistication, and to a large extent, current government institutions have adapted existing capabilities to this new context. As concern over cyberwar and cybercrime continued to increase, a major military unit dedicated to cybersecurity was inaugurated by the Department of Defense in November 2010. [[#Cyber Command|Cyber Command]], as it is named, has the [http://www.defense.gov/home/features/2010/0410_cybersec/docs/CYBERCOM%20Fact%20Sheet%20to%20replace%20online%20version%20on%20OCT%2013.pdf stated mission] to "conduct full-spectrum military cyberspace operations" and "ensure US/Allied freedom of action in cyberspace and deny the same to our adversaries." | ||
This project explores the current shape of the institutional structures in the United States devoted to cyberthreat detection, mitigation, and response, and questions whether other structures might be more effective and/or better serve important non-security government goals. This project does not undertake to describe or classify the different types of cyberthreats based on perpetrator or motive. While the issue of threat taxonomy is an interesting one, at the level of institutional response it is often irrelevant. A cyberattack poses the same immediate issues of response whether it was launched by a country or a wayward teenager. There are of course some issues of threat classification, but these are closely linked to the distribution of authority among agencies-- an attack on military networks will raise different issues and provoke a different response than an attack on the servers of a private corporation. | This project explores the current shape of the institutional structures in the United States devoted to cyberthreat detection, mitigation, and response, and questions whether other structures might be more effective and/or better serve important non-security government goals. This project does not undertake to describe or classify the different types of cyberthreats based on perpetrator or motive. While the issue of threat taxonomy is an interesting one, at the level of institutional response it is often irrelevant. A cyberattack poses the same immediate issues of response whether it was launched by the military apparatus of a country or a wayward Belgian teenager. There are of course some issues of threat classification, but these are closely linked to the distribution of authority among agencies-- an attack on military networks will raise different issues and provoke a different response than an attack on the servers of a private corporation. | ||
Some questions to keep in mind when considering these materials: | Some questions to keep in mind when considering these materials: | ||
| Line 9: | Line 9: | ||
* How do different institutional arrangements affect other important rights and government interests, such as privacy? | * How do different institutional arrangements affect other important rights and government interests, such as privacy? | ||
* How much weight should these rights and interests receive as compared with security concerns? | * How much weight should these rights and interests receive as compared with security concerns? | ||
* What relative weight should be assigned to each of the institutional responsibilities in this area? | * What relative weight should be assigned to each of the institutional [[#Responsibilities|responsibilities]] in this area? | ||
* Is the response purely an executive responsibility? What kinds of government agencies and branches should be involved in developing responses to cyber threats? | |||
* How proactive should the government be in these areas: should the government take the lead in both defensive and offensive cyber capabilities? In terms of resource allocation, what is the appropriate response to the current level of threats? | |||
* How does the complex threat environment (national and individual-based attacks) affect the U.S.' optimal response to attacks? Should the U.S. see cyber attacks as a military, criminal, or international relations issue? | |||
= Status Quo = | = Status Quo = | ||
| Line 15: | Line 18: | ||
While an increasing number of statutes and executive decisions organize agencies, allocate responsibilities and create inter-agency relationships, the current structure principally reflects historical and bureaucratic decisions by the agencies themselves rather than an overarching institutional design decision. As a result, the government structures for responding to cyber-threats are complex, with a number of agencies sharing authority in occasionally overlapping areas. | While an increasing number of statutes and executive decisions organize agencies, allocate responsibilities and create inter-agency relationships, the current structure principally reflects historical and bureaucratic decisions by the agencies themselves rather than an overarching institutional design decision. As a result, the government structures for responding to cyber-threats are complex, with a number of agencies sharing authority in occasionally overlapping areas. | ||
[[Image:Agency_soup.png| | [[Image:Agency_soup.png|400px|thumb|left|Primary and secondary agencies]] | ||
This chart, while by no means an exhaustive survey of government action in the realm of cybercrime and cyberwar, attempts to plot several of the major actors in those areas as well as the key relationships linking those actors together. | This chart, while by no means an exhaustive survey of government action in the realm of cybercrime and cyberwar, attempts to plot several of the major actors in those areas as well as the key relationships linking those actors together. | ||
| Line 42: | Line 45: | ||
* recovery policies and activities, | * recovery policies and activities, | ||
"including computer network operations, information assurance, law enforcement, diplomacy, military, and intelligence missions as they relate to the security and stability of the global information and communications infrastructure." The 60-Day Review offers no explanation of what each term might entail (and in fact this might just be a throwaway list), but this provides at least a starting point for thinking about the array of responsibilities agencies may be saddled with in addressing potential and actual cyber-threats. | "including computer network operations, information assurance, law enforcement, diplomacy, military, and intelligence missions as they relate to the security and stability of the global information and communications infrastructure." The 60-Day Review offers no explanation of what each term might entail (and in fact this might just be a throwaway list), but this provides at least a starting point for thinking about the array of responsibilities agencies may be saddled with in addressing potential and actual cyber-threats. The 60-Day Review presents a near-term and mid-term action plan that may eventually alter the status quo as outlined herein. | ||
== Links == | == Links == | ||
| Line 48: | Line 51: | ||
The different actors in the cybersecurity context are connected through a variety of structural links and formal and informal agreements. These connections take four general forms: | The different actors in the cybersecurity context are connected through a variety of structural links and formal and informal agreements. These connections take four general forms: | ||
* Structural ( | * Structural (or official institutional subordination, for example, the Secret Service is a component of DHS) | ||
* Statutory | * Statutory | ||
* Negotiated cooperation | * Negotiated cooperation | ||
| Line 55: | Line 58: | ||
There are few formal agreements and statues explicitly governing relationships between agencies in the cybersecurity realm. Some examples of current agreements between agencies, depicted in the above chart as lines between actors, include: | There are few formal agreements and statues explicitly governing relationships between agencies in the cybersecurity realm. Some examples of current agreements between agencies, depicted in the above chart as lines between actors, include: | ||
* The Enduring Security Framework, which is intended to operate to encourage cooperation between the public and private sectors, is ill-defined and little publicized. | * [[#The Enduring Security Framework|The Enduring Security Framework]], which is intended to operate to encourage cooperation between the public and private sectors, is ill-defined and little publicized. | ||
* | * [http://itlaw.wikia.com/wiki/National_Cyber_Response_Coordination_Group National Cyber Response Coordination Group] (NCRCG) | ||
* | * [http://www.fbi.gov/about-us/investigate/cyber/ncijtf National Cyber Investigative Joint Task Force] (NCIJTF) | ||
** See also the [http://www.justice.gov/ola/testimony/111-1/2009-11-17-fbi-chabinsky-cybersecurity.pdf Senate Judiciary Committee testimony] of Steven Chabinsky, Deputy Assistant Director of the FBI's Cyber Division | |||
Other opportunities for cooperation have arisen through slightly less formal processes. For instance, the DHS and NSA in October 2010 [http://www.theatlantic.com/politics/archive/2010/10/nsa-dhs-deepen-cyber-relationships/64498/ announced a coordinated response] to cyber threats. Under this agreement, both agencies will assign staff and officials to permanent exchange posts in the other agency's offices, and the NSA will provide additional support to the DHS's cybersecurity efforts. | Other opportunities for cooperation have arisen through slightly less formal processes. For instance, the DHS and NSA in October 2010 [http://www.theatlantic.com/politics/archive/2010/10/nsa-dhs-deepen-cyber-relationships/64498/ announced a coordinated response] to cyber threats. Under this agreement, both agencies will assign staff and officials to permanent exchange posts in the other agency's offices, and the NSA will provide additional support to the DHS's cybersecurity efforts. | ||
| Line 69: | Line 73: | ||
As one example, [http://www.nytimes.com/2010/11/14/magazine/14Hacker-t.html this New York Times article] describes how one hacker, Albert Gonzalez, was able to evade capture by the police for a number of attacks on different commercial websites while he was simultaneously under protection as a Secret Service informant. | As one example, [http://www.nytimes.com/2010/11/14/magazine/14Hacker-t.html this New York Times article] describes how one hacker, Albert Gonzalez, was able to evade capture by the police for a number of attacks on different commercial websites while he was simultaneously under protection as a Secret Service informant. | ||
= | == Cyber Command == | ||
The | The establishment of Cyber Command was [http://www.stratcom.mil/factsheets/cc/ announced] in 2009, and after some delay, it went operational in November 2010. Since then, however, [http://www.defense.gov/home/features/2010/0410_cybersec/ CYBERCOM] has faced a lack of agreement over its mission and role. | ||
Cyber Command falls under the Pentagon, and it is led by General [http://www.washingtonpost.com/wp-dyn/content/article/2010/05/10/AR2010051005251.html Keith Alexander], who is dual-hatted as the National Security Agency director. Alexander has [http://articles.cnn.com/2010-09-23/politics/cyber.security.hearing_1_cyber-command-cyber-defense-nasa-computers?_s=PM:POLITICS stated] that he is responsible for protecting Defense Department networks, but the scope of Cyber Command responsibilities, as well as its conformity with traditional military-civilian [http://www.nytimes.com/2010/09/24/us/24cyber.html?scp=5&sq=cyber%20command%20military%20alexander&st=cse boundaries], remain up in the air, although Alexander did provided some insight into his goals in his responses to the [https://www.washingtonpost.com/wp-srv/politics/documents/questions.pdf advance questions] prepared by Congress before his confirmation hearing. Specifically, officials are working out whether Cyber Command will take a role in [http://www.wired.com/dangerroom/2010/09/militarys-cyber-commander-swears-no-role-on-civilian-networks/ protecting civilian networks]. Although Cyber Command has publicly disaffirmed its role in civilian networks and Alexander's answers to Congress's advance testimony evince no clear intention to intervene in this area, Alexander's other organization, the NSA, has already taken steps toward working with private companies. Indeed, in October 2010, the Department of Defense and Department of Homeland Security signed a [http://www.defense.gov/releases/release.aspx?releaseid=13965 memorandum of agreement] aimed at protecting "critical networks." Additionally, Cyber Command has recently been exploring offensive [http://www.washingtonpost.com/wp-dyn/content/article/2010/11/05/AR2010110507304.html attack capabilities], but disagreement over how this responsibility would fit into its still-undefined mission will likely slow any formal decision-making on the issue. | |||
== International Comparisons == | == International Comparisons == | ||
*China | |||
Though the exact structure of other countries' cyber capabilities is difficult to ascertain, the US may be playing catch-up relative to China and Russia. | |||
*China has placed cyber responsibilities under military leadership | |||
** Established the [http://www.unhcr.org/refworld/country,,THE_JF,COUNTRYNEWS,CHN,,4c74e64d2,0.html "Information Security Base"] in July 2010 | ** Established the [http://www.unhcr.org/refworld/country,,THE_JF,COUNTRYNEWS,CHN,,4c74e64d2,0.html "Information Security Base"] in July 2010 | ||
***This agency falls under military command | ***This agency falls under military command | ||
| Line 83: | Line 89: | ||
** China has been developing [http://online.wsj.com/article/SB10001424052748703399204574508413849779406.html attack capabilities] since 2003 | ** China has been developing [http://online.wsj.com/article/SB10001424052748703399204574508413849779406.html attack capabilities] since 2003 | ||
** But capabilities, of course, remain [http://www.pcworld.com/businesscenter/article/201183/talk_on_china_cyber_army_pulled_after_pressure.html guarded] | ** But capabilities, of course, remain [http://www.pcworld.com/businesscenter/article/201183/talk_on_china_cyber_army_pulled_after_pressure.html guarded] | ||
* Russia | * Russia has allegedly used its intelligence agencies for cyber attacks and has worked with criminal networks | ||
** Russia wants to develop an [http://www.technologyreview.com/blog/editors/25050/ international agreement] to deal with cyber-attacks | ** Russia wants to develop an [http://www.technologyreview.com/blog/editors/25050/ international agreement] to deal with cyber-attacks | ||
** In the 2008 Georgian war, cyber attacks on Georgian government websites were linked to [http://news.cnet.com/8301-13639_3-10312708-42.html civilians] pulled from social networking sites and using Russian Mafia botnets, as well as to Russian [http://www.cio.com/article/485828/Report_Links_Russian_Intelligence_to_Cyber_Attacks intelligence agencies] | ** In the 2008 Georgian war, cyber attacks on Georgian government websites were linked to [http://news.cnet.com/8301-13639_3-10312708-42.html civilians] pulled from social networking sites and using Russian [http://www.nytimes.com/2008/08/13/technology/13cyber.html Mafia] botnets, as well as to Russian [http://www.cio.com/article/485828/Report_Links_Russian_Intelligence_to_Cyber_Attacks intelligence agencies] | ||
** A 2008 attack on U.S. military networks has also been [http://www.msnbc.msn.com/id/40306517/ns/us_news-security/ linked] to Russian intelligence agencies | ** A 2008 attack on U.S. military networks has also been [http://www.msnbc.msn.com/id/40306517/ns/us_news-security/ linked] to Russian intelligence agencies | ||
= Agency Organizational Strategies = | |||
The apparent weaknesses in the current agency structure suggest two major organizing strategies. | |||
First, agency cyber-security responsibilities have largely evolved in a bottom-up manner as agencies often unilaterally expanded their spheres of operation onto the Internet. In some cases this approach resulted in seemingly natural allocations, such as the Department of Justice and FBI taking responsibility for investigating computer crimes. But in other cases the result was overlap between disparate agencies responsible for performing substantially similar operations. For example, the Department of Defense has its own investigative office — the Defense Cyber Crimes Center; the Secret Service adds a another layer of investigative authority with its Electronic Crimes Task Forces (which coordinate between federal, state, and local law enforcement activities). | |||
Second, management of cyber-threats is still largely decentralized, though the Department of Homeland Security has slightly increased the degree of centralization (and it's still unclear how Cyber Command is going to fit into the agency framework). There is no cybersecurity version of the [http://www.dni.gov/index.html Director of National Intelligence] to centralize agency information and activities relating to cyber-threats, nor is there a mechanism for determining who is initially responsible for responding to a newly-discovered incident or threat. Given the difficulty in identifying the actor behind a particular attack, interested agencies will be generally unable to classify the nature of an incident — criminal, espionage, terrorist, or something else — prior to commencing the investigation and response. In the absence of centralization, this means that agencies must decide among themselves who should mount the response — or that they will risk the inefficiency and inconsistency of multiple agencies independently acting. | |||
== Top-down vs. Bottom-up Allocation of Responsibilities == | == Top-down vs. Bottom-up Allocation of Responsibilities == | ||
Thus far, the institutional structure has evolved in response to cyberthreats as they are detected. There may be advantages to replacing this organic, bottom-up system with one imposed from above, or with applying some hybrid approach that lies between the two extremes. The aforementioned [http://www.gao.gov/new.items/d10338.pdf GAO report] calls for imposing a stronger top-down structure than currently exists. | |||
=== Top-Down=== | |||
Under a top-down arrangement, agencies would be allocated a set of responsibilities from some central authority—perhaps Congress by statute, or perhaps from a central agency. | |||
* | * Pros | ||
** Clarity of organization: little overlap of responsibility when externally allocated | ** Clarity of organization: little overlap of responsibility when externally allocated | ||
*** Responsibilities may also be more accurately allocated in relation to actors' strengths | |||
** Accountability: when actors have externally defined roles, they are more likely to be held to account for their performance in pursuing these goals. | ** Accountability: when actors have externally defined roles, they are more likely to be held to account for their performance in pursuing these goals. | ||
* Bottom-Up | * Cons | ||
** Flexibility: allows actors to adapt and respond to changing threat | ** Bureaucracy: hierarchical requirements slow institutional response. | ||
** Institutional costs: allocation of responsibilities requires prior understanding and responding to the diversity of cyber threats that exist, which may be costly to develop. | |||
** Lacunae: Efforts to reduce overlap (or simple oversight/lack of experience) may result in some threats remaining unaddressed. | |||
*** For example, if an entirely new type of cyber-threat arises, no agency may have the authority to respond immediately. | |||
=== Bottom-Up === | |||
Under a bottom-up approach, agencies independently decide which aspects of cybersecurity fall within their areas of expertise and take responsibility accordingly. | |||
*Pros | |||
** Flexibility: allows actors to adapt and respond to changing threat environments | |||
** Actors who are accustomed to dealing directly with a specific threat may be better at formulating effective responses | |||
** Innovation: a more diverse set of actors may devise more creative approaches, which a top-down approach could stifle | |||
*Cons | |||
** Conflict: Agency overlap may lead to inefficient overlapping responses and inter-agency turf wars. | |||
** Forced decentralization: May be incompatible with a highly centralized agency response structure. | |||
== Centralization vs. Decentralization == | == Centralization vs. Decentralization == | ||
The current system is extremely fragmented and decentralized: until the creation of Cyber Command, allocation of responsibilities happened by default or necessity. With the advent of Cyber Command, however, there is great potential to rectify the problems of fragmentation--but correspondingly, there are potential risks to concentrating power in one agency. There | The current system is extremely fragmented and decentralized: until the creation of Cyber Command, allocation of responsibilities happened by default or necessity. With the advent of Cyber Command, however, there is great potential to rectify the problems of fragmentation--but correspondingly, there are potential risks to concentrating power in one agency. There is a spectrum of organizational options available ranging from centralization to decentralization. | ||
=== Decentralization === | === Decentralization === | ||
| Line 107: | Line 141: | ||
*Pros: | *Pros: | ||
** The current structure is already highly decentralized, so such an approach involves little disruption of the status quo. | ** Implementation: The current structure is already highly decentralized, so such an approach involves little disruption of the status quo. | ||
** Presumably there would be less risk of agency over-reach into civilian networks, since practically speaking, no agency will have the tools (or agencies may serve as checks on each other). | ** Limitation: Presumably there would be less risk of agency over-reach into civilian networks, since practically speaking, no agency will have the tools (or agencies may serve as checks on each other). | ||
** A more heterarchical structure may breed creativity and innovation in responding to attacks. | ** Innovation: A more heterarchical structure may breed creativity and innovation in responding to attacks. | ||
*Cons: | *Cons: | ||
** Responses might not always come from the | ** Allocation: Responses might not always come from the agency with the greatest relevant expertise or most abundant resources. | ||
*** For example, the first agency to learn of an attack is not necessarily the ideal one to respond, but it may not want to give up responsibility to another agency (reflecting inter-agency competition) | *** For example, the first agency to learn of an attack is not necessarily the ideal one to respond, but it may not want to give up responsibility to another agency (reflecting inter-agency competition) | ||
** Agencies may not share sufficient information to optimize security (for an example of these flaws and a reaction to them, see [http://www.brookings.edu/testimony/2003/1208terrorism_thompson.aspx pre- and post-9/11] counter-terrorism responsibilities) | ** Information blindness: Agencies may not share sufficient information to optimize security (for an example of these flaws and a reaction to them, see [http://www.brookings.edu/testimony/2003/1208terrorism_thompson.aspx pre- and post-9/11] counter-terrorism responsibilities) | ||
** Connecting-the-dots problems: if attacks are handled by different agencies that do not share information, it's possible that no agency will be able to piece together enough clues to find out who the perpetrator is | *** Connecting-the-dots problems: if attacks are handled by different agencies that do not share information, it's possible that no agency will be able to piece together enough clues to find out who the perpetrator is | ||
** | ** Competition: Agencies may compete to keep the best technical resources and may be unwilling to risk sharing credit for successes. | ||
*** | *** For example, other agency heads have [http://news.cnet.com/8301-13578_3-10191170-38.html criticized] NSA dominance of cyber issues | ||
=== Hybrid Structures === | === Hybrid Structures === | ||
One approach would be the leadership strategy, wherein one agency (such as the newly-formed Cyber Command, or the Department of Homeland Security) acts in an organizational role while other agencies maintain their core independent responsibilities. The leadership agency could institute some sort of reporting system to collect information on attacks from other agencies. The bar for centralized reporting could be adjusted according to efficiency and informational requirements: agencies could independently categorize problems as high- or low-risk, and report to the leadership agency accordingly ( | One approach would be the leadership strategy, wherein one agency (such as the newly-formed Cyber Command, or the Department of Homeland Security) acts in an organizational role while other agencies maintain their core independent responsibilities. The leadership agency could institute some sort of reporting system to collect information on attacks from other agencies. The bar for centralized reporting could be adjusted according to efficiency and informational requirements: agencies could independently categorize problems as high- or low-risk, and report to the leadership agency accordingly (perhaps handling the low-risk issues on their own); alternatively, agencies could report all issues to the leadership agency, who would then be responsible for categorization. In either case, the leadership agency would presumably assume responsibility for delegating response to the agency it deems best-poised to address the issue. The leadership agency could also serve as a central contact for obtaining technical resources when, say, the DOJ needs outside expertise to investigate a particular attack. | ||
* Pros: | |||
** Information awareness: Information becomes centralized, allowing for easier analysis of cyber-threats and allowing for inter-agency information sharing. | |||
** Allocation: Response to individual attacks can be determined based on an outside evaluation of available expertise and resources—possibly less politicization and competition within and among agencies. | |||
* Cons: | |||
** Delay: Reduced reaction time as the leadership agency determines an appropriate response. | |||
** Information leakage: Centralized information poses a Wikileaks problem—if the leadership agency is compromised, the entire body of attack and response data could be released. | |||
** Implementation: Potentially difficult to achieve given the status quo—agencies may be reluctant to release information and responsibility to the leadership agency. | |||
=== Centralization === | |||
Under a centralized structure, one agency would hold all or most of the responsibility for addressing cybersecurity threats. Other agencies may haver some support responsibilities, and would presumably still be responsible for ensuring the security of their own systems and adherence to best practices. In an extremely centralized structure, the central "Cyber Agency" may possess "all" responsibilities: investigation, defense, attack, and regulation. | |||
* Pros | |||
** Coordination: Reduce inefficiency by concentrating technical expertise and responsibility in one agency. | |||
** Information centralization: No information-sharing issues. | |||
** Lack of delay: Rapid response to attacks—defensive and investigative expertise can be brought to bear simultaneously, and counter-attacks can be more easily organized. | |||
* | * Cons | ||
** Orwell problem: The central agency may hold too much power—the scope of cyber-responsibilities could be construed quite broadly. | |||
*** NSA has already caused some concern over its far-reaching [http://www.pcworld.com/businesscenter/article/200824/nsas_perfect_citizen_program_what_you_need_to_know.html programs]. | |||
*** Over-broad set of responsibilities may result in an unwieldy | |||
** | ** Over-centralization: Some cyber crimes may be small-scale and easily handled by other agencies (such as DOJ), or may be more relevant to another agency's area of expertise. | ||
** Boundary violation: Centralization may also cross the negotiated boundaries that define agency reach (e.g., [http://www.nytimes.com/2010/10/21/us/21cyber.html?hp military] action in domestic settings) | |||
** Information leakage: Wikileaks problem is even more salient when the entire structure is monolithic. | |||
** Ossification: Groupthink may limit innovative approaches to cybersecurity. | |||
*** NSA has already caused some concern over its far-reaching [http://www.pcworld.com/businesscenter/article/200824/nsas_perfect_citizen_program_what_you_need_to_know.html programs] | |||
** | |||
** | |||
** | |||
= Involving the Private Sector = | = Involving the Private Sector = | ||
| Line 163: | Line 198: | ||
According to [http://docs.google.com/viewer?a=v&q=cache:CfW4LfiwAgAJ:armedservices.house.gov/pdfs/StratForces031610/Miller_Testimony031610.pdf+enduring+security+framework&hl=en&gl=us&pid=bl&srcid=ADGEESispN9NMysIQOAGJ15TEcztjlzXK4osiPjOWVogxR5XRqzT9Uzj-Gp8azlXhJHSfA1ddyrUnFIt08pScKkRGTtvETpzo_BXczZmUw3oKnlKlsq8eZiESA15QJ75pwtTa2s2q0Wu&sig=AHIEtbTRTX9PO5rf10l9SH38WvIbub6tcA testimony by James N. Miller], Principal Deputy Under Secretary of Defense for Policy, "[t]he Enduring Security Framework is a public-private partnership between the Director for National Intelligence, DoD, the Department of Homeland Security, and the private sector; its goal is to provide a permanent forum for USG-industry dialogue." | According to [http://docs.google.com/viewer?a=v&q=cache:CfW4LfiwAgAJ:armedservices.house.gov/pdfs/StratForces031610/Miller_Testimony031610.pdf+enduring+security+framework&hl=en&gl=us&pid=bl&srcid=ADGEESispN9NMysIQOAGJ15TEcztjlzXK4osiPjOWVogxR5XRqzT9Uzj-Gp8azlXhJHSfA1ddyrUnFIt08pScKkRGTtvETpzo_BXczZmUw3oKnlKlsq8eZiESA15QJ75pwtTa2s2q0Wu&sig=AHIEtbTRTX9PO5rf10l9SH38WvIbub6tcA testimony by James N. Miller], Principal Deputy Under Secretary of Defense for Policy, "[t]he Enduring Security Framework is a public-private partnership between the Director for National Intelligence, DoD, the Department of Homeland Security, and the private sector; its goal is to provide a permanent forum for USG-industry dialogue." | ||
Further information on the Enduring Security Framework is currently scarce, however, so it's unclear precisely what exactly this process entails. But what | Further information on the Enduring Security Framework is currently scarce, however, so it's unclear precisely what exactly this process entails. But what ''should'' be involved in the government-industry dialogue? | ||
== The Defense Industrial Base == | == The Defense Industrial Base == | ||
Certain private companies classified under [http://www.fas.org/irp/offdocs/nspd/hspd-7.html Homeland Security Presidential Directive 7] (HSPD-7) as "critical infrastructure and key resources" (CIKR) work together with the Sector-Specific Agencies (SSAs) to establish information-sharing and analysis programs. The [http://www.dhs.gov/xlibrary/assets/nipp-ssp-defense-industrial-base.pdf Defense Industrial Base] is the set of CIKRs for which DoD is the relevant SSA. The DIB is primarily focused on ensuring that industries necessary to supplying and maintaining the military are protected and resilient against harms ranging from natural disaster to intentional attacks. The DoD's Sector-Specific Plan has this to say about cyber-threats: | Certain private companies classified under [http://www.fas.org/irp/offdocs/nspd/hspd-7.html Homeland Security Presidential Directive 7] (HSPD-7) as "critical infrastructure and key resources" (CIKR) work together with the Sector-Specific Agencies (SSAs) to establish information-sharing and analysis programs. The [http://www.dhs.gov/xlibrary/assets/nipp-ssp-defense-industrial-base.pdf Defense Industrial Base] (DIB) is the set of CIKRs for which DoD is the relevant SSA. The DIB is primarily focused on ensuring that industries necessary to supplying and maintaining the military are protected and resilient against harms ranging from natural disaster to intentional attacks. The DoD's Sector-Specific Plan has this to say about cyber-threats: | ||
<blockquote> | <blockquote> | ||
Latest revision as of 22:57, 20 December 2010
Introduction
As the importance of the Internet increases for citizens, corporations, and governments, so does the danger posed by attacks to and through these new systems. Awareness of the dangers posed by cyberthreats has increased gradually in tandem with their frequency and sophistication, and to a large extent, current government institutions have adapted existing capabilities to this new context. As concern over cyberwar and cybercrime continued to increase, a major military unit dedicated to cybersecurity was inaugurated by the Department of Defense in November 2010. Cyber Command, as it is named, has the stated mission to "conduct full-spectrum military cyberspace operations" and "ensure US/Allied freedom of action in cyberspace and deny the same to our adversaries."
This project explores the current shape of the institutional structures in the United States devoted to cyberthreat detection, mitigation, and response, and questions whether other structures might be more effective and/or better serve important non-security government goals. This project does not undertake to describe or classify the different types of cyberthreats based on perpetrator or motive. While the issue of threat taxonomy is an interesting one, at the level of institutional response it is often irrelevant. A cyberattack poses the same immediate issues of response whether it was launched by the military apparatus of a country or a wayward Belgian teenager. There are of course some issues of threat classification, but these are closely linked to the distribution of authority among agencies-- an attack on military networks will raise different issues and provoke a different response than an attack on the servers of a private corporation.
Some questions to keep in mind when considering these materials:
- How do different institutional arrangements affect other important rights and government interests, such as privacy?
- How much weight should these rights and interests receive as compared with security concerns?
- What relative weight should be assigned to each of the institutional responsibilities in this area?
- Is the response purely an executive responsibility? What kinds of government agencies and branches should be involved in developing responses to cyber threats?
- How proactive should the government be in these areas: should the government take the lead in both defensive and offensive cyber capabilities? In terms of resource allocation, what is the appropriate response to the current level of threats?
- How does the complex threat environment (national and individual-based attacks) affect the U.S.' optimal response to attacks? Should the U.S. see cyber attacks as a military, criminal, or international relations issue?
Status Quo
While an increasing number of statutes and executive decisions organize agencies, allocate responsibilities and create inter-agency relationships, the current structure principally reflects historical and bureaucratic decisions by the agencies themselves rather than an overarching institutional design decision. As a result, the government structures for responding to cyber-threats are complex, with a number of agencies sharing authority in occasionally overlapping areas.
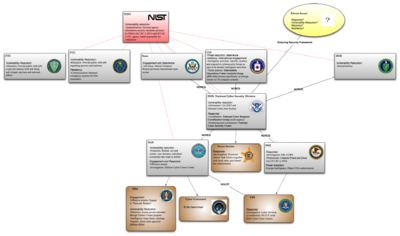
This chart, while by no means an exhaustive survey of government action in the realm of cybercrime and cyberwar, attempts to plot several of the major actors in those areas as well as the key relationships linking those actors together.
One consequence of this lack of centralization is the lack of agreed-upon categories and terms for discussing types and threats and forms of response.
Actors
Various government and private actors participate in preventing, detecting, and responding to various cyber-threats. Broadly speaking, these actors fall into four different categories:
- Cyber-specific federal agencies (e.g. Cyber Command)
- Defense and investigation agencies (e.g. Department of Defense, FBI, CIA, NSA, DOJ)
- Independent agencies with relevant concerns and vulnerabilities (e.g. Department of State, Federal Communications Commission)
- Private corporations
Under federal law, every agency has at least some cybersecurity responsibility: the Federal Information Security Management Act, U.S.C § 3541 et seq., requires the head of each federal agency to ensure compliance with information security standards promulgated by the National Institute of Standards and Technology (NIST).
Responsibilities
One of the many uncertainties inherent in this discussion is how to go about classifying the types of responsibilities we want to allocate among the various federal agencies. The White House Cyberspace Policy Review (the 60-Day Review) notes that it considers "Cybersecurity policy" to include the following activities:
- threat reduction
- vulnerability reduction
- deterrence, international engagement
- incident response
- resiliency
- recovery policies and activities,
"including computer network operations, information assurance, law enforcement, diplomacy, military, and intelligence missions as they relate to the security and stability of the global information and communications infrastructure." The 60-Day Review offers no explanation of what each term might entail (and in fact this might just be a throwaway list), but this provides at least a starting point for thinking about the array of responsibilities agencies may be saddled with in addressing potential and actual cyber-threats. The 60-Day Review presents a near-term and mid-term action plan that may eventually alter the status quo as outlined herein.
Links
The different actors in the cybersecurity context are connected through a variety of structural links and formal and informal agreements. These connections take four general forms:
- Structural (or official institutional subordination, for example, the Secret Service is a component of DHS)
- Statutory
- Negotiated cooperation
- De facto cooperation (history of communication and coordination between Department of Defense and State Department)
There are few formal agreements and statues explicitly governing relationships between agencies in the cybersecurity realm. Some examples of current agreements between agencies, depicted in the above chart as lines between actors, include:
- The Enduring Security Framework, which is intended to operate to encourage cooperation between the public and private sectors, is ill-defined and little publicized.
- National Cyber Response Coordination Group (NCRCG)
- National Cyber Investigative Joint Task Force (NCIJTF)
- See also the Senate Judiciary Committee testimony of Steven Chabinsky, Deputy Assistant Director of the FBI's Cyber Division
Other opportunities for cooperation have arisen through slightly less formal processes. For instance, the DHS and NSA in October 2010 announced a coordinated response to cyber threats. Under this agreement, both agencies will assign staff and officials to permanent exchange posts in the other agency's offices, and the NSA will provide additional support to the DHS's cybersecurity efforts.
Current Problems
A Government Accountability Office report discussing the Comprehensive National Cybersecurity Initiative sums up one of the major problems with the current organizational situation thus: "Federal agencies have overlapping and uncoordinated responsibilities for cybersecurity, and it is unclear where overall responsibility for coordination lies."
The scarcity of official coordination between different government agencies raises a number of issues. Agencies may claim overlapping jurisdiction, leading to inefficient staffing and funding decisions (as well as inter-agency tension). At the same time, gaps in coverage between the jurisdictions of various agencies may emerge elsewhere. The inability of agencies effectively to share intelligence about possible threats in new technological contexts contributes to slower and less successful government responses.
As one example, this New York Times article describes how one hacker, Albert Gonzalez, was able to evade capture by the police for a number of attacks on different commercial websites while he was simultaneously under protection as a Secret Service informant.
Cyber Command
The establishment of Cyber Command was announced in 2009, and after some delay, it went operational in November 2010. Since then, however, CYBERCOM has faced a lack of agreement over its mission and role.
Cyber Command falls under the Pentagon, and it is led by General Keith Alexander, who is dual-hatted as the National Security Agency director. Alexander has stated that he is responsible for protecting Defense Department networks, but the scope of Cyber Command responsibilities, as well as its conformity with traditional military-civilian boundaries, remain up in the air, although Alexander did provided some insight into his goals in his responses to the advance questions prepared by Congress before his confirmation hearing. Specifically, officials are working out whether Cyber Command will take a role in protecting civilian networks. Although Cyber Command has publicly disaffirmed its role in civilian networks and Alexander's answers to Congress's advance testimony evince no clear intention to intervene in this area, Alexander's other organization, the NSA, has already taken steps toward working with private companies. Indeed, in October 2010, the Department of Defense and Department of Homeland Security signed a memorandum of agreement aimed at protecting "critical networks." Additionally, Cyber Command has recently been exploring offensive attack capabilities, but disagreement over how this responsibility would fit into its still-undefined mission will likely slow any formal decision-making on the issue.
International Comparisons
Though the exact structure of other countries' cyber capabilities is difficult to ascertain, the US may be playing catch-up relative to China and Russia.
- China has placed cyber responsibilities under military leadership
- Established the "Information Security Base" in July 2010
- This agency falls under military command
- Previously, cyber responsibilities had been dispersed throughout various military branches
- China has been developing attack capabilities since 2003
- But capabilities, of course, remain guarded
- Established the "Information Security Base" in July 2010
- Russia has allegedly used its intelligence agencies for cyber attacks and has worked with criminal networks
- Russia wants to develop an international agreement to deal with cyber-attacks
- In the 2008 Georgian war, cyber attacks on Georgian government websites were linked to civilians pulled from social networking sites and using Russian Mafia botnets, as well as to Russian intelligence agencies
- A 2008 attack on U.S. military networks has also been linked to Russian intelligence agencies
Agency Organizational Strategies
The apparent weaknesses in the current agency structure suggest two major organizing strategies.
First, agency cyber-security responsibilities have largely evolved in a bottom-up manner as agencies often unilaterally expanded their spheres of operation onto the Internet. In some cases this approach resulted in seemingly natural allocations, such as the Department of Justice and FBI taking responsibility for investigating computer crimes. But in other cases the result was overlap between disparate agencies responsible for performing substantially similar operations. For example, the Department of Defense has its own investigative office — the Defense Cyber Crimes Center; the Secret Service adds a another layer of investigative authority with its Electronic Crimes Task Forces (which coordinate between federal, state, and local law enforcement activities).
Second, management of cyber-threats is still largely decentralized, though the Department of Homeland Security has slightly increased the degree of centralization (and it's still unclear how Cyber Command is going to fit into the agency framework). There is no cybersecurity version of the Director of National Intelligence to centralize agency information and activities relating to cyber-threats, nor is there a mechanism for determining who is initially responsible for responding to a newly-discovered incident or threat. Given the difficulty in identifying the actor behind a particular attack, interested agencies will be generally unable to classify the nature of an incident — criminal, espionage, terrorist, or something else — prior to commencing the investigation and response. In the absence of centralization, this means that agencies must decide among themselves who should mount the response — or that they will risk the inefficiency and inconsistency of multiple agencies independently acting.
Top-down vs. Bottom-up Allocation of Responsibilities
Thus far, the institutional structure has evolved in response to cyberthreats as they are detected. There may be advantages to replacing this organic, bottom-up system with one imposed from above, or with applying some hybrid approach that lies between the two extremes. The aforementioned GAO report calls for imposing a stronger top-down structure than currently exists.
Top-Down
Under a top-down arrangement, agencies would be allocated a set of responsibilities from some central authority—perhaps Congress by statute, or perhaps from a central agency.
- Pros
- Clarity of organization: little overlap of responsibility when externally allocated
- Responsibilities may also be more accurately allocated in relation to actors' strengths
- Accountability: when actors have externally defined roles, they are more likely to be held to account for their performance in pursuing these goals.
- Clarity of organization: little overlap of responsibility when externally allocated
- Cons
- Bureaucracy: hierarchical requirements slow institutional response.
- Institutional costs: allocation of responsibilities requires prior understanding and responding to the diversity of cyber threats that exist, which may be costly to develop.
- Lacunae: Efforts to reduce overlap (or simple oversight/lack of experience) may result in some threats remaining unaddressed.
- For example, if an entirely new type of cyber-threat arises, no agency may have the authority to respond immediately.
Bottom-Up
Under a bottom-up approach, agencies independently decide which aspects of cybersecurity fall within their areas of expertise and take responsibility accordingly.
- Pros
- Flexibility: allows actors to adapt and respond to changing threat environments
- Actors who are accustomed to dealing directly with a specific threat may be better at formulating effective responses
- Innovation: a more diverse set of actors may devise more creative approaches, which a top-down approach could stifle
- Cons
- Conflict: Agency overlap may lead to inefficient overlapping responses and inter-agency turf wars.
- Forced decentralization: May be incompatible with a highly centralized agency response structure.
Centralization vs. Decentralization
The current system is extremely fragmented and decentralized: until the creation of Cyber Command, allocation of responsibilities happened by default or necessity. With the advent of Cyber Command, however, there is great potential to rectify the problems of fragmentation--but correspondingly, there are potential risks to concentrating power in one agency. There is a spectrum of organizational options available ranging from centralization to decentralization.
Decentralization
Under a decentralized agency structure, agencies would be independently responsible for identifying and responding to an attack. The agencies themselves would be responsible for coordinating their activities, and ensuring that the agency with the most relevant expertise addresses the problem at hand.
- Pros:
- Implementation: The current structure is already highly decentralized, so such an approach involves little disruption of the status quo.
- Limitation: Presumably there would be less risk of agency over-reach into civilian networks, since practically speaking, no agency will have the tools (or agencies may serve as checks on each other).
- Innovation: A more heterarchical structure may breed creativity and innovation in responding to attacks.
- Cons:
- Allocation: Responses might not always come from the agency with the greatest relevant expertise or most abundant resources.
- For example, the first agency to learn of an attack is not necessarily the ideal one to respond, but it may not want to give up responsibility to another agency (reflecting inter-agency competition)
- Information blindness: Agencies may not share sufficient information to optimize security (for an example of these flaws and a reaction to them, see pre- and post-9/11 counter-terrorism responsibilities)
- Connecting-the-dots problems: if attacks are handled by different agencies that do not share information, it's possible that no agency will be able to piece together enough clues to find out who the perpetrator is
- Competition: Agencies may compete to keep the best technical resources and may be unwilling to risk sharing credit for successes.
- For example, other agency heads have criticized NSA dominance of cyber issues
- Allocation: Responses might not always come from the agency with the greatest relevant expertise or most abundant resources.
Hybrid Structures
One approach would be the leadership strategy, wherein one agency (such as the newly-formed Cyber Command, or the Department of Homeland Security) acts in an organizational role while other agencies maintain their core independent responsibilities. The leadership agency could institute some sort of reporting system to collect information on attacks from other agencies. The bar for centralized reporting could be adjusted according to efficiency and informational requirements: agencies could independently categorize problems as high- or low-risk, and report to the leadership agency accordingly (perhaps handling the low-risk issues on their own); alternatively, agencies could report all issues to the leadership agency, who would then be responsible for categorization. In either case, the leadership agency would presumably assume responsibility for delegating response to the agency it deems best-poised to address the issue. The leadership agency could also serve as a central contact for obtaining technical resources when, say, the DOJ needs outside expertise to investigate a particular attack.
- Pros:
- Information awareness: Information becomes centralized, allowing for easier analysis of cyber-threats and allowing for inter-agency information sharing.
- Allocation: Response to individual attacks can be determined based on an outside evaluation of available expertise and resources—possibly less politicization and competition within and among agencies.
- Cons:
- Delay: Reduced reaction time as the leadership agency determines an appropriate response.
- Information leakage: Centralized information poses a Wikileaks problem—if the leadership agency is compromised, the entire body of attack and response data could be released.
- Implementation: Potentially difficult to achieve given the status quo—agencies may be reluctant to release information and responsibility to the leadership agency.
Centralization
Under a centralized structure, one agency would hold all or most of the responsibility for addressing cybersecurity threats. Other agencies may haver some support responsibilities, and would presumably still be responsible for ensuring the security of their own systems and adherence to best practices. In an extremely centralized structure, the central "Cyber Agency" may possess "all" responsibilities: investigation, defense, attack, and regulation.
- Pros
- Coordination: Reduce inefficiency by concentrating technical expertise and responsibility in one agency.
- Information centralization: No information-sharing issues.
- Lack of delay: Rapid response to attacks—defensive and investigative expertise can be brought to bear simultaneously, and counter-attacks can be more easily organized.
- Cons
- Orwell problem: The central agency may hold too much power—the scope of cyber-responsibilities could be construed quite broadly.
- NSA has already caused some concern over its far-reaching programs.
- Over-broad set of responsibilities may result in an unwieldy
- Over-centralization: Some cyber crimes may be small-scale and easily handled by other agencies (such as DOJ), or may be more relevant to another agency's area of expertise.
- Boundary violation: Centralization may also cross the negotiated boundaries that define agency reach (e.g., military action in domestic settings)
- Information leakage: Wikileaks problem is even more salient when the entire structure is monolithic.
- Ossification: Groupthink may limit innovative approaches to cybersecurity.
- Orwell problem: The central agency may hold too much power—the scope of cyber-responsibilities could be construed quite broadly.
Involving the Private Sector
Since the vast majority of critical Internet infrastructure is in private hands, the private sector clearly has a role to play in addressing cyber-threats, especially when it comes to ensuring the resiliency of our networks. Indeed, the record shows that attacks are levied against private companies and government alike. But effective cooperation between government and the private sector is burdened by a variety of hurdles:
- Communication: Under the current framework, it's unclear how agencies and private companies should interact. For example, if a federal agency detects an intrusion into a private system, should that agency immediately notify the company? If so, how? On the flip side, if a private company detects an intrusion into its own systems, how do we ensure that an appropriate agency receives that information?
- Information sharing: This is closely tied to the communication issue. Government may be reluctant to share information with the private sector in general for fear of disseminating sensitive information (for example, sharing information about a detected intrusion may reveal the nature of the detection systems that are in place). The prevalence of multinational corporations further complicates this issue; U.S. agencies may be especially wary of sharing information with a company based in China, even when that information may otherwise address a security problem. And from companies' perspective, providing information to government agencies may be seen as a risky activity—they are likely to worry about sharing trade secrets, business strategies, and other sensitive data that may eventually leak out (some of which may be subject to FOIA requests absent clear exemptions). Companies may be similarly reluctant to provide information regarding recent or ongoing cyber-attacks.
- Coordination: How can government agencies work together with the private sector to proactively improve security and network resiliency?
The Enduring Security Framework
According to testimony by James N. Miller, Principal Deputy Under Secretary of Defense for Policy, "[t]he Enduring Security Framework is a public-private partnership between the Director for National Intelligence, DoD, the Department of Homeland Security, and the private sector; its goal is to provide a permanent forum for USG-industry dialogue."
Further information on the Enduring Security Framework is currently scarce, however, so it's unclear precisely what exactly this process entails. But what should be involved in the government-industry dialogue?
The Defense Industrial Base
Certain private companies classified under Homeland Security Presidential Directive 7 (HSPD-7) as "critical infrastructure and key resources" (CIKR) work together with the Sector-Specific Agencies (SSAs) to establish information-sharing and analysis programs. The Defense Industrial Base (DIB) is the set of CIKRs for which DoD is the relevant SSA. The DIB is primarily focused on ensuring that industries necessary to supplying and maintaining the military are protected and resilient against harms ranging from natural disaster to intentional attacks. The DoD's Sector-Specific Plan has this to say about cyber-threats:
"While [the Assistant Secretary of Defense for Networks and Information Integration] is responsible within DoD for assuring the availability of the [Global Information Grid], those responsibilities do not extend to the private sector portion of the DIB. There is no specific cyber asset characterized as part of the DIB Sector. Individual DIB assets likely have cyber elements within them, but they are the responsibility of the asset owner/operator. Cyber security is part of the critical asset risk assessment process, and the expertise of ASD(NII) will be sought for development and distribution of best practices to be shared with all DIB security partners."