Cybersecurity: Difference between revisions
BerkmanSysop (talk | contribs) m UTurn to 1267401600 Tag: Manual revert |
|||
| (48 intermediate revisions by 21 users not shown) | |||
| Line 1: | Line 1: | ||
''For the cybersecurity student group's discussions from the Cyberlaw: Difficult Problems Class, see [[Cybersecurity Brainstorming]]'' | |||
== SCOPE OF THE PROBLEM == | == SCOPE OF THE PROBLEM == | ||
| Line 7: | Line 8: | ||
<blockquote>Cybersecurity policy as used in this document includes strategy, policy, and standards regarding the security of and operations in cyberspace, and encompasses the full range of threat reduction, vulnerability reduction, deterrence, international engagement, incident response, resiliency, and recovery policies and activities, including computer network operations, information assurance, law enforcement, diplomacy, military, and intelligence missions as they relate to the security and stability of the global information and communications infrastructure. The scope does not include other information and communications policy unrelated to national security or securing the infrastructure.<ref name="WhiteHouseReview">[http://www.whitehouse.gov/assets/documents/Cyberspace_Policy_Review_final.pdf] White House Cyberspace Policy Review, p2 (March, 2009).</ref></blockquote> | <blockquote>Cybersecurity policy as used in this document includes strategy, policy, and standards regarding the security of and operations in cyberspace, and encompasses the full range of threat reduction, vulnerability reduction, deterrence, international engagement, incident response, resiliency, and recovery policies and activities, including computer network operations, information assurance, law enforcement, diplomacy, military, and intelligence missions as they relate to the security and stability of the global information and communications infrastructure. The scope does not include other information and communications policy unrelated to national security or securing the infrastructure.<ref name="WhiteHouseReview">[http://www.whitehouse.gov/assets/documents/Cyberspace_Policy_Review_final.pdf] White House Cyberspace Policy Review, p2 (March, 2009).</ref></blockquote> | ||
Summarizing, the Policy Review notes that âCyberspace touches practically everything and everyone.â<ref name="WhiteHouseReview" /> Given this definition, it is no wonder that cybersecurity is perceived as an almost insurmountable problem. In order to begin approaching solutions, therefore, we will first begin by breaking down our understanding of what cybersecurity means. | Summarizing, the Policy Review notes that âCyberspace touches practically everything and everyone.â<ref name="WhiteHouseReview" /> Given this definition, it is no wonder that cybersecurity is perceived as an almost insurmountable problem. In order to begin approaching solutions, therefore, we will first begin by breaking down our understanding of what cybersecurity means. | ||
For pictures of the whiteboards from Professors Goldsmith and Zittran's conversation can be found [[here.]] | |||
== ASSESSING VULNERABILITY == | == ASSESSING VULNERABILITY == | ||
| Line 22: | Line 24: | ||
This vulnerability considers attacks upon the network itself. A clever hacker could shut down the internet itself in an extreme case, or more conservatively can re-route the internet to prevent users from getting where they need to go. | This vulnerability considers attacks upon the network itself. A clever hacker could shut down the internet itself in an extreme case, or more conservatively can re-route the internet to prevent users from getting where they need to go. | ||
The internet is a large-scale decentralized network. A packet sent from one computer to another may cross multiple networking administrative domains (called Autonomous Systems [AS]). Internet routing includes two different systems: an intra-domain routing system and an inter-domain routing system. AS routes traffic within its infrastructure any way it likes, but all of the AS's coordinate inter-domain routing by running a [http://en.wikipedia.org/wiki/Border_Gateway_Protocol Border Gateway Protocol] (BGP) on routers that connect the AS's. The BGP computes routes between every AS and every IP address.<ref name=BGP Background">[http://www.informs-sim.org/wsc04papers/038.pdf]J. Kim et al., A BGP Attack Against Traffic Engineering, PROCEEDINGS OF THE 2004 WINTER SIMULATION CONFERENCE 318 (2004).</ref> | The internet is a large-scale decentralized network. A packet sent from one computer to another may cross multiple networking administrative domains (called Autonomous Systems [AS]). Internet routing includes two different systems: an intra-domain routing system and an inter-domain routing system. AS routes traffic within its infrastructure any way it likes, but all of the AS's coordinate inter-domain routing by running a [http://en.wikipedia.org/wiki/Border_Gateway_Protocol Border Gateway Protocol] (BGP) on routers that connect the AS's. The BGP computes routes between every AS and every IP address.<ref name=BGP Background">[http://www.informs-sim.org/wsc04papers/038.pdf]J. Kim et al., A BGP Attack Against Traffic Engineering, PROCEEDINGS OF THE 2004 WINTER SIMULATION CONFERENCE 318 (2004).</ref> As a basic matter: When you type a domain like "news.com" into your Web browser, it uses the Domain Name System to cough up a numeric Internet address, e.g. 216.239.113.101. That IP address is handed to your router, which uses a table of addresses to figure out the next hop toward the news.com server. | ||
To attack the network itself, however, it is then possible to cause a disconnect in the BGP-AS connection. The best example of an attack on internet as a network is such a BGP attack: this kind of attack gained publicity through the recent incident in which Pakistan accidentally took down YouTube. See this [http://www.ripe.net/news/study-youtube-hijacking.html case study on Pakistan & Youtube] and this [http://www.wired.com/threatlevel/2008/08/revealed-the-in/ comment on the threat of BGP hijacking] for more details. | Kim Davies, ICANN's manager of route zone services, says ICANN isn't able to revoke the AS number of a misbehaving network provider. "It's best to think of them as similar to post codes or ZIP codes," Davies said. "We maintain a registry of them to ensure that they aren't conflicting." If the address information provided by AS is reliable, all is well. But if an AS makes a false broadcast, because of a configuration mistake or for malicious reasons, all hell can break loose. | ||
To attack the network itself, however, it is then possible to cause a disconnect in the BGP-AS connection. The best example of an attack on internet as a network is such a BGP attack: this kind of attack gained publicity through the recent incident in which Pakistan accidentally took down YouTube. See this [http://www.ripe.net/news/study-youtube-hijacking.html case study on Pakistan & Youtube] and this [http://www.wired.com/threatlevel/2008/08/revealed-the-in/ comment on the threat of BGP hijacking] for more details. These kinds of attacks aren't new or unique: a network provider in Turkey once [http://www.renesys.com/blog/2005/12/internetwide_nearcatastrophela.shtml pretended to be the whole internet]. | |||
The main solution that has been suggested is for network providers to be automatically notified when the virtual location of an Internet address changes, which is what some researchers have suggested in the form of a "hijack alert system."<ref>[http://iar.cs.unm.edu/]IAR</ref><ref>[http://irl.cs.ucla.edu/papers/originChange.pdf], Alert System Proposal</ref> Another is to treat broadcasts with changes of addresses as suspicious for 24 hours and then accept them as normal. Simple filtering of broadcasts may not always work because some networks provide connectivity to customers with thousands of different routes.<ref>Declan McCullagh, âHow Pakistan Knocked YouTube Offline (and how to make sure it never happens again),â CNET NEWS BLOG, Feb. 25, 2008, http://news.cnet.com/8301-10784_3-9878655-7.html.</ref> | |||
Arguably the most extensive countermeasure would be a technology like Secure BGP,<ref>[http://www.ir.bbn.com/sbgp/]Secure BGP</ref> which uses encryption to verify which network providers own Internet addresses and are authorized to broadcast changes. But Secure BGP has been around in one form or another form since 1998, and is still not a widely-used standard, mostly because it adds complexity and routers that understand will add additional cost. | |||
===II. Vulnerability in the Network Endpoints=== | ===II. Vulnerability in the Network Endpoints=== | ||
| Line 32: | Line 40: | ||
====A. SCADA Systems==== | ====A. SCADA Systems==== | ||
[http://en.wikipedia.org/wiki/SCADA SCADA] systems (SCADA stands for supervisory control and data acquisition) are computer systems that oversee industrial computer systems. Generally the term is used to refer to governmental systems such as the computer systems that regulate dams, traffic lights, and other components of civilian infrastructure. One of the most public issues has been concern that a hacker could shut down public power grids or that terrorists could utilize the SCADA systems to destroy infrastructure. See [[SCADA | [http://en.wikipedia.org/wiki/SCADA SCADA] systems (SCADA stands for supervisory control and data acquisition) are computer systems that oversee industrial computer systems. Generally the term is used to refer to governmental systems such as the computer systems that regulate dams, traffic lights, and other components of civilian infrastructure. One of the most public issues has been concern that a hacker could shut down public power grids or that terrorists could utilize the SCADA systems to destroy infrastructure. See this recommendation [http://www.oe.netl.doe.gov/docs/prepare/21stepsbooklet.pdf "21 Steps to Improve SCADA security"] for how to address these threats. See a report on a [http://online.wsj.com/article/SB123914805204099085.html SCADA hijack into the US electricity grid (2009)] or this report on [http://www.computerworld.com/s/article/108735/Utility_hack_led_to_security_overhaul Australian sewage and water system hack] for examples of the type of vulnerabilities we face. Also consider more extreme examples: could a hacker access a [http://tech.commongate.com/post/Hacker_Hits_Nuclear_Plant nuclear power plant]? | ||
====B. Servers==== | ====B. Servers==== | ||
Rather than targeting individual computers, attackers can target servers and providers. Once a server is infected, it propagates the infection and compromises other internal computers and sensitive servers incorrectly thought to be protected from unauthorized access by external entities. This infection can also result in servers being shut down by regulators in order to prevent the spread of infection, thereby effectively stopping business at that site. This can have significant implications depending on the nature of the site. | Rather than targeting individual computers, attackers can target servers and providers. Once a server is infected, it propagates the infection and compromises other internal computers and sensitive servers incorrectly thought to be protected from unauthorized access by external entities. This infection can also result in servers being shut down by regulators in order to prevent the spread of infection, thereby effectively stopping business at that site. This can have significant implications depending on the nature of the site. | ||
There appear to be two main avenues for exploiting and compromising web servers: brute force password guessing attacks and web application attacks. Microsoft SQL, FTP, and SSH servers are popular targets for password guessing attacks because of the access that is gained if a valid username/password pair is identified. SQL Injection, Cross-site Scripting and PHP File Include attacks continue to be the three most popular techniques used for compromising web sites. Automated tools, designed to target custom web application vulnerabilities, make it easy to discover and infect several thousand web sites. See this evaluation of the [http://www.sans.org/top-cyber-security-risks/ Top Cyber-Security Risks]. | |||
====C. Personal Computers==== | ====C. Personal Computers==== | ||
| Line 53: | Line 63: | ||
<blockquote>Whether through a sneaky vector like the one Morris used, or through the front door, when a trusting user elects to install something that looks interesting without fully understanding it, opportunities for accidents and mischief abound. A hobbyist computer that crashes might be a curiosity, but when a home or office PC with yearsâ worth of vital correspondence and papers is compromised, it can be a crisis. And when thousands or millions of individual, business, research, and government computers are subject to attack, we may find ourselves faced with a fundamentally new and harrowing scenario. As the unsustainable nature of the current state of affairs becomes more apparent, we are left with a dilemma that cannot be ignored. How do we preserve the extraordinary benefits of generativity, while addressing the growing vulnerabilities that are innate to it?</blockquote> | <blockquote>Whether through a sneaky vector like the one Morris used, or through the front door, when a trusting user elects to install something that looks interesting without fully understanding it, opportunities for accidents and mischief abound. A hobbyist computer that crashes might be a curiosity, but when a home or office PC with yearsâ worth of vital correspondence and papers is compromised, it can be a crisis. And when thousands or millions of individual, business, research, and government computers are subject to attack, we may find ourselves faced with a fundamentally new and harrowing scenario. As the unsustainable nature of the current state of affairs becomes more apparent, we are left with a dilemma that cannot be ignored. How do we preserve the extraordinary benefits of generativity, while addressing the growing vulnerabilities that are innate to it?</blockquote> | ||
ref | More discussion on generativity and security can be found in the following references.<ref>[http://bostonreview.net/BR33.2/zittrain.php]Jonathan Zittrain, Protecting the Internet Without Wrecking It, Boston Review (2008).</ref><ref>[http://www.ericjohnolson.com/blog/2007/08/31/saving-the-web-should-we-sacrifice-generativity-for-safety-and-security/]Eric Olson, Saving the Web: Should we sacrifice generativity for security?, Olson's Observations.</ref><ref>[http://www.temple.edu/lawschool/dpost/Zittrain.pdf]David Post, The Theory of Generativity (response/evaluation of Zittrain's ideas).</ref><ref>[http://www.emergentchaos.com/archives/2008/04/generativity_emergent_cha.html]Adam, Generativity, Emergent Chaos and Adam Thierer.</ref> | ||
=====1. Government Computers===== | |||
In this year alone, we've seen data about the presidential chopper appear on [http://www.switched.com/2009/03/09/iranian-computer-found-to-have-info-on-presidential-chopper/ Iranian laptops], warnings about [http://www.switched.com/2009/03/23/hackers-could-cause-blackouts-on-smart-grid/ hackers causing blackouts], an [http://www.switched.com/2009/02/11/faa-systems-hacked-employee-information-released/ intrusion into the FAA], and a wholesale hijacking of the [http://www.switched.com/2009/02/01/federal-job-applicant-database-hacked/ federal government's job listing] site. All this while the Pentagon has spent over [http://www.switched.com/2009/04/09/pentagon-spends-100m-in-6-months-on-cyber-attacks/ $100 million] to protect against such attacks, which are only [http://www.switched.com/2009/02/21/attacks-on-federal-computers-increase-by-40/ expected to increase]. | |||
http://www. | [http://www.wired.com/threatlevel/2008/09/the-analyzer-su/ Ehud Tenenbaum] ("The Analyzer") is one of the most famous hackers to break into government computers. He was only 19 when he was arrested in one of the first high-profile hacking cases. Even though his attacks were considered "unsophisticated" at the time (exploiting a known vulnerability in the Solaris operating system), he still managed to breach systems belonging to the Department of Defense, Air FOrce and Navy, NASA, and MIT. | ||
http:// | Earlier this year, hackers broke into the Pentagon's $300 billion [http://online.wsj.com/article/SB124027491029837401.html Joint Strike Fighter project] -- the Defense Department's costliest weapons program ever. This has raised significant military concerns: a Pentagon report issued last month said that the Chinese military has made "steady progress" in developing online-airfare techniques. China hopes its computer skills can help it compensate for an underdeveloped military, the report said. China [http://www.telegraph.co.uk/news/worldnews/asia/china/5193207/China-denies-claims-it-hacked-into-Pentagon-computers.html denies] that it was responsible for the hack. | ||
http://www. | |||
=====2. Industrial Computers===== | =====2. Industrial Computers===== | ||
[[ | Depending on the industry that is hacked, computer vulnerabilities in industry can mean loss of revenue, distribution of valuable (and potentially dangerous) technological information -- even biological or chemical weapon information or nuclear technology. Tenenbaum recently made a re-appearance as a hacker and is being held responsible for taking more than [http://www.wired.com/threatlevel/2009/03/the-analyzer-ha/ $10 Million from U.S. Banks]. In 2003, 39% of [http://news.zdnet.co.uk/security/0,1000000189,2136212,00.htm global banks had been hacked] at least once. And attacks against industries and financial institutions are [http://www.wallstreetandtech.com/data-security/showArticle.jhtml;jsessionid=0I0CGCB0CXWVNQE1GHPCKHWATMY32JVN?articleID=201806928&_requestid=474611 increasing]: in 2007 alone attacks rose 81%. As more of our banking transactions take place online, hacking becomes even more valuable as a business. | ||
=====3. Private Individual Computers===== | =====3. Private Individual Computers===== | ||
===Application in Cyberwarfare=== | ===Application in Cyberwarfare=== | ||
For general background information on cyberwarfare, browse [http://staff.washington.edu/dittrich/cyberwarfare.html the Washington resource] page (includes definitions, strategies and news articles on point). For an example of cyberwarfare in action, read [http://drop.io/cyberlaw_winter10 Palestinian Cyberwar] by Allen and Demchack: it provides a good explanation of exactly how such a war is conducted. | |||
== NEXT STEPS == | == NEXT STEPS == | ||
Earlier this year, the White House released a [http://www.whitehouse.gov/assets/documents/Cyberspace_Policy_Review_final.pdf Cyberspace Policy Review] that recognizes the far-reaching impact of cybersecurity and the currently vulnerable position of the United States. The Near-Term and Mid-Term action plans from that report are reproduced below. | |||
The most-discussed / most publicized step towards improving cybersecurity is to [http://www.msnbc.msn.com/id/32290186/ns/politics-white_house/ name a Cyber Czar]. Since Obama initially announced this intention in May, 2009, however, the position has continued to go unfilled. Some politicians support this move (see [http://www.fcw.com/Articles/2009/10/30/Web-Lieberman-Cybersecurity-Legislation.aspx Lieberman], but other experts are critical of this position - considering either unnecessary or actually counterproductive (see [http://www.wired.com/dangerroom/2009/08/white-house-cyber-czar-resigns-good-riddance/ Tanji] and [http://www.fcw.com/Articles/2009/11/02/Web-Collins-cybersecurity-coordinator-opposition.aspx Collins]). | |||
Legislation on a variety of fronts is also being considered, though not everyone is sure what (if anything) the new legislation would add.<ref>[http://www.fcw.com/Articles/2009/05/04/news-congress-cybersecurity.aspx]Ben Bain, Lawmakers Attack Cybersecurity on Multiple Fronts, Federal Computer Week, May 1, 2009.</ref> | |||
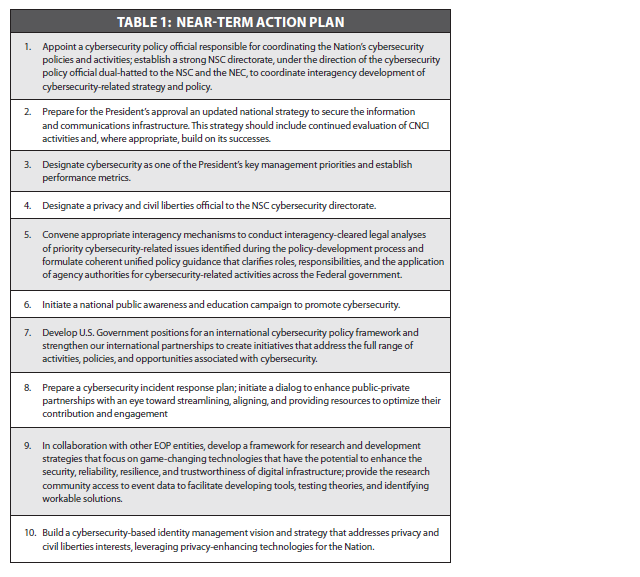
[[Image:Near_Term_Action_Plan.PNG|White House Cyber Security Review Near Term Action Plan]] | [[Image:Near_Term_Action_Plan.PNG|White House Cyber Security Review Near Term Action Plan]] | ||
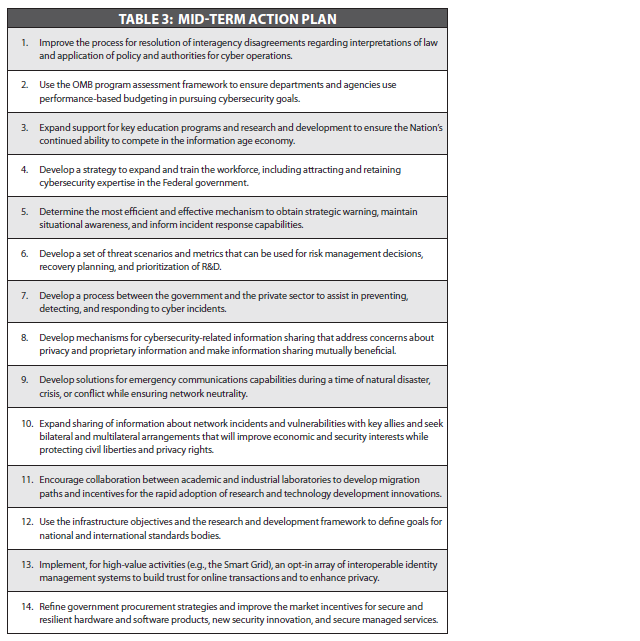
[[Image:Mid-Term_Action_Plan.PNG|White House Cyber Security Review Mid-Term Action Plan]]<ref | [[Image:Mid-Term_Action_Plan.PNG|White House Cyber Security Review Mid-Term Action Plan]] | ||
<ref>[http://www.whitehouse.gov/assets/documents/Cyberspace_Policy_Review_final.pdf White House Cyberspace Policy Review], p37-38 (March, 2009).</ref> | |||
==REFERENCES== | ==REFERENCES== | ||
<references/> | <references/> | ||
Latest revision as of 19:57, 14 August 2024
For the cybersecurity student group's discussions from the Cyberlaw: Difficult Problems Class, see Cybersecurity Brainstorming
SCOPE OF THE PROBLEM
According to the U.S. federal government, threats to cyberspace pose one of the most serious economic and national security challenges of the 21st Century.[1] An increasing number of state and non-state actors are now capable of targeting U.S. citizens, financial institutions, critical infrastructure, and government organizations. The Commission on Cybersecurity, established to advice President Obama in his new administration, stated the challenge: "America's failure to protect cyberspace is one of the most urgent security problems facing the new administration."[2] In fact, the intelligence community assessment is that already a number of nations have the capability to conduct crippling attacks against the U.S.[1]
One reason cybersecurity poses such a security threat is that the term 'cybersecurity' applies to almost everything. The White House Cyberspace Policy Review that analyzes the current cybersecurity threat defines the term broadly:
Cybersecurity policy as used in this document includes strategy, policy, and standards regarding the security of and operations in cyberspace, and encompasses the full range of threat reduction, vulnerability reduction, deterrence, international engagement, incident response, resiliency, and recovery policies and activities, including computer network operations, information assurance, law enforcement, diplomacy, military, and intelligence missions as they relate to the security and stability of the global information and communications infrastructure. The scope does not include other information and communications policy unrelated to national security or securing the infrastructure.[3]
Summarizing, the Policy Review notes that âCyberspace touches practically everything and everyone.â[3] Given this definition, it is no wonder that cybersecurity is perceived as an almost insurmountable problem. In order to begin approaching solutions, therefore, we will first begin by breaking down our understanding of what cybersecurity means.
For pictures of the whiteboards from Professors Goldsmith and Zittran's conversation can be found here.
ASSESSING VULNERABILITY
The internet is a large-scale decentralized network of generative computers. (For an introduction to how the internet works, read the first two pages of BGP Attack.) This network is vulnerable to attack at several different key points, each with a different result and security concern. The taxonomy below breaks down the security issues according to what part of the network is under attack. Real life examples of attacks are then provided to illustrate the danger of attacks, and the application of this knowledge to cyberwarfare is then considered.
If you need background on how the internet works and is related, watch JZ's background video about internet and law.
In order to help us understand cybersecurity, we can break down our analysis of vulnerable points in cyberspace by separating out the point of attack.
I. Vulnerability in the Network Itself
This vulnerability considers attacks upon the network itself. A clever hacker could shut down the internet itself in an extreme case, or more conservatively can re-route the internet to prevent users from getting where they need to go.
The internet is a large-scale decentralized network. A packet sent from one computer to another may cross multiple networking administrative domains (called Autonomous Systems [AS]). Internet routing includes two different systems: an intra-domain routing system and an inter-domain routing system. AS routes traffic within its infrastructure any way it likes, but all of the AS's coordinate inter-domain routing by running a Border Gateway Protocol (BGP) on routers that connect the AS's. The BGP computes routes between every AS and every IP address.[4] As a basic matter: When you type a domain like "news.com" into your Web browser, it uses the Domain Name System to cough up a numeric Internet address, e.g. 216.239.113.101. That IP address is handed to your router, which uses a table of addresses to figure out the next hop toward the news.com server.
Kim Davies, ICANN's manager of route zone services, says ICANN isn't able to revoke the AS number of a misbehaving network provider. "It's best to think of them as similar to post codes or ZIP codes," Davies said. "We maintain a registry of them to ensure that they aren't conflicting." If the address information provided by AS is reliable, all is well. But if an AS makes a false broadcast, because of a configuration mistake or for malicious reasons, all hell can break loose.
To attack the network itself, however, it is then possible to cause a disconnect in the BGP-AS connection. The best example of an attack on internet as a network is such a BGP attack: this kind of attack gained publicity through the recent incident in which Pakistan accidentally took down YouTube. See this case study on Pakistan & Youtube and this comment on the threat of BGP hijacking for more details. These kinds of attacks aren't new or unique: a network provider in Turkey once pretended to be the whole internet.
The main solution that has been suggested is for network providers to be automatically notified when the virtual location of an Internet address changes, which is what some researchers have suggested in the form of a "hijack alert system."[5][6] Another is to treat broadcasts with changes of addresses as suspicious for 24 hours and then accept them as normal. Simple filtering of broadcasts may not always work because some networks provide connectivity to customers with thousands of different routes.[7]
Arguably the most extensive countermeasure would be a technology like Secure BGP,[8] which uses encryption to verify which network providers own Internet addresses and are authorized to broadcast changes. But Secure BGP has been around in one form or another form since 1998, and is still not a widely-used standard, mostly because it adds complexity and routers that understand will add additional cost.
II. Vulnerability in the Network Endpoints
The internet as a network joins together numerous end point computers. These endpoints are all vulnerable targets in and of themselves, though the nature of the end point changes some of the ramifications of its attack.
A. SCADA Systems
SCADA systems (SCADA stands for supervisory control and data acquisition) are computer systems that oversee industrial computer systems. Generally the term is used to refer to governmental systems such as the computer systems that regulate dams, traffic lights, and other components of civilian infrastructure. One of the most public issues has been concern that a hacker could shut down public power grids or that terrorists could utilize the SCADA systems to destroy infrastructure. See this recommendation "21 Steps to Improve SCADA security" for how to address these threats. See a report on a SCADA hijack into the US electricity grid (2009) or this report on Australian sewage and water system hack for examples of the type of vulnerabilities we face. Also consider more extreme examples: could a hacker access a nuclear power plant?
B. Servers
Rather than targeting individual computers, attackers can target servers and providers. Once a server is infected, it propagates the infection and compromises other internal computers and sensitive servers incorrectly thought to be protected from unauthorized access by external entities. This infection can also result in servers being shut down by regulators in order to prevent the spread of infection, thereby effectively stopping business at that site. This can have significant implications depending on the nature of the site.
There appear to be two main avenues for exploiting and compromising web servers: brute force password guessing attacks and web application attacks. Microsoft SQL, FTP, and SSH servers are popular targets for password guessing attacks because of the access that is gained if a valid username/password pair is identified. SQL Injection, Cross-site Scripting and PHP File Include attacks continue to be the three most popular techniques used for compromising web sites. Automated tools, designed to target custom web application vulnerabilities, make it easy to discover and infect several thousand web sites. See this evaluation of the Top Cyber-Security Risks.
C. Personal Computers
The term personal computers is meant broadly to apply to individual computers rather than larger servers or systems. However, the use of these computers - whether for government application, industrial business, or private personal use - has a significant impact on the nature of the security concern. One of the vulnerabilities that all types of personal computers share, however, is that all the computers are generative, having the power to create. This very generativity adds to the potential vulnerability of the computers.
In his book, The Future of the Internet and How To Stop It (Chapter 3) on generativity and cybersecurity, Zittrain describes the Morris Worm Attack - the first virus attack (1988) and how the changing nature of the internet made that attack possible:
[T]he Morris worm really was not perceived as a network problem, thanks to the intentional conceptual separation of network and endpoint. The Morris worm used the network to spread but did not attack it beyond slowing it down as the worm multiplied and continued to transmit itself. The wormâs targets were the networkâs endpoints: the computers attached to it. The modularity that inspired the Internetâs design meant that computer programming enthusiasts could write software for computers without having to know anything about the network that would carry the resulting data, while network geeks could devise new protocols with a willful ignorance of what programs would run on the devices hooked up to it, and what data would result from them. Such ignorance may have led those overseeing network protocols and operation unduly to believe that the worm was not something they could have prevented, since it was not thought to be within their design responsibility.
...
Even without...flaws, the machines were intentionally designed to be operated at a distance, and to receive and run software sent from a distance. They were powered on and attached to the network continuously, even when not in active use by their owners. Moreover, many administrators of these machines were lazy about installing available fixes to known software vulnerabilities, and often utterly predictable in choosing passwords to protect entry to their computer accounts. Since the endpoint computers infected by the worm were run and managed by disparate groups who answered to no single authority for their use, there was no way to secure them all against attack.
The computers could not be secured because each computer could incorporate the code, use it and further distribute it.
Whether through a sneaky vector like the one Morris used, or through the front door, when a trusting user elects to install something that looks interesting without fully understanding it, opportunities for accidents and mischief abound. A hobbyist computer that crashes might be a curiosity, but when a home or office PC with yearsâ worth of vital correspondence and papers is compromised, it can be a crisis. And when thousands or millions of individual, business, research, and government computers are subject to attack, we may find ourselves faced with a fundamentally new and harrowing scenario. As the unsustainable nature of the current state of affairs becomes more apparent, we are left with a dilemma that cannot be ignored. How do we preserve the extraordinary benefits of generativity, while addressing the growing vulnerabilities that are innate to it?
More discussion on generativity and security can be found in the following references.[9][10][11][12]
1. Government Computers
In this year alone, we've seen data about the presidential chopper appear on Iranian laptops, warnings about hackers causing blackouts, an intrusion into the FAA, and a wholesale hijacking of the federal government's job listing site. All this while the Pentagon has spent over $100 million to protect against such attacks, which are only expected to increase.
Ehud Tenenbaum ("The Analyzer") is one of the most famous hackers to break into government computers. He was only 19 when he was arrested in one of the first high-profile hacking cases. Even though his attacks were considered "unsophisticated" at the time (exploiting a known vulnerability in the Solaris operating system), he still managed to breach systems belonging to the Department of Defense, Air FOrce and Navy, NASA, and MIT.
Earlier this year, hackers broke into the Pentagon's $300 billion Joint Strike Fighter project -- the Defense Department's costliest weapons program ever. This has raised significant military concerns: a Pentagon report issued last month said that the Chinese military has made "steady progress" in developing online-airfare techniques. China hopes its computer skills can help it compensate for an underdeveloped military, the report said. China denies that it was responsible for the hack.
2. Industrial Computers
Depending on the industry that is hacked, computer vulnerabilities in industry can mean loss of revenue, distribution of valuable (and potentially dangerous) technological information -- even biological or chemical weapon information or nuclear technology. Tenenbaum recently made a re-appearance as a hacker and is being held responsible for taking more than $10 Million from U.S. Banks. In 2003, 39% of global banks had been hacked at least once. And attacks against industries and financial institutions are increasing: in 2007 alone attacks rose 81%. As more of our banking transactions take place online, hacking becomes even more valuable as a business.
3. Private Individual Computers
Application in Cyberwarfare
For general background information on cyberwarfare, browse the Washington resource page (includes definitions, strategies and news articles on point). For an example of cyberwarfare in action, read Palestinian Cyberwar by Allen and Demchack: it provides a good explanation of exactly how such a war is conducted.
NEXT STEPS
Earlier this year, the White House released a Cyberspace Policy Review that recognizes the far-reaching impact of cybersecurity and the currently vulnerable position of the United States. The Near-Term and Mid-Term action plans from that report are reproduced below.
The most-discussed / most publicized step towards improving cybersecurity is to name a Cyber Czar. Since Obama initially announced this intention in May, 2009, however, the position has continued to go unfilled. Some politicians support this move (see Lieberman, but other experts are critical of this position - considering either unnecessary or actually counterproductive (see Tanji and Collins).
Legislation on a variety of fronts is also being considered, though not everyone is sure what (if anything) the new legislation would add.[13]
REFERENCES
- ↑ 1.0 1.1 [1]Dennis Blair, Director of National Intelligence, Annual Threat Assessment of the Intelligence Services Committee, Statement for the Record, March 10, 2009, at 39.
- ↑ [2]CSIS Commission on Cybersecurity, Security Cyberspace for the 44th Presidency, Dec. 2008.
- ↑ 3.0 3.1 [3] White House Cyberspace Policy Review, p2 (March, 2009).
- ↑ [4]J. Kim et al., A BGP Attack Against Traffic Engineering, PROCEEDINGS OF THE 2004 WINTER SIMULATION CONFERENCE 318 (2004).
- ↑ [5]IAR
- ↑ [6], Alert System Proposal
- ↑ Declan McCullagh, âHow Pakistan Knocked YouTube Offline (and how to make sure it never happens again),â CNET NEWS BLOG, Feb. 25, 2008, http://news.cnet.com/8301-10784_3-9878655-7.html.
- ↑ [7]Secure BGP
- ↑ [8]Jonathan Zittrain, Protecting the Internet Without Wrecking It, Boston Review (2008).
- ↑ [9]Eric Olson, Saving the Web: Should we sacrifice generativity for security?, Olson's Observations.
- ↑ [10]David Post, The Theory of Generativity (response/evaluation of Zittrain's ideas).
- ↑ [11]Adam, Generativity, Emergent Chaos and Adam Thierer.
- ↑ [12]Ben Bain, Lawmakers Attack Cybersecurity on Multiple Fronts, Federal Computer Week, May 1, 2009.
- ↑ White House Cyberspace Policy Review, p37-38 (March, 2009).