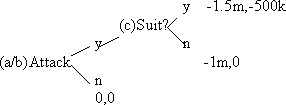
Advertise That I May Hear Ye: The Eyeball Consumers of the Internet
Paul Gowder
Introduction
"There you go, talking about class again" 1
On the net, there are very few actual benefits to the vaunted "cheap speech." The term itself is a complete misnomer. "Speech" has always been free. It is entirely costless to yell one’s brilliant ideas into a well, and hope for a reply. The proponents of "cheap speech" are, in reality, referring to "cheap audience" – the idea that it is easier, in terms of time and effort, to reach people and influence them with ideas over the net.
This paper critically examines, and ultimately rejects, this idea. The unavoidable conclusion is that, to the extent audiences are cheaper over the net, they are only cheaper for those people (corporations and the wealthy) who already have the means to reach audiences in physical space. Finally, this paper proposes several solutions for a society as a whole, interested in using the net as a tool to advance weak 2 viewpoints, promote minority businesses, and otherwise create a greater pool of social contribution. A few suggestions are also offered for those disempowered people who wish to take advantage of the internet to attract their own audience.
The Problem
It is at this point useful to mention a couple of guiding principles for this paper. First, and most important, is the concept that I will call "marginality." This is the idea that, as players with functionally unlimited wealth compete for scarce resources, the price of the resource rises to that point at which the buyer receives $1.01 from each additional dollar spent. This is called marginality because economists, when describing behavior like that in various contexts, have only one thing in common, the description of that $1.01 point as the "marginal" point, or rate of return, or cost, or something similar. 3 This is extremely important on the internet because of one special "how the net is different" factor.
This is the second guiding principle of this paper: the competition between commercial and noncommercial speakers. 4 In non-internet space, marginality does not pose a problem for small speakers because the quantity of speech is limited – speech is the scarce resource, not listeners. 5 In cyberspace, however, the ability for "anyone to speak", and the adaptability of the medium for all forms of communication, from commercial to political, has heavily changed the speaker-listener ratio. As a result, speakers have to compete with each other for audience members. 6 The cost of the audience members is expressed many ways (the entirety, in fact, of part one of this paper), but is always a uniform cost for both commercial and noncommercial speakers. Offline, the costs of noncommercial speakers are significantly lower, because they only compete with each other.
For example, the cost of putting a noncommercial statement in the newspaper is limited to the cost of the writing ability and postage necessary to convince the editorial staff to include your opinion in the "letters to the editor" section. A commercial speaker must pay the advertisement rates and occupy that space. It would be as unusual to see political messages in a corporate retreat as it would to see Ford advertising by writing in chalk on the sidewalks. While public communication is still at a disadvantage, there are at least some places that are given solely to the group. On the net, there are no such "zones" dividing the editorial page from the classified ads from front page bottom corner. While this is a fine method for choosing between purely economic actors, it is a poor method for choosing between economic and social actors. This paper proposes creation of such differentiated spaces as one way of minimizing the competition 7 between commercial and noncommercial speakers.
The third major principle is what I will call "credibility disintermediation" (or filter dislocation). 8 This refers to the fact that, offline, listeners can judge the credibility of speakers (or, expressed in the language of this paper, speakers can earn the currency of credibility necessary to get listener time) through third party intermediaries. Thus, the credibility of a restaurant review is established once it is printed in the New York Times. This gives a certain amount of power to the credibility granters: off the net, the powerful players effectively act as filters for information: in order to get the credibility of the NYT, you have to be hired by the NYT. On the net, viewers are forced to judge this for themselves. While this may seem more democratic: the NYT can no longer control credibility, it is merely an illusion. If viewers judge credibility from (in the language of this paper, sell their attention based on) links from the NYT web site, or the presence of expensive site design tools that can make their site look like the NYT site, the goals of democratization are lost. If it is the case that the internet does allow more people to put communications "out", to potentially reach large numbers of people, there must be some additional filtering mechanism to protect readers from untrustworthy information. It seems that the filtering mechanism has simply shifted from an editor to a mass of individuals. 9
Gaining an audience: a dissection
It is a relatively simple matter to isolate those needed to communicate a message of any kind to an audience of willing or unwilling listeners. One needs to have a message to communicate, to some general pool of members out of which your audience may be chosen. One needs to have a means of offering (or propelling) that message to the audience. At that point, one needs a group of people out of that audience willing and able to listen to the specific message (as opposed to the entire pool, who may be willing to listen to the offer of the message: the "click on this link to reach my site"). Finally, one needs the credibility to influence audience members to be, at the very least, willing to take the speech seriously, and evaluate it on the merits. Each of these "audience economy" factors has its own cost which must be paid for effective communication. In addition, success has its own ex post price.
Pool
If a tree falls in usenet, does it make a sound?
The first hurdle which any speaker will encounter is simply finding a group of people who are in a situation to be able to reach their message. On the net, this requires three things. First, that the intended audience be on the internet. Second, the intended audience must be able to find the offer of ideas: the communication must be accessible, not only technically, but easily and cheaply for the potential reader. Finally, they must convince the reader that the communication is worth their time.
The first factor is especially difficult for minority messages. 10 While it is extremely difficult to find information on the precise composition of race, age, religion, etc. on the net, it is likely that the internet is predominantly white, middle-class, and American. This can be assumed simply from the amount of money still required to get on the internet for any significant period of time (20 minutes at the local public library, for example, would not be significant.). A modern computer from a major, easy to reach, retailer still costs between one and two thousand dollars. 11 That about sums it up – unless a small speaker is employed at one of the high-paying jobs involving computers with internet access, or at an institute of higher education offering the same, they are fundamentally shut out from internet access. Whole sections of the potential audience are lost to speech. A speaker who wishes to promote unionization among migrant laborers can shout and shout all she wants on the internet, without that communication ever reaching its intended audience.
To reach this pool, one must purchase advertising on the major portal sites. This is the clearest application of the marginality principle. Portal sites having an oligopoly on eyeballs can charge up to the point where the richest speakers are not willing to purchase their entire stock. This creates a deadweight loss for the smaller purchasers, who can not get any eyeballs from the portals. 12
Credibility
"I DON’T LIKE SPAM!" 13
The most tragic factor for minority speakers with ideas or goods and services to contribute to the group is inability to attain credibility. As a general matter, credibility can be bought. This can be seen by the simple expedient of comparing the perceived honesty of a businessman on Rodeo Drive in Beverly Hills with one on Normandy in South Central LA. Likewise, a speaker giving a harangue in Harvard Square is more credible in an Armani suit than in the rags of a homeless person. On the internet this factor, obvious to anyone, is translated into more subtle appearance and location factors. 14
One oft ignored problem with the internet as a mode of transmission is the credibility gap between the internet itself, and more traditional modes of communication. Cyberspace has not earned full "rights" as a medium for credible communications. For example, many businesses do not communicate with potential clients, employees, or contractors over the internet, considering it unprofessional or unnecessary. 15 Even on the internet, there is a heightened awareness of "scams," 16 false information, dishonesty, and "kooks" 17 that would not be present were the same messages communicated in non-electronic form.
Even those parts of the medium which have exact analogs in physical space are disadvantaged on the internet. For example, "junk mail," when transmitted through the United States Postal Service third class mail, is considered obnoxious and is often thrown away unread. Junk mail, when send over the internet by people not equipped to do bulk physical mailings, is met with ISP complaints, denial of service attacks, lawsuits 18 and legislation. 19
Finally, the usual offline problems with credibility of weaker speakers are repeated online. Since poor people are less likely to be able to afford education, and education increases earning power, it is just as difficult online as offline for socially weaker individuals to communicate their ideas. This is even exacerbated on the internet because the vast majority of communication is done through text, requiring strong written communication skills. 20 In addition to the flaws in education that can be detected and filtered through the bias of a listener to a spoken discussion, the additional formal rules of written English (like spelling and punctuation) can operate on the internet to further reduce the credibility of persons with a lack of formal education. Furthermore, much communication on the internet requires a certain minimum of technical knowledge – a working command of HTML to build a presentable web page, basic competence in the normal software of internet access. These too may be out of the reach of a less empowered internet user, and in an environment such as usenet where users are regularly castigated for setting their carriage return at anything greater than 80 characters, these small problems can have a huge impact on the credibility of a speaker. This impact is intensified when the audience compares it to a more mainstream information source, such as the New York Times, 21 which produces easily readable web pages most likely built by professional web designers.
One additional difficulty for the weak speaker is the lack of access to the tools of greater speakers. The cliche of free press for those who own one holds on the internet, but is no longer a means of distinguishing not between those who own presses and are capable of mass producing documents and those who are not. Rather, it distinguishes between those who have the copy of Adobe Photoshop 22 to produce attractive web pages, and those who do not. This is partly a problem with the legal system’s protection of intellectual property, and partly a problem of marketplaces for technical skill. One major limited resource in the process of the internet (for lack of a better term) is the technical skill (and venture capital) necessary to produce top quality products. As such, the real competition in the case of applications such as Photoshop is between buyers. Commercial speakers drive up the price of such applications by sheer ability and willingness to pay, leaving the weak speakers mired in marginality.
Ex-post price
"You have the right to free speech as long as you’re not dumb enough to actually try it." 23
The law itself does not impose back-end costs (costs after successful communication) on audiences. Rather, the current maladjustment of the legal system allows people opposed to the communication in question to impose additional, often malicious, costs against the speakers. This creates a cruel paradox where the more effective the attempt at getting an audience is, the more painful the eventual backlash from the legal system is.
The first, and most severe, imposition of additional back-end costs to effective communication on the internet is the current confused state of affairs in personal jurisdiction. Many courts have held that publishing a web page subjects a speaker to personal jurisdiction everywhere the page can be read – basically, the entire world, with the possible exception of Antarctica. 24 The standards used to determine jurisdiction on the internet are likely to be highly detrimental to small speakers.
Wide jurisdiction is one of the major causes of the paradox mentioned earlier, that a speaker on the net is punished more as the reach and persuasion of her speech increases. If the internet is to fulfill its potential as the ground for "cheap speech", plaintiffs should not be allowed to retroactively increase the costs of an audience by increasing the potential for punishment as the chances of successful communication increase. The jurisdictional muddle on the internet should be solved by federal legislation, outlined below, or by judicial action.
More "substantive" law also causes a severe increase in back-end costs. The two major substantive areas of difficulty are libel and intellectual property law. This is a short discussion, because these problems have been explored many times before.
Libel law is the most obvious manifestation of the paradox of increasing success equaling increasing costs. The more audience members who can or do receive and are convinced by the offending communication, the more "harm" is allegedly done by the defendant, and the more liability attaches to the conduct. However, this is not as important as the increase in the plausibility of a suit. Assuming a libel suit is likely to lose, with the increasing exposure of the information bringing about the suit, the credibility of the plaintiff’s case can rise, and with this, the costs to the defendant. Cases that could be dealt with in summary judgment may have to go through expensive discovery first. And so on through the system, until the defendant is forced to take down the offending communication or reach bankruptcy. 27
This is perfectly reasonable when reach strictly correlates with wealth. When the New York times is accused of libel, it can afford to defend itself against the ensuing lawsuit. However, a single person with a political manifesto on the internet cannot. Worse still, any speaker who is not aware of these increased costs may not be prepared to pay them, and can then be severely punished through the private law system. A speaker who is aware of these possibilities, of course, will be chilled in the traditional sense.
The same chill can occur in intellectual property law. In this case, however, it may come from two ends, with two different purposes. Trademark law could have the effect of chilling the most effective ways to reach audiences. Copyright law could have the effect of chilling the most effective ways to convince them. This is primarily important in criticism and satire. Again, because this ground has been walked over many times, I will only provide a short summary of the basic arguments.
Trademark law can be used to lock up the most effective ways to reach an audience, in any number of ways. A person wishing to criticize McDonalds, say, for environmentally unfriendly practices, would be most effective registering the domain McDonald’s.com. However, the moment they do this, McDonald’s lawyers will undoubtedly be on the courthouse steps with a trademark infringement suit. 28 Likewise, the person wishing to criticize McDonalds may realize the domain name is already taken. The next step may be the registration of their criticism site in the major search engines under "McDonalds." Come the resulting trademark infringement suit. Then they may advertise their site using the McDonalds trademark. Meeting again the requisite lawyers. The suits, again, do not need to be meritous to silence dissent, just plausible. Trademark is also subject to the paradox illustrated in libel law: the more consumers reach the criticism site instead of McDonald’s, the more "consumer confusion" there is, increasing the plausibility of any suit filed.
Copyright works the same effect on the content of the messages themselves. 29 The organization criticizing McDonalds may decide to copy policy statements that passed through McDonalds headquarters, to the effect of "lets use styrofoam, it’s cheaper and hey, we’re all old, and we don’t have kids, so forget the environment." Doing so immediately subjects them to an expensive copyright suit as the price of convincing their audiences. 30
Another method of increasing back-end costs is through the device of contract. There are many new forms of adhesive contract on the net, with an increasing disassociation from the actual ability of users to consent. On the internet, contract sneaks in many forms – from the "shrinkwrap" used to sell any new software product, through "clickwrap" agreements where a user is told that "clicking ok" binds them to several different "terms of service" and "user agreements" on different sites, to agreements imposed in almost comically unilateral ways. 31 The problem is in the very ubiquity of these contracts on the internet. In a real world commercial transaction, it is clear what circumstances invoke contract, and what do not. It is also generally clear what terms are present in a contract. Walking into a store and purchasing a commercial good is a familiar experience to users, who understand that they are agreeing to pay a fixed price for a known service. On the internet, where there is very little "trade usage" or other common practice support, it is considerably more difficulty for a "little guy" to know what he is agreeing to. Contracts are imposed on the internet for many things that are not normally within the experience of the user – eg. "by viewing the next page you agree to" style clickwrap – and exacerbate the standard problems with adhesive contracts. This becomes important in the realm of speech when ISP’s and quasi ISP’s (such as free e-mail providers) step into the picture. For example, America Online still refuses to publish its list of "dirty words" of which a user consents to the silencing. Likewise, ISP’s as a matter of course bar spam – even though "spam" is very loosely defined. (This would be akin to UPS banning bulk commercial mail.) This increases the cost of speech ex ante by requiring that the user who inadvertently runs afoul of these restrictions go to court or find an alternate way of speaking. 32
The code also assists in the imposition of back-end prices. First, to the extent that smaller speakers can use the internet to reach a wide range of audiences, larger speakers can use the same methods to reach even more people and attack the message. Second, the powerful interests can use any success in reaching people to easily discover the offending speech and take legal or extra-legal action.
This second problem is because most accepted communication on the internet is untargeted. With the exception of extremely expensive targeted search engine ads, and sanctionable bulk mailing, 33 all mass-communication on the internet can not be targeted. While the cost to the speaker is debatable, the cost to an audience member is near zero, except in time. The powerful interest wishing to find hostile information no longer needs to subscribe to the right magazines, but only needs to use 1 search engine to search the entire web, perhaps another to search usenet, and can discover any communication that, in a pre internet world, would perhaps have been limited to a niche audience. This is a variety of the "perfect enforcement" problem in public law. In private law, we have a "perfect information" problem, because powerful interests can now attack all information they find hostile. A disaffected employee, pre-net, could distribute negative, yet true, information about her corporate employer through word-of-mouth, anonymous written communication, and other difficult and less effective techniques. On the internet, however, the employee is tempted by the apparent ease of diffusion to many, and the anonymity she believes she has, to post those negative messages on, for example, a stock valuation website, where the company, concerned about its image, can easily search the web for such postings, and, through any number of means (such as legal action, financial action, or simple intimidation or cooperation), get the true identity of the disaffected employee, for easy termination.
The Solution
Small speakers can take certain "self-help" steps to increase their own exposure. Organization to share vital resources is the most important, and the only one addressed here. The role of the government is somewhat more extensive. The government can directly address those laws which unduly burden small speakers, but can also subsidize low-income speakers and their audiences.
Organization of small speakers
"If love is just a big charge account, why it has to be mine?" 34
The most effective method of self help for small speakers is too become large speakers. Perhaps the best comparison is to the labor unions. An individual group of workers does not have the resources to survive in the event of a strike, nor to compete with "scabs" and control the employment market. When labor unions organize into large groups, some striking at various times (eg. the AFL-CIO), the funds of the members not striking can be used to support the striking members. The unions can also gain more attention to the workplace problems their action is concerned with by virtue of sheer numbers. Similarly, if environmental activists on the internet wish to support each other in an attack on a polluting corporation, their best move would be to contract to support each other in the event one of them gets sued by a powerful opponent. The environmental groups on the internet can create linking programs and search engines to lower the cost for users to discover their speech and increase their joint readership through network effects.
In the case of ex post legal sanctions, the money to defend themselves and survive should be an adequate deterrent for many suits. Especially when the opponent is a corporation or other profit-maximizing entity (such as the church of scientology), the inability to deter critics with ultimately unsuccessful suits will cause the suits to stop. A simple game theoretic model will perhaps demonstrate this best.
Assume a profit making organization, C, wants to deter an attack by B, an individual with a bone to pick, and A, an organization with pooled resources to defend against suit. The cost of an effective attack is 1 million dollars in stock drops, lost business, etc. The cost of filing a lawsuit to each side is 500,000 dollars. B has unallocated defense resources of 50,000 dollars. A has unallocated defense resources of 2 million dollars. B values the ability to cost a million dollars in lost profits at $50,000, the amount of money he is willing and able to spend on legal defense. A, because of the diminishing marginal utility of wealth, is willing to spend more to attack C, and it is worth $700,000 dollars to A to cause a million dollars of loss to C.
Extensive form game of this scenario:
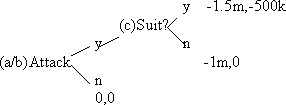
B is unwilling to pay the –500k costs that a lawsuit from C will impose. As a result, if C accepts a certain strategy of always filing suit, B will not attack C. If C builds a reputation for always filing suit, this can actually save C money in the long run. The cost of filing suit twice is recovered in one attack deterred. A, however, because it has more resources, is willing and able to handle the lawsuit costs. As a result, no matter how litiginous C becomes, A will not be deterred as long as the harm (1.5m) creates enough utility (1,050,000 in this case, at a rate of 700k per million) to compensate for the cost of a lawsuit. Because C is a profit-maximizing actor, there is no reason for C to spend an additional 500k when it will deter nobody. The suits will not occur.
This reasoning suggests that minority interests on the net should pool their resources in the event of conflict. 35 However, they can also pool their resources to encourage the effective speech which got them into trouble in the first place.
On the web, there is a site called "Disinformation, the subculture search engine." 36 Disinformation was begun by a group of liberal-minded individuals with technical knowledge and writing skills who wanted to provide links to pages that agree with them, and criticism of those that disagree. To fund this project, they are members of the "at hand network" which places advertising banners on websites and pays per click. This is the ideal way to solve the problem of difficult communication on the web. With adequate publicity, 37 this site could become the portal, or the first place checked, for anyone dissatisfied with the current crop of information. In addition, they should try to gain some commercial leverage, sufficient funds to make a significant advertising dent in major competitors, or some other way of drawing mainstream viewers. The power of such a group effort could influence enough mainstream views to create, through the free market and without government intervention, a competitive "sidewalk" for those dissatisfied with the mainstream "sidewalks." Disinformation does not go nearly far enough. The ideal for a privately run "sidewalk" would be more of a network between fringe sites. This should be open to any site with fewer "hits" per month than some arbitrary number, to track those sites who actually need more effective speech. Resource sharing should also be encouraged – perhaps each member would be asked to contribute something, be it graphics creation ability, writing talent, server space, or some other needed resource, to the good of the group. In addition, the network should engage in some form of revenue raising or sharing activity to enable members to meet legal challenges and meet the costs of site promotion. If resources permit, the fringe network should even attempt to capture more mainstream viewers by setting up a portal site with special preference for those groups who are members of their network.
A full outline of the proposed steps small speakers could take to increase their own exposure is beyond the scope of this paper. However, it should be noted that no such site exists. While many sites exist purporting to create "networks" of other internet speakers, 38 those small speakers are uniformly large – the ACLU, for example, seems to be a member of many of these coalitions. The ACLU does not need the help. Such coalitions should focus on sharing resources between small speakers, not providing yet another list of links for large ones, no matter how socially important those large speakers are.
Government subsidy for low-income computing
2 gigs in every hard drive...
One characteristic of minority viewpoints is that they are not backed up by a lot of money. That is why they are not majority viewpoints. For a poor person in the inner city wanting to speak out against the police, even if they can find a computer, in the library or something, it probably has censorware installed. Even if they can find a computer without censorware, it is probably impossible for them to find webspace. 39 Even if they can find webspace, it is probably impossible for them to find the computer time, in the scarce resources of public libraries, YMCA’s, and similar organizations, to actually publish their views. Even if they manage all that, they probably do not have the knowledge necessary to create web pages, promote them, or successfully post anonymously to usenet. To solve these problems:
Government paring down of internet-unfriendly laws
‘But congressman... how will this affect the web?"
The final government 43 step that can be taken to insure the availability of the internet for dissent is to eliminate those laws which unfairly burden small speakers. This should be done as follows:
One strong way the government can contribute to the diversity of voices on the internet is by completely protecting anonymity. In the scenario of a corporate employee who criticizes his company, and is fired after a routine web or usenet search, the government could save the time and expense of a wrongful termination lawsuit by simply making anonymity the default rule. 55 There may not be much the legal system can do to lower the technical demands of anonymity. It would be extremely difficult and expensive to require corporations to not keep backup copies of e-mail traffic, for example. Fortunately, the government can take some steps to protect anonymity.
Conclusion
The government has an important interest in democratization of viewpoints. Under traditional "marketplace of ideas" theory, the more different ideas that are allowed to enter the market and receive full consideration, the more effective social policy will be. In addition, effective speech allows persons to actualize themselves – they can express their unique personalities and thoughts for the world at large to see.
Many scholars claim that such a structure exists on the internet right now. However, those scholars uniformly ignore the important cost factors outlined in this paper. Until the cost of effective speech is lowered on the internet, small speakers will have free speech without free communication. Without an audience, the promise of "cheap speech" is nothing but an illusion.
The internet provides a great opportunity to allow small speakers to influence society and express their personalities. The internet also poses a great challenge: society, to take advantage of this opportunity, must break the control over the means of, not production, but communication. The internet breaks control over one of the means of speech, but not the means of audience gathering. If society wishes to take full advantage of the potential of the internet as a democratizing medium, the full "ownership of the means of production" of ideas must be transferred to the people as a whole.
FOOTNOTES
1. Monty Python: The Holy Grail (BBC I believe)
2. Fundamentally, “little guys.” The terms “weak” and “minority” will be used interchangeably to refer to the general category of ideas and social or economic positions that tend to be less influential in modern American society. I will also use terms with a similar meaning, such as “less empowered.” Since the net is currently dominated by the majority American perspective “minority” will then include (in addition to other things) international viewpoints and people, racial/religious/sexual orientation minorities, women, the poor, etc. One key test for “weak” people and viewpoints is money - those viewpoints, or attempted commercial activity, likely to fail because of a lack of money to support them. While this paper predominantly refers to disempowered social/political/cultural viewpoints, the issue of commercial activity can not be avoided, both as business is an essential way to convert weak players into strong players, and as the line between commercial and noncommercial activity is increasingly blurred. The difference between this and the class definition of “little guys” is that this paper is not concerned with the problem of little guys as content consumers (eg. persons who no longer have any privacy as a result of cookies), only as content providers.
3. This issue could be an entire paper on its own. A few interesting conversations with people who have economics degrees have revealed the complete lack of actual source material for this argument - apparently, most economics considers this problem from a consumer perspective. The standard argument would then be that the costs of reaching a piece of information, no matter what its inherent value, are high enough for consumers that they choose to “purchase” a different piece of information. This perspective, while supported by the literature on substitution effects and the like, is not useful in this context. In effect, we have to reverse the traditional model and call the speaker (the “producer” of information) a “consumer” of listener time, and call the listener (the “consumer” of information) a “producer” of the same. Due to the dearth of economic research on the internet, however, they simply haven’t gotten there yet. Rather than the (alleged) science of economics, the craft of marketing, much less represented in the academic world, must be applied.
This change in perspective follows naturally from the change in power, and has some interesting dynamics. "Consumers" control the failure or success of net speakers more than they do offline, because the increased supply of substitutable goods creates a very high elasticity of demand in any single good. As such, the cost of satisfying a listener increases, to the point where the speaker is buying a listener, not the other way around. This is further complicated by the growth of such programs as @guard <
http://www.atguard.com> (visited 12-22-98), a filter for listeners to remove advertisements. If such a program becomes popular, it will be a rejection by the listeners of the offer of useful content in exchange for eyeballs on other content. Presumably, advertiser supported content will decrease -- the power relationship from such a product will actually shift in favor of the content provider/eyeball consumer, as supply goes down.It is also important to consider the impact of this on the intellectual property “industry.” If, as I have just claimed, the speaker is “buying” the attention of the audience, the value of her intellectual property comes from what that attention can purchase: as many people have argued, the reason the speaker “buys” attention is not so they can “sell” words, or code, or whatever, but because they then get power in other markets. For example, they “buy” credibility by “buying” attention, and this credibility can then be used to sell books. To put it a different way, one first buys credibility by placing oneself on public access television. If one is successful, one gets picked up by a local television, and is now paid, rather than paying, for the opportunity to speak. Public access television has many fine analogies to small speakers on the internet, one of which is that nobody ever watches it. On the issue of the changing nature of IP on the net, see generally Eric S. Raymond, The Cathedral and the Bazaar, <http://www.tuxedo.org/~esr/writings/cathedral-bazaar/cathedral-bazaar.html> (last updated 11-22-98), John Perry Barlow, IP on The Global Net <http://www.eff.org/~barlow/EconomyOfIdeas.html>. (visited 12-21-98) This will become important when I later argue that one remedy to the audience cost problem is a relaxation of certain IP laws.
Of course, another way to view this is as a disintermediation problem. Where before the consumer’s market for restaurant reviews in New York was mediated by the New York Times hiring process, now it is direct. Two markets existed in the previous example: the “restaurant reviewer” market and the “newspaper” market. Now that these two markets are one, we must use different tools to analyze this new market.
4. The terms “commercial” and “noncommercial” are used here merely to indicate the difference between rich and poor. There is no question that the “noncommercial” speech of a major party presidential candidate is more powerful than a small business selling products to a niche market located in Watts. For the purposes of this context, the major party candidate would be considered a “commercial” speaker, and the small business would be considered a “noncommercial” speaker.
5. The simplest evidence of this can be found in a comparison of the methods of paying for content. Offline, speech is purchased straight away, and one does not expect to find, for example, advertisements in the pages of a book. Though there are advertisers, they do not entirely dominate the space. Online, speakers support their activity by allowing other speakers to share their audience attention through advertising. As the amount of content increases relative to the number of eyeballs, the ratio of advertisement speech to the amount of “pristine” speech increases. (Further evidence of this can be found by comparing the sophistication and power of advertisers before television to that after.)
6. It is important to note that this audience economy is not new -- it has been the case since time immemorial. The strength of the New York Times is not in it's ability to print newspapers -- paper is cheap too -- the strength is in it's ability to reach millions of people. The LA times even advertises in movie theatres. What is new is the extent of the competition, and the new players of a different nature.
7. perhaps better characterized as an "arms race."
8. This was predicted in Eugene Volokh, Cheap Speech and What it Will Do 104 Yale L.J. 1805 (1995). However, Volokh was wrong about the extent of what he calls “The Shift of Power Away from Intermediaries.” The simple answer to his argument is that power abhors a vacuum - and in this case, the vacuum has been filled by the same people who had the power in the previous world. Despite the terrors expressed by some commentators - see eg. David Shenk, Data Smog (1998) - it is relatively easy for listeners to deal with the “glut” of potential customers for their time by simply allowing filters to govern the content they accept. Volokh himself, in fact, foreshadows this credibility gap: “But when speakers can communicate to the public directly, it's possible their speech will be less trustworthy.” id at 1837. It is easy to criticize a writer three years ago in hindsight, but one wonders where articles published only a few months ago get their information. See eg. Kathleen Sullivan, First Amendment Intermediaries in the Age of Cyberspace, 45 UCLA L. Rev. 1653 (1998). (limiting the discussion of new “speech intermediaries” on the internet to internet service providers and similar code-based censorship without addressing the vital role of third party credibility judges). The narrowness of Sullivan’s discussion limits her analysis. For example, she claims that “the tacit assumption behind Brandenburg v. Ohio and New York Times v. Sullivan that the incidence of incitement and libel is likely to be controlled as a practical matter by speech intermediaries” is no longer applicable on the internet. However, this ignores the fact that incitement and libel can now be controlled by the unwillingness of internet readers to accept information and advocacy not vetted by such filters.
9. Internet users have devised a number of ways to judge the credibility of communication on the internet. One person interviewed for a “scam protection” site recommends judging the quality of a page based on the credibility of the pages linking to them. This, in addition to being somewhat useless, because the credibility and judgment of the linking page must then be judged, is also a means of perpetrating the “lock-in” effects of ideas. It can be compared to the network effects idea in economics: once a group of credible sites link to each other, they bolster each other’s perceived credibility relative to unlinked sites. At the same time, the situation of unlinked sites falls into a viscous circle: the unlinked sites become more difficult to find as the number of linked sites increase to occupy the attention of a reader. As a result, it is less likely that this potentially good information may be discovered and linked. See Scambusters on Y2K <
http://www.scambusters.com/Scambusters26.html> (visited 12-22-98)While the “linking” situation is usually considered a problem of getting eyeballs rather than gaining credibility, for any solution to work, both eyeballs and credibility must be provided. This is why public “sidewalks in cyberspace” are doomed to fail. The government, by creating, for example, “social search engines” to reach dissident information would either have to indiscriminately catalog every site on the net, in which case it would be nothing more than a publicly owned altavista, or it would have to prefer certain sites over others, providing this credibility by government endorsement. Obviously, however, government endorsed dissident groups quickly cease to be dissident groups. This is the core reason why the government’s role should be limited to removing harmful laws and giving poor people access and training. Anything else introduces distortion into the “marketplace” for audiences, and leaves an opening for questionable public motives.
10. Strong businesses and other monied interests, on the other hand, have sophisticated tools to identify their potential audiences. One example is SRI consulting <
http://www.sriconsulting.com/> (visited 12-21-98), a business consulting firm who’s parent company claims to have been one of the first two nodes of ARPANET, after UCLA <http://www.sriconsulting.com/sri/sri1C.html> (visited 12-21-98). SRI offers a package of internet services, including “consumer acceptance of technology” studies <http://future.sri.com/vals/cat.method.html> (visited 12-21-98) to help businesses determine their precise markets. For anyone interested in this issue, their “vals” service should be worth exploring. To avoid spending the hours clicking that I did, here is a good starting point: <http://future.sri.com:80/vals/ivals.segs.html> (visited 12-21-98). This describes the “types” on the internet. Note also that you can take a survey to determine your “type”, but this will in all probability include your information in their database. See also Firefly <http://www.ffly.com> (visited 12-21-98).11. See eg. <
http://www.compusa.com/CompUSA/CompUSAPC/pc_default.asp> (visited 11-98) Note also that a move to “network computers” will, while lowering the cost of access to the internet, will probably be more harmful to minority viewpoints than beneficial. Networks supporting the network computers have to be owned by someone - most likely corporations with their own interests in regulating the content of information presented to consumers. So, for example, if it became profitable to market a network with “child protection” censorware products built in at the network level (with considerably less control to the user), it would quickly defeat many of the diversity advantages from making computers more widely available.12. See generally Lande, Wealth Transfers as the Original and Primary Concern of Antitrust: The Efficiency Interpretation Challenged, 34 HASTINGS L.J. 65 (1982) (arguing that monopolies are dangerous because they effect a wealth transfer from the less powerful consumers to the more powerful producers) if consumer surplus is a matter of “right”, when the product is audiences for ideas, the government has an extremely strong interest in breaking the portal oligopoly.
13. Monty Python’s Flying Circus: Spam (BBC)
14. For example, a column on one of the sites within the “Pathfinder Network” <
http://www.pathfinder.com> (visited 12-21-98), because it implies some sort of reintermediation of credibility, has more inherent credibility than a web page on Geocities <http://www.geocities.com> (visited 12-21-98), a free home page provider that has no “standards.” This is just one of many examples of the parallelism between the false promise of economic “disintermediation” and the false promise of noneconomic filter removal.15. See eg. “FAQ for beginning writers” <
http://www.sfwa.org/writing/faqs.htm> (visited 12-21-98) suggesting that publishers do not accept online submissions because “the consensus among editors has been that the process of manuscript submission works fine for them, and they're not interested in changing it... the publishing industry was designed to turn out profitable and high-quality books, not to be convenient for writers.”16. See eg. Yahoo Directory, “internet frauds” <
http://dir.yahoo.com/Computers_and_Internet/Internet/Business_and_Economics/Fraud/> (visited 12-21-98), Scambusters “Scam Check” <http://www.scambusters.com/scamcheck.html> (visited 12-21-98) (This is the same scambusters that accepts advertising from groups that would be recognized as shifty even off the internet: “7 internet success strategies” <http://www.successplace.com/iba/index.html> (visited 12-21-98))17. See eg. Usenet group <alt.usenet.kooks>, “Howling at Net.kooks” <'
http://www.netizen.org/Howling/Kooks/> (visited 12-21-98). The very titles of these forums ignore the reality that people who are “kooks” on the internet are also “kooks” off the internet. This erroneously implies that “kookery” is somehow more encouraged by the internet, and contributes to a general distrust of the medium. (Sanity is not medium-dependent.) The ignorance of this seemingly obvious point is a result of credibility disintermediation. Were there no need to independently judge speaker credibility, there would be no special “kook” warning. However it comes about, it effectively reduces the credibility of the entire net by casting it as the sole place where one may find “kooks.”18. See eg. “AOL’s Campaign Against Junk E-mail” <
http://legal.web.aol.com/email/jeaolcam/index.html> (visited 12-21-98), Bigfoot <http://www.bigfoot.com> (visited 12-21-98)19. See eg. summary of proposed bill H.R. 1748 “Netizens Protection act of 1997” <
http://thomas.loc.gov/cgi-bin/bdquery/z?d105:HR01748:@@@L|/bss/d105query.html>> See also <http://thomas.loc.gov/cgi-bin/query/D?r105:1:./temp/~r105XN6iBV:e371:> (visited 12-21-98) (there does not seem to be any better way to cite this - however, they may all be reached from AOL, id)20. Paradoxically, this will not be improved as the development of the internet moves toward non-text uses. If the internet is going toward more bandwith, more hardware intensive applications, this will further disadvantage small speakers. Small speakers have no need for additional bandwidth - a political manifesto can be communicated as effectively through text on usenet as through full motion video. Extra functionality favors those speakers who have the resources to make use of it - much like competition for advertising, it raises the marginal cost of an eyeball, because speakers who can afford to produce things like streaming video will attract more viewers. This will put smaller speakers at yet another competitive disadvantage.
See eg. Real Player <
http://www.real.com> (visited 12-21-98) (once merely an internet audio player, now offering streaming audio and video, specially designed “channels”, “bookmarks” and other “large” features favoring stronger players who can afford to cut deals with Real to feature their communication), Pointcast <http://www.pointcast.com> (visited 12-21-98) (more high bandwidth, high commercialization technology), and, astonishingly enough, Neoplanet <http://www.neoplanet.com/> (visited 12-21-98), a browser apparently building a commercially sponsored portal right into the software. This last comes perilously close to a complete private ownership of the internet.21. <
http://www.nytimes.com> (visited 12-21-98)22. Costing our poor speaker an additional $995. See <
http://www.adobe.com/prodindex/photoshop/prodinfo.html> (visited 12-21-98)23. The Clash, Know Your Rights, on Combat Rock (1982)
24. See eg. Compuserve Inc. v. Patterson, 89 F.3d 1257 (6th Cir.1996) (purchasing compuserve account and selling shareware over compuserve sufficient to establish personal jurisdiction in Ohio), United States v. Thomas, 74 F.3d 701, 706-07 (6th Cir.1996) (transfer of pornography “across state lines” over internet sufficient to subject defendant to personal jurisdiction.), Zippo Manufacturing v. Zippo Dot Com, 952 F.Supp. 1119 (W.D. Penn, 1997), Inset Systems Inc. v. Instruction Set Inc., 937 F. Supp 161 (D. Conn 1996), Heroes, Inc. v. Heroes Found., 958 F.Supp. 1 (D.D.C.1996) (web page, combined with newspaper ad and accessible toll free number establishing personal jurisdiction). But see Bensusan Restaurant Corp. v. King, 937 F.Supp. 295 (S.D.N.Y.1996) (web page is merely stream of commerce, and insufficient to exercise personal jurisdiction alone), McDonough v. Fallon McElligott, Inc., 40 U.S.P.Q.2d 1826, 1996 WL 753991, *3 (S.D.Cal.1996), Smith v. Hobby Lobby Stores, 968 F.Supp. 1356 (W.D.Ark.1997), Scherr v. Abrahams, 1998 WL 299678 (N.D. Ill unpublished opinion holding that Massachusetts defendant with web page accessible from Illinois and e-mailing list including Illinois citizens not subject to Illinois personal jurisdiction), > Hearst Corp. v. Goldberger, 1997 WL 97097 (S.D.N.Y.1997). Until the Supreme Court is heard on this issue, it is unlikely that the field will be any less muddled. Unfortunately, the cases holding no jurisdiction seem to be predominantly unreported, with consequently lessened precedental value.
25. See eg. Compuserve, Id. Even though compuserve is a national ISP with users in every state, and Patterson was a single individual marketing software from his home, the court still had no qualms in basing Ohio jurisdiction on the commercial transactions between Compuserve and Patterson. In the words of the court
He subscribed to CompuServe, and then he entered into the Shareware Registration Agreement when he loaded his software onto the CompuServe system for others to use and, perhaps, purchase. Once Patterson had done those two things, he was on notice that he had made contracts, to be governed by Ohio law, with an Ohio-based company. Then, he repeatedly sent his computer software, via electronic links, to the CompuServe system in Ohio, and he advertised that software on the CompuServe system. Moreover, he initiated the events that led to the filing of this suit by making demands of CompuServe via electronic and regular mail messages. (id at 1264)
Apparently, in the view of the sixth circuit, clicking “agree”, sending e-mail, and uploading files to an ISP establishes personal jurisdiction. This though, looking at the situation realistically, it is unlikely that clicking on parts of an adhesive contract mentioning the state of Ohio served as notice to the defendant that he was taking advantage of the state of Ohio. The main facts that the court seem to rely on to establish “transacting business in ohio” are the uploading of files into a Compuserve server, and the subsequent downloading by users. This basis is highly questionable. First, there is no real reason to locate the software in Ohio. In effect, Ohio is merely a temporary storage area, used for transmission to users in a variety of states. This can be analogized to a physical transaction. If a business ships goods to a number of states through a national freight company, knowing that the freight company will store the goods in their Ohio warehouse. This point of view may provide a radically different result (see eg. Health Communications Inc. v. Mariner Corporation, 860 F.2d 460 (DC Cir, 1988)) from the 6th circuit’s perspective, characterizing “Patterson's relationship with CompuServe as a software provider and marketer that is crucial to this case.” The important distinction in this case, then, is between “ISP as active agent” and “ISP as faceless intermediary, just another computer on the way to the audience.” While normally it is in the interests of the ISP to minimize its role in the provision of computer services (See eg. zeran), in cases where the ISP is filing suit against an out-of-state defendant, it is in the ISP’s interest to represent their services as fully as possible. To be consistent, however, they must choose one perspective to present their claims.
26. Maritz, Inc. v. Cybergold, Inc., 947 F.Supp. 1328 (E.D.Mo.1996). While a commercial activity case, the court introduced a “passivity” test, arguing that Cybergold’s site was not passive because, unlike “snail mail”, “[w]ith CyberGold's website, CyberGold automatically and indiscriminately responds to each and every internet user who accesses its website. Through its website, CyberGold has consciously decided to transmit advertising information to all internet users, knowing that such information will be transmitted globally”. Apparently, CyberGold’s web site collected a mailing list, and, as the above quote implies, set up an auto-responder to reply to each customer who chose to put themselves on their list. By this logic, every web site may as well be subject to personal jurisdiction everywhere. The only functional difference between an auto-responder, where a visitor sends an e-mail and gets an automatic response, and a web site visit, where a visitor sends a http request and gets an automatic response, is the method of transmission. As such, this decision, while proposing to respect a passivity requirement, really implies unlimited jurisdiction for the net.
27. Refusal to submit can have dire consequences. For example, the “cult awareness network” is now owned by the “church” of scientology after bankruptcy resulting from litigation by the same “church”.
28. See eg. Planned Parenthood Fed. of America v. Bucci, 1997 WL 133313 (S.D.N.Y. 1997) (Planned Parenthood lawsuit over plannedparenthood.com domain name.) It is difficult to see how this could enter trademark law at all, as planned parenthood is not generally considered to be offering “goods or services” for which there needs to be protection against consumer confusion. If simple free information is considered a good or service, the law of trademark becomes the law of misrepresentation. It is also difficult to see why Planned Parenthood would object to this use of their name in a critical domain. Any debate about a controversial issue using the name of a major player must increase the viewers wishing to see the actual opinions of the major player, leading them to seek the actual Planned Parenthood page out.
29. See eg. Religious Technology Center v. Netcom On-Line Communication Services, Inc 923 F. Supp 1231 (1995) (copyright suit over “church” of scientology documents with strong social importance.)
30. Or worse. One thing that strikes the mind about "how the net is different" is that copyright is enforced differently on the net. In meatspace, to enforce your copyright, you file a lawsuit against the infringer asking for an injunction/damages. In cyberspace, you send an e-mail to the infringer's ISP and get the offending speech taken down. In effect, this is more than a cost to the minority speaker, it is actually a TRANSFER of the costs from the strong party to the weak party. Where before, the person claiming a copyright violation had to first take the expensive formal legal steps in order to stop speech, now the speaker has to take that cost first, to regain the right to speak. This situation is even worse when intellectual property is protected by code. Protected by law, the costs come ex post to the enforcing party. Protected by informal “ask the isp,” the costs come ex post to the using party. Protected by code, the costs come ex ante to the using party, creating a threshold which must be passed in order to even get to the point where the use need be defended. Furthermore, the legal system is not even available in this situation - even in the informal protection scheme, the user always has the option of finding another ISP or perhaps filing suit against his current ISP for breach of contract. Unless an affirmative legal right of fair use is to be created, this is irremediable. Even if an affirmative legal right of fair use is born, though, the costs are still very high ex ante - it is just a choice between the cost to sue or the cost to crack.
31. One of the more amusing examples of the latter variety comes from the Software Publisher’s association. They provide a “button” to use on websites to show support for their antipiracy campaign <
http://www.spa.org/piracy/button.htm> (visited 12-15-98). Along with the button is a contract regulating the terms of use of that button, basically taking away fair use rights, but reciting assent as “downloading, copying or otherwise reproducing the SPA BUTTON." Since the SPA must take the position that loading into RAM is a copy (otherwise they could not prevent software being used on a network under a single user license), they are placed in thw position of claiming that a mere view of the button - even on someone else’s web page, and inadvertent - is sufficient to assent to a contract taking away fair use rights.32. Even more insidious perhaps is the example id of contracts removing fair use rights. The contract for the SPA button imposes the following terms: "The SPA BUTTON is licensed, not sold. SPA grants you a non-exclusive license to reproduce the SPA BUTTON...[uses]...You agree not to make any other uses of the SPA BUTTON. You agree that you will not use the SPA BUTTON with any other logo or title, nor will you incorporate the SPA BUTTON in any other design, or in any way that alters, distorts, mutilate, or otherwise modify, or in any way make a derogatory use..." Unquestionably, this contract takes away parody rights (derogatory use) protected by the fair use section of the copyright act (17 U.S.C. sec 107). See eg. Campbell v. Acuff-Rose Music, 114 S.Ct 1164 (1994). Given that, it is highly questionably that such a contract could even be enforced. If the user downloads the SPA button solely to parody it (for example, changing “report software piracy” to “inform on your family” to highlight the fact that the SPA advocates action normally considered socially harmful) they have not done anything beyond what they already were privileged to do by law. It is difficult, in such a situation, to justify calling the mere fact that the user could have used it to promote the SPA “consideration.” There is no apparent benefit to the user from this additional unwanted right, and no apparent detriment to the SPA from granting the right to promote it’s campaign - not even a peppercorn.
33. Perhaps the evils of bulk mailing (“spam”) should be ignored in the attempt to give internet users some avenue of targeting communication, without being subject to extralegal sanctions by aggressive powerful players.
34. The Commodores, Goin’ to the Bank
35. Note that this reasoning only applies to justifiable attacks. I am assuming here a suit without merit, or at least without moral force. If A attacks C and actually libels, violates the copyright of in some socially unacceptable manner, etc., the judge is just as able to make a utility calculation as anyone else, and set damages high enough to still deter other As from attacking C in the future.
36. <
http://www.disinfo.com>37. Easier to obtain because of the group nature of the action - more resources, plus on-site advertising, bringing in more money, which creates more promotion, for more users, bringing in more advertising dollars, etc.
38. see eg. Global Internet Liberty Coalition <
http://www.gilc.org>, Netaction <http://www.netaction.org>39. Unless they are willing to tolerate an address like http://www.geocities.com/CapitolHill/Senate/Chamber/PagesOffice/UnderDesk/7830238549, completely impossible to find and peppered with advertisements at all times.
40. Consumers would be on notice that trademark did not apply there, and that brand names in that space would bear no relation beyond the choice of the speaker to the goods or services branded. In effect, this would be an example of government (rather than dangerous private) “zoning”, placing players on notice that different rule sets apply in different locations. When the theoretical justification for these rule sets (for trademark, consumer confusion) is based on notice, this allows the rules to be abandoned. See generally David G. Post, Anarchy, State, and the Internet: An Essay on Law-Making in Cyberspace, 1995 J. Online L. 3, <
http://www.law.cornell.edu/jol/post.html> (arguing the inevitability of a “free market” in rule sets based on private zoning)41. This would also avoid the problems discussed in Dan L. Burk, Trademarks Along the Infobahn: A First Look at the Emerging Law of Cybermarks, 1 RICH. J.L. & TECH. 1 (Apr. 10, 1995) <
http://www.urich.edu/~jolt/v1i1/burk.html>' with online misrepresentation.42. But which would be facilitated by allowing real diversity on the internet. There is no point in internet education if the only accessible resources are exactly the same as what the teachers and textbooks say. This really IS a different paper, and one I want to write at some point soon. Simply for the purposes of this paper, however, I will point out that the need for diversity of opinions at all, and especially in education, assumes a view of education very different from post-industrial revolution uses of the public school system. Rather than free universal education being merely a way for the economy to produce skilled workers, the “diversity in education is good” viewpoint sees education as a source of personal and social growth. If one only wishes public education to support industry, then there is little reason for the students to have anything available except the “stronger” viewpoints, and this entire paper can be sent to the compost heap right now.
43. These suggestions are mainly directed at the US government, not because the US is the only government important on the internet, but because net culture, politics and economics are currently dominated by US voices. In addition, it is undoubtedly easier to get the US government to change policies, than, say, China. Finally, your devoted servant the author is simply more familiar with the US than with other countries. One step that IS necessary for any of these suggestions to be at all effective, however, is for some international agreement to find some way to divide jurisdiction over the net. That, again, is a completely different paper.
44. See eg. Planned Parenthood, supra note 28.
45. This is perfectly within their power. Even when congress has not explicitly preempted state law, the courts have sometimes held that commerce clause legislation effects a preemption. See eg. Paul D. Carrington, Regulating Dispute Resolution Provisions in Adhesion Contracts, 35 Harv. J. on Legis. 225 (1998) (discussing the use of the federal arbitration act to validate dispute resolution provisions invalid under state contract law).
46. It must be noted that this is a double edged sword. To the extent the courts are used as forces for the strong to exert power over the weak (most cases in the net - since the net is earliest resorted to by people who need the advantages it provides over meatspace), this will properly limit the costs of the small parties. To the extent, however, that the courts are a means for weak parties to sue strong ones (eg. censored cites suing filtering software manufacturers), some possibility for justice is lost. However, the net benefit is clearly to those parties we want to protect. More powerful players are more likely to be subject to wide jurisdiction in a pre-net analysis, simply because having money and power often requires one to leave one’s state.
47. for a general discussion of IP rights as affected by digital technology, see Neil Netanel, Copyright and a Democratic Civil Society, 106 Yale L.J. 283 (1996) (promoting a vague balance between incentives and the public domain for copyright on the internet, without considering the cost of litigation problem)
48. This may entail eliminating antidemocratic doctrines such as tarnishment in trademark law. See eg. 15 U.S.C. sec.1125(c)
49. and a certain risk that parents opposing such things will inadvertently allow them to slip in the hands of their children.
50. Speaking of paying: it is obvious that those things would not exist if there was no demand for them. Rather than apply poorly targeted tools, like legislation and commercial software, to prevent “indecency” from reaching children, society could stop professional pornographers with less collateral damage simply by providing greater opportunities elsewhere. If pornography were not one of the few ways that weaker parties could make any money off the internet (because the most powerful players generally are not interested, reducing the level [quality. not quantity] of competition), it would not be so available.
51. For a further discussion (if sometimes evangelical) of the borders of the first amendment, see Eric M. Freedman, A Lot More Comes Into Focus When You Remove the Lens Cap: Why Proliferating New Communications Technologies Make it Particularly Urgent for the Supreme Court to Abandon its Inside-Out Approach to Freedom of Speech and Bring Obscenity, Fighting Words, and Group Libel Within the First Amendment, 81 Iowa L. Rev. 883 (1996). (arguing that the realm of free speech should be greatly expanded to prevent attacks at the border.) This sort of argument - that the current lack of protection for some categories of speech risks interested parties limiting protection at the borders (eg. “politically incorrect” speech) can be applied equally well here. At those same borders, the plausibility of a suit increases, and the length before it is defeated, along with the cost of defense, increase for weaker parties.
52. Suggesting a change in the attitudes of American parents to the scope of information their children have access to is well beyond the scope of this paper.
53. Or would have the realistic and continuing opportunity and the technical ability to choose to not censor such sites.
54. For example, if a site censored
http://www.mightyblack.net (to my knowledge, no such site exists), when a user attempts to visit the site (or executes a search that would normally retrieve it), the refusal should read “This site blocked by OppressBot (tm) for: extremism” rather than “This site blocked by OppressBot(tm)”, “document contains no data” or, worst of all, a simple absence from the results of a search engine. This would allow a parent to actually choose to view the “extremism”, being made aware that the site espouses “black power” political views, rather than African-American pornography. This would also be to the advantage of the proxy manufacturers, as they would not be so vulnerable to defamation lawsuits from groups claiming that, because most people only expect filtering software to block pornography, they were associated with unsavory content.55. As it currently stands, a speaker on the internet must jump through a lot of hoops, and have a certain amount of technical knowledge, to ensure complete anonymity. For posting on the web, she must know what a proxy server is, and how to use one. For usenet and e-mail, he must be able to find and use a trustworthy anonymous remailer, or obscure e-mail header information well enough to evade detection. She must also be able to completely delete copies of posted e-mail, cached web pages, etc. off of local drives, networks, backups, etc.
56. it is important to build protections into this proposed system for “fair use” of private information. If necessary, a power differential requirement could be imposed through legislation: a right of action based on privacy violation could be created for less powerful speakers against more powerful speakers. If there were some way to make that distinction in a statute, it would be useful to still allow commentary on the “private affairs of socially relevant parties. For example, a private person could freely invade the privacy of the New York Times, a powerful corporation, to expose abuses (or complain about employment policies), but not necessarily vice versa. Likewise, the NYT could freely invade the “privacy” of public officials, but the public officials need not feel free to search the NYT’s offices.
57. Although the minority speaker is the person we are trying to protect here, I assume that all speakers will prefer anonymity. This is partly the flip side of the “credibility of the medium” issue discussed above: there is little enough trust in people on the internet (eg. the “stalker” fear) that there is little likelihood that the average person, if educated (that should be an additional proposal for the gov’t. I’ll stick it in under subsidy maybe later) will choose an ISP preventing anonymity from one allowing or encouraging it.